Table of Contents
In the modern era, as we continue to move towards a digital age, we find ourselves participating in digital transactions and accessing sensitive information. As a result, cryptography is vital for safeguarding the privacy and security of our data. White-box cryptography is a specific field within cryptography that focuses on securely protecting cryptographic keys and algorithms. This ensures that even if attackers gain access to the software and attempt to analyze it, the data remains secure and protected.
What is Cryptography?
Cryptography, the practice of safeguarding communications, is both an artistic and scientific endeavor. Throughout history, it has played a crucial role in societies worldwide. Initially, its primary purpose was to safeguard classified information and maintain confidentiality in military endeavors and diplomatic exchanges. However, in modern times, cryptography has transformed into a fundamental element for protecting data in various domains like e-commerce, online banking, and secure communication, among others.
Cryptography encompasses the utilization of mathematical algorithms and keys to encode and decode information. It can be broadly categorized into two main divisions:
- Symmetric key cryptography involves the utilization of a single key for both encrypting and decrypting data.
- In asymmetric key cryptography, the encryption and decryption of data is achieved through the utilization of a pair of public and private keys.
Challenges Faced by Cryptography
- Key management: Managing cryptographic keys is a complex undertaking, as it involves the secure storage and proper management of these keys. The compromise of any key by an attacker could potentially undermine the entire encryption system.
- Side-channel attacks have the potential to exploit information that is unintentionally revealed by cryptographic systems. These attacks make use of various channels, such as power consumption, electromagnetic radiation, or timing information, in order to infer the secret key.
- Implementation attacks occur when cryptographic algorithms are not properly implemented, making them vulnerable. In such cases, attackers can exploit the weaknesses of poorly designed or implemented systems.
- Attacker with full access: The situation that poses the greatest challenge is when the attacker possesses complete control over the cryptographic software. In this case, they have the ability to thoroughly examine and exploit it. Consequently, safeguarding cryptographic keys and algorithms becomes an essential undertaking.
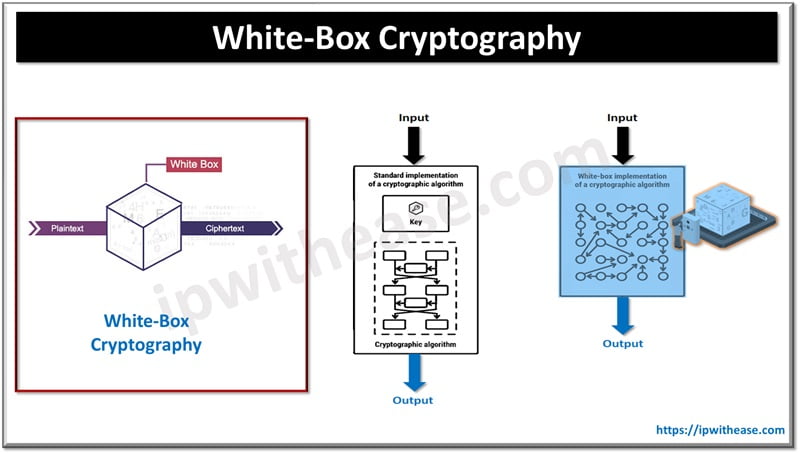
What is White-box Cryptography?
White-box cryptography is a specialized technique in the field of cryptography that concentrates on safeguarding both the cryptographic keys and software, even when the perpetrators have complete control over the software. This implies that the encryption keys are meticulously concealed within the software, making it exceedingly challenging for an attacker to retrieve them, even if they possess unlimited computational resources.
The primary objective of white-box cryptography is to ensure the security and privacy of cryptographic keys and data within any software setting. This presents a complex challenge, given its significant implications in various domains such as digital rights management (DRM), secure mobile payment systems, and software protection.
- DRM: DRM systems employ white-box cryptography as a means of safeguarding their content against unauthorized copying or alteration. This implementation offers numerous advantages, particularly within the entertainment sector where protecting intellectual property is of utmost importance.
