Table of Contents
IPS is a key security component in a networking environment and stands for Intrusion Prevention System. IPS works on the network perimeter and scans network traffic flows to detect and prevent vulnerability exploits.
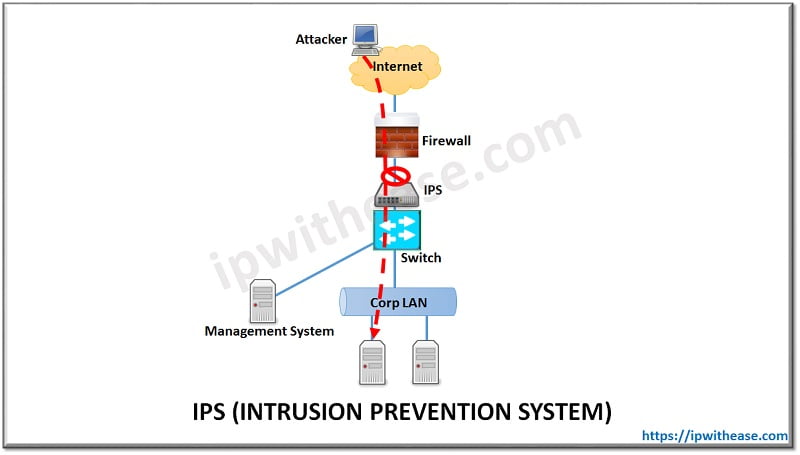
Intrusion prevention scans all network traffic and takes responsive action i.e. either block or remediate flows with malicious traffic. In general scenarios, IPS uses a combination of traffic and file signatures and heuristic analysis of flows.
IPS follows a procedural approach to address action against attack as shared below –
- Monitors traffic flow
- Identify malicious traffic
- Takes corrective action to protect the network
There are a number of different threats that an IPS is used to prevent –
- Denial of Service (DoS) attack
- Distributed Denial of Service (DDoS) attack
- Exploits
- Viruses
- Worms
- Backdoor
Related- DOS vs DDOS
IPS Types
IPS uses different type of approaches to protect the network from unauthorized access. These are –
- Signature-Based – This approach works by referring to predefined signatures of well-known network threats, where IPS matches one of the traffic signatures or patterns and therefore takes necessary action.
- Anomaly-Based – This type of approach monitors the traffic for any event outside the normal or acceptable behavior on the network. In thi case, the system blocks access to the target host immediately.
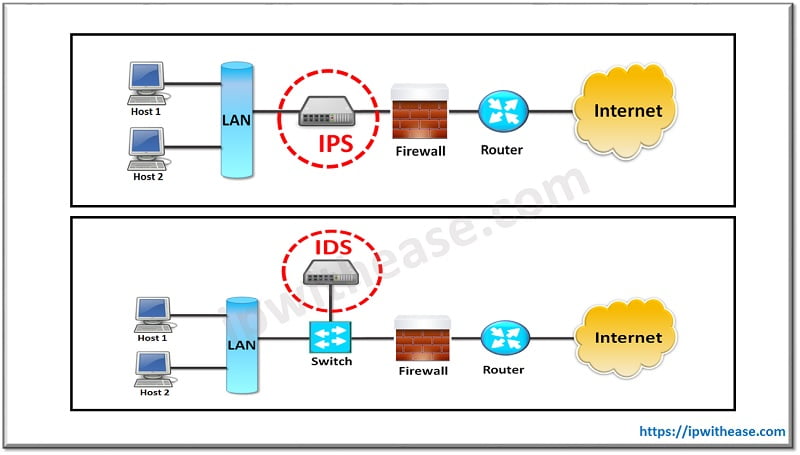
IDS vs IPS
Many times, IPS is compared to its close relative IDS. IDS stands for Intrusion Detection System which is a passive system and monitors/scans traffic and only reports on threats and attacks. Interestingly, most of IPS systems can also function as IDS solution.One major difference between IDS and IPS is placement in the network. IDS does not sit inline to traffic flow and just passively watches the traffic traversing the network.In this case the traffic copy is sent to IDS by mechanism of port span or by deploying network TAP. On the other hand, IPS sits inline in the network and all the traffic passes through it.
IDS and IPS also contrast in terms of action to be taken in the event of unauthorized traffic access. The former will not stop the traffic, albeit it sends alarm or alert to the responsible system for further action. The latter is more aggressive and immediately blocks the unauthorized traffic which it detects. An overhead which may be associated with IDS systems is the responsibility of taking action on each alarm generated by the system. This is because IDS cant take action on the threat and hence same needs to be owned by network or security admin.
Related – Cisco IPS/IDS Interview Questions
Comparison Table
Below are the key differences between IDS and IPS
| PARAMETER | IPS | IDS |
|---|---|---|
| Abbreviation for | Intrusion Prevention System | Intrusion Detection System |
| System Type | Active (monitor & automatically defend) and/ or passive | Passive (monitor and Notify) |
| Detection mechanism | Statistical anomaly based detection Signature detection: * Exploit-facing signatures * Vulnerability-facing signatures | Signature detection: * Exploit-facing signatures |
| Placement | Inline to data communication | Out of band from data communication |
| Anomaly response | Drop, alert or clean malicious traffic | Sends alarm/alert of detecting malicious traffic |
| Network performance impact | Slow down network performance due to delay caused by inline IPS processing | Does not impact network performance due to non-line deployment of IDS. |
| Benefits | Preferred by most organization since detection and prevention are automatically performed | Does not block legitimate traffic which might be blocked by IPS at times. |
Download the difference table here.
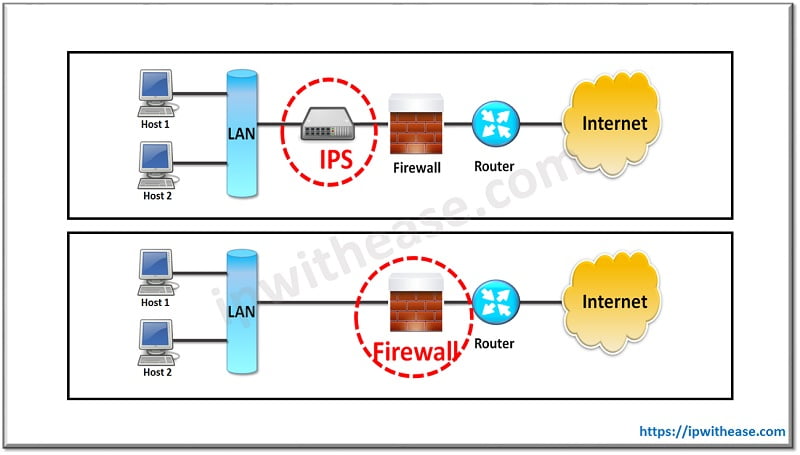
IPS vs Firewall
Firewall and IPS are 2 key components of a Security framework especially in scenarios where Data Center or Office for an enterprise are provisioned. There will be buffet of attacks from Internet and both these components are well equipped to defend against new/old attacks and vulnerabilities.
Firewall controls incoming and outgoing traffic based on preassigned security rules. It provisions a barrier between trusted internal network, semi trusted DMZ network and untrusted external network.
The main difference between firewall and IPS is that firewall performs actions such as blocking and filtering of traffic while an IPS detects and prevents the attack . Firewall primarily relies on source, destination IP addresses, protocol and port numbers. A firewall can deny any traffic that does not meet the configured rule-set. On the contrary, scenarios like IP packet not being of standard length, attacks like buffer overflow, DOS and DDOS attacks are ones that IPS can detect and take corrective action.
In terms of placement, Firewall is primarily the 1st line of defense against attack on perimeter. IPS comes in as next level of defense and is deployed after the Firewall.
Comparison Table
Below table summarizes the difference between IPS and Firewall
| PARAMETER | IPS | FIREWALL |
|---|---|---|
| Principle of working | 1st Analysis traffic, next detects/classifies it and then block malicious attack to network | Controls traffic based on port number, source/destination IP and protocol number |
| Traffic pattern analysis | Performed | Not Performed |
| Placement | Placed after the Firewall in Network | 1st Line of defense and provides parameter security |
| Key features | * Anomaly detection * Signature detection * Zero day attacks * Alert and monitoring | Stateful packet inspection Controls traffic based on protocol, port number and Ip address |
Download the difference table here.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj