While unauthorized access to computer systems is generally illegal and considered hacking, there are specific situations where hacking is legal and even encouraged. This is where it is termed “ethical hacking”. Ethical hacking involves authorized professionals, commonly referred to as ethical hackers or penetration testers, who perform hacking activities with the explicit permission of the system owner.
It’s important to note that while ethical hacking is legal, unauthorized hacking, also known as malicious or black-hat hacking, is illegal in most jurisdictions. Unauthorized access to computer systems, theft of data, and disruption of services are criminal activities that can lead to severe legal consequences.
According to CyberGhost ethical hackers are the future of cybersecurity, as cybercrime has increased by 600% during the COVID-19 pandemic. So, in this blog, we will understand the phases of ethical hacking, the importance of ethical hackers for cybersecurity, the types of ethical hackers, and how ethical hackers differ from unethical hackers.
Ethical Hacking & Ethical Hackers
Ethical hacking, also known as penetration testing or white-hat hacking, refers to the practice of identifying vulnerabilities and weaknesses in computer systems, networks, or software applications. Ethical hackers, also called security researchers or penetration testers, are authorized professionals who perform these activities with the permission and knowledge of the system owner.
These ethical hackers use their skills
- to identify vulnerabilities
- to test security measures
- to help improve the overall security of systems and networks
They follow strict guidelines and adhere to legal and ethical boundaries during their assessments. Ethical hacking is conducted in a controlled environment, often as part of proactive security testing or in response to a specific request from an organization or individual seeking to enhance their security.
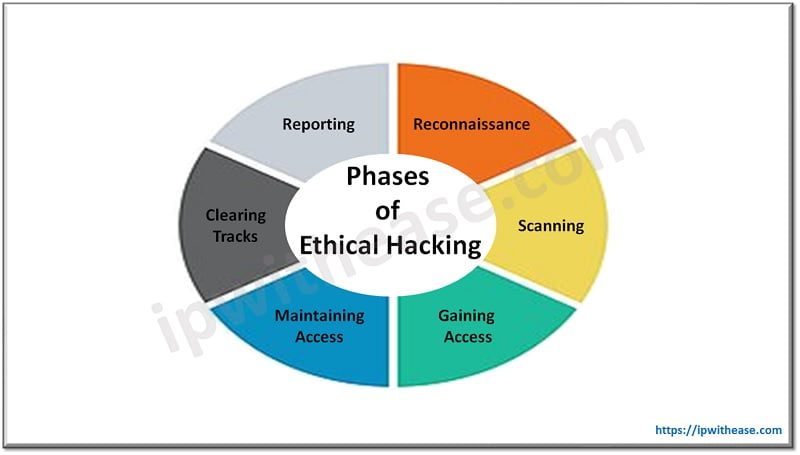
Phases of Ethical Hacking
There are 6 phases of Ethical hacking:
- Reconnaissance: Reconnaissance is a vital phase in the process of hacking, where the attacker collects information about the target system.
- Scanning: The hacker makes an attempt to find vulnerabilities within the target system.
- Gaining Access: The hacker attempts to hack into the system using the vulnerabilities identified during the scanning phase.
- Maintaining Access: It is the crucial phase as during this phase, the hackers insert different types of backdoors and payloads onto the targeted system.
- Clearing Tracks: This phase is considered unethical as the hacker attempts to erase all logs of their actions during the hacking process. Even those who practice ethical hacking must carry out this phase to showcase the methods used by malicious hackers.
- Reporting: The ethical hacker submits a comprehensive report that includes all the discoveries made, the techniques employed, and the vulnerabilities exposed. It is the final phase.
Role of Ethical Hackers in Cybersecurity
Ethical hackers play a crucial role in cybersecurity for several reasons:
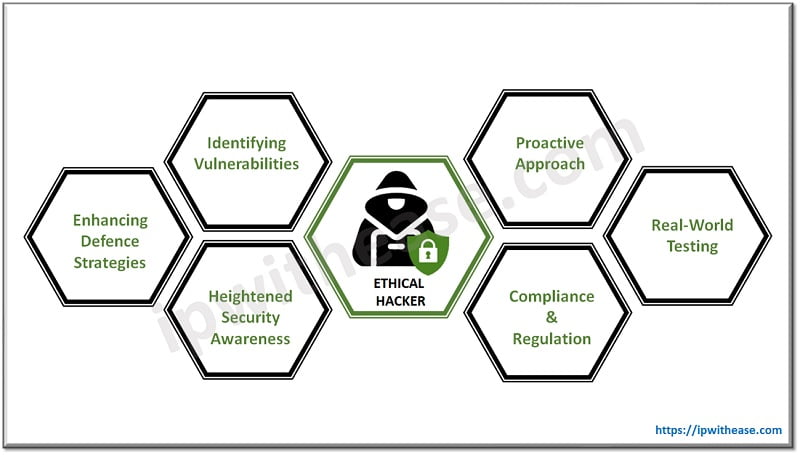
Identifying Vulnerabilities: Ethical hackers have the skills and knowledge to identify vulnerabilities and weaknesses in systems and networks. By actively testing and probing for vulnerabilities, they can uncover security flaws that may otherwise go unnoticed. This allows organizations to address these weaknesses before malicious hackers can exploit them.
Proactive Approach: Ethical hackers take a proactive approach to cybersecurity. Rather than waiting for a security breach or incident to occur, they actively search for vulnerabilities and help organizations strengthen their defences. By conducting regular security assessments and penetration testing, ethical hackers help prevent potential cyberattacks.
Enhancing Defence Strategies: The insights and recommendations provided by ethical hackers enable organizations to enhance their defence strategies. Ethical hackers not only identify vulnerabilities but also offer guidance on how to mitigate these risks. This may involve implementing security patches, configuring firewalls, improving access controls, or strengthening encryption mechanisms.
Real-World Testing: Ethical hackers simulate real-world attack scenarios to assess the effectiveness of security controls and measures. This type of testing provides organizations with valuable insights into how their systems and networks would withstand actual attacks. It helps identify potential weaknesses and ensures that security measures are robust and effective.
Heightened Security Awareness: Through their work, ethical hackers raise awareness about the importance of cybersecurity. Their findings and reports often highlight the potential risks and consequences of inadequate security measures. This helps organizations and individuals understand the need for robust security practices and encourages them to take proactive steps to protect their systems and data.
Compliance and Regulation: Many industries and sectors have specific compliance requirements and regulations related to cybersecurity. Ethical hackers assist organizations in meeting these requirements by identifying vulnerabilities and helping them implement the necessary security controls. This ensures that organizations remain compliant with relevant laws and regulations.
Types of Ethical Hackers
There are different types of ethical hackers based on their areas of expertise and the specific tasks they perform during security assessments. Here are a few common types:
- White Hat Hackers: White hat hackers are ethical hackers who conduct authorized security assessments, penetration testing, and vulnerability assessments. They work to identify vulnerabilities and weaknesses in systems and networks and provide recommendations for remediation.
- Black Box Testers: Black box testers are ethical hackers who perform assessments without prior knowledge of the system being tested. They simulate real-world scenarios where they have no prior information about the target system’s architecture, design, or internal workings. This approach helps assess the system’s security from an external perspective.
- Grey Box Testers: Grey box testers have partial knowledge of the system being tested. They are typically provided with limited information about the system, such as its architecture, network diagrams, or application details. This approach allows them to focus their efforts on specific areas of concern while still simulating a partially informed attacker.
- Network Security Specialists: These ethical hackers specialize in assessing the security of networks, including routers, switches, firewalls, and other network infrastructure components. They identify vulnerabilities, misconfigurations, and potential weaknesses that could be exploited by attackers.
- Web Application Security Specialists: Web application security specialists focus on assessing the security of web-based applications. They use various techniques to identify vulnerabilities such as injection attacks, cross-site scripting (XSS), cross-site request forgery (CSRF), and insecure authentication or authorization mechanisms.
- Social Engineers: Social engineers are ethical hackers who specialize in exploiting human psychology and manipulating individuals to gain unauthorized access to systems or sensitive information. They use techniques like phishing, pretexting, or impersonation to deceive and trick individuals into revealing confidential information.
Ethical hacker vs Unethical hacker
The below given differences highlight the contrasting motives, actions, and ethical considerations between ethical hackers and unethical hackers.
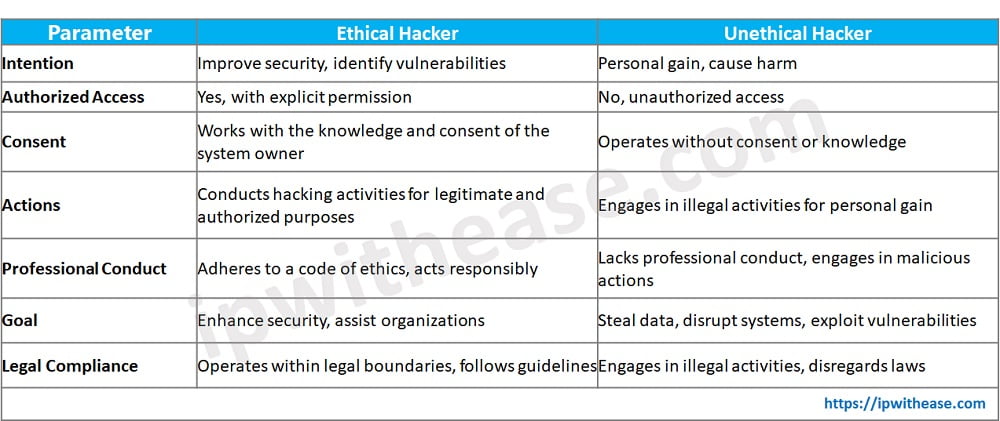
Download the comparison table: ethical hackers vs unethical hackers
Final Words
Ethical hackers are crucial for cybersecurity as they proactively identify vulnerabilities and weaknesses in computer systems, helping organizations fortify their defences before malicious hackers exploit them. Their expertise and insights contribute to the development of robust security measures, safeguarding sensitive data and preventing potential cyber threats.
Continue Reading:
What Is Threat Hunting? Everything You Want to Know
Honeypot vs Honeynet: Complete Guide
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.