- Secure transactions: White-box cryptography plays a crucial role in guaranteeing the security of transactions. Its purpose is to protect financial data, even if a device is compromised.
- Secure Software: Software vendors utilize white-box cryptography to safeguard their intellectual property and software data from potential threats.
Techniques in White-box Cryptography
To achieve the intended goal, white-box cryptography employs a variety of essential methods. Among the significant techniques utilized are:
Key Whitening
A secret key is incorporated multiple times within the software during the encryption process using this technique. This enhances the difficulty for attackers to identify the true key.
Permutation & Substitution
White-box cryptography makes use of mathematical algorithms such as permutation and substitution to conceal the data and make it harder to analyze.
Look-Up Tables
White-box cryptography employs lookup tables for the purpose of storing pre-calculated intermediate values, which are instrumental in facilitating subsequent cryptographic operations. These tables are typically safeguarded to prevent unauthorized access by potential attackers.
Virtual Machines
Certain white-box implementations execute cryptographic operations within a virtual machine, effectively segregating the execution environment from the remainder of the system. This imparts an additional level of security to the software.
White-box Cryptography: Challenges
- Proving the security of white-box cryptography poses a challenge since traditional cryptographic implementations offer mathematical proofs, unlike white-box cryptography. The security of white-box cryptography relies solely on the incomprehensibility of the data, which does not provide a strong guarantee of security.
- White-box cryptography faces a lack of established standards, posing a challenge for organizations when it comes to assessing and contrasting various solutions.
- Despite the claims of white-box cryptography being resistant to reverse engineering, skilled and persistent attackers with sufficient resources can still identify vulnerabilities and extract the encryption keys.
White-Box Cryptography: Continuously Evolving
To tackle the obstacles and restrictions, the realm of white-box cryptography is constantly advancing. Noteworthy patterns and advancements in this area encompass:
- Homomorphic Encryption: White-box cryptography is investigating the use of homomorphic encryption, a form of encryption that permits calculations on encrypted data, to facilitate secure data operations while maintaining data confidentiality.
- Formal Verification Methods: Scientists are currently engaged in the development of formal verification methods. These techniques aim to offer mathematical evidence of the security of white-box implementations, thereby increasing the reliability and trustworthiness of these solutions.
- Lightweight Implementations: There is a push to develop lightweight white-box cryptography solutions that have minimal impact on performance, making them ideal for devices with limited resources.
- Hybrid Model: By incorporating white-box cryptography alongside other cryptographic methods like Hardware Security Modules (HSMs), it is possible to bolster security measures without compromising performance.
- Standardization: There are ongoing initiatives to establish a standardized approach for white-box cryptography, aiming to create a universal framework for assessment and implementation.
Final Words
White-box cryptography tackles important security issues by safeguarding cryptographic keys and algorithms from malicious individuals who possess complete software access. Its use in digital rights management (DRM), mobile payments, and software protection plays a vital role in our ever-expanding digital landscape. Nevertheless, it encounters various challenges, including ensuring security, managing performance overhead, and the absence of standardized protocols.
As white-box cryptography advances, it has the capacity to safeguard sensitive information across various applications. However, its effectiveness relies on continuous endeavors to enhance security, performance, and standardization. Additionally, it must be adaptable to address emerging threats within the dynamic realm of cybersecurity.
Continue Reading:
White Box Testing vs Black Box Testing: A Detailed Analysis
ABOUT THE AUTHOR

I am here to share my knowledge and experience in the field of networking with the goal being – “The more you share, the more you learn.”
I am a biotechnologist by qualification and a Network Enthusiast by interest. I developed interest in networking being in the company of a passionate Network Professional, my husband.
I am a strong believer of the fact that “learning is a constant process of discovering yourself.”
– Rashmi Bhardwaj (Author/Editor)