Table of Contents
IDS, IPS, and firewalls are all security technologies designed to protect networks, but they differ in functionality and purpose. In this blog, we will focus on the detailed comparison between the three, i.e. Firewall vs IPS vs IDS that covers similarities as well as differences.
We have already discussed Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS) and Firewall in detail in our previous blogs.
Similarities between IDS, IPS and Firewall
Before moving on to the differences, we must understand the points of similarities between the 3 security technologies.
- All of them are designed to improve the security of a network by monitoring traffic and enforcing policies to protect against threats.
- All of them monitor incoming and outgoing network traffic. IDS and IPS focus on detecting or preventing intrusions, while firewalls manage traffic based on defined rules (e.g., blocking or allowing traffic).
- All three are typically deployed at key points in a network such as at the perimeter (e.g., between a trusted network and the internet), or within internal network segments to protect against lateral movement of threats.
- They all rely on a set of rules or signatures to identify malicious traffic or enforce security policies. For example:
IDS/IPS use signatures and anomaly detection techniques to recognize attacks or suspicious activities.
Firewalls use rules to allow or block traffic based on IP addresses, ports, and protocols.- These systems are often deployed together to form a comprehensive security solution. A firewall provides the first line of defense, while IDS and IPS provide deeper inspection and can detect more sophisticated threats that pass through the firewall.
- All of them are capable of detecting malicious behavior such as denial-of-service (DoS) attacks, unauthorized access attempts, and suspicious data transfers.
- They all generate logs and alerts based on events detected in network traffic, which can be integrated with SIEM tools for further analysis and incident response.
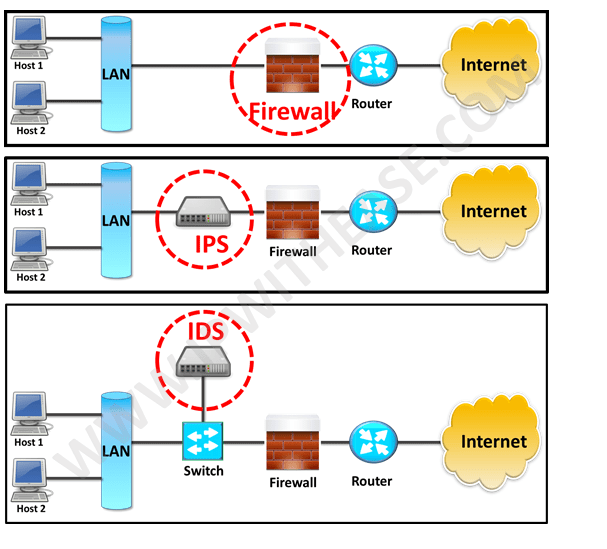
Differences: Firewall vs IPS vs IDS
A very common query asked by network and security administrators is the difference between Firewall, IPS and IDS.
All the 3 terms related to providing security to network and are considered essential components of a Network especially Data Center Network.
- The main difference being that firewall performs actions such as blocking and filtering of traffic while an IPS/IDS detects and alert a system administrator or prevent the attack as per configuration.
- A firewall allows traffic based on a set of rules configured. It relies on the source, the destination addresses, and the ports. A firewall can deny any traffic that does not meet the specific criteria.
- IDS is a passive device which watches packets of data traversing the network, comparing with signature patterns and setting off an alarm on detection on suspicious activity. On the contrary, IPS is an active device working in inline mode and prevent the attacks by blocking it.
Comparison Table
Furthermore, below table enumerates the difference between IDS, IPS and Firewall in detail:
| PARAMETER | FIREWALL | IPS | IDS |
|---|---|---|---|
| Abbreviation for | – | Intrusion Prevention System | Intrusion Detection System |
| Philosophy | Firewall is a network security device that filters incoming and outgoing network traffic based on predetermined rules | IPS is a device that inspects traffic, detects it, classifies and then proactively stops malicious traffic from attack. | An intrusion detection system (IDS) is a device or software application that monitors a traffic for malicious activity or policy violations and sends alert on detection. |
| Principle of working | Filters traffic based on IP address and port numbers | inspects real time traffic and looks for traffic patterns or signatures of attack and then prevents the attacks on detection | Detects real time traffic and looks for traffic patterns or signatures of attack and them generates alerts |
| Configuration mode | Layer 3 mode or transparent mode | Inline mode , generally being in layer 2 | Inline or as end host (via span) for monitoring and detection |
| Placement | Inline at the Perimeter of Network | Inline generally after Firewall | Non-Inline through port span (or via tap) |
| Traffic patterns | Not analyzed | Analyzed | Analyzed |
| Placement wrt each other | Should be 1st Line of defense | Should be placed after the Firewall device in network | Should be placed after firewall |
| Action on unauthorized traffic detection | Block the traffic | Preventing the traffic on Detection of anomaly | Alerts/alarms on detection of anomaly |
| Related terminologies | – Stateful packet filtering – permits and blocks traffic by port/protocol rules | – Anomaly based detection – Signature detection – Zero day attacks – Blocking the attack | – Anomaly based detection – Signature detection – Zero day attacks – Monitoring – Alarm |
Download the comparison table: Firewall vs IPS vs IDS
Download the IDS vs IPS vs Firewall detailed comparison in PDF format
Key Differences
- Firewalls primarily control access between trusted and untrusted networks using predefined rules.
- IDS detects and alerts on malicious activity but does not block traffic.
- IPS actively blocks malicious traffic and takes corrective actions in real-time.
Understanding these similarities and differences is crucial for designing a layered security strategy.
Watch Related Video for Better Understanding
Continue Reading
Cisco IPS/IDS Interview Questions
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj