Table of Contents:
Understanding an Attack Surface
The attack surface is the total number of all possible points, or attack paths, where an unauthorized entity can access a system and exploit/abstract data. It includes all the vulnerability and endpoints that can be misused by any intruder or attacker.
Now-a-days every organization tries to attain minimal attack surface to avoid any cyber-attack. Organizations must regularly monitor potential threats to attack surfaces and apply possible mitigation immediately.
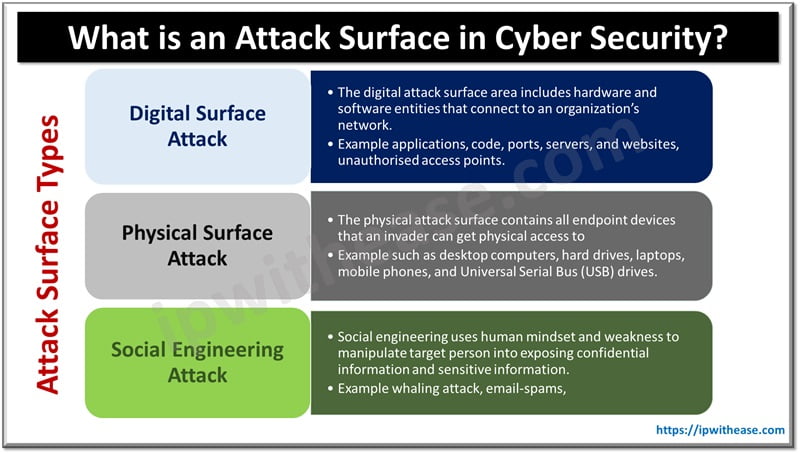
Attack Surface Types
Attack Surface further categorized into 3 parts:
Digital Surface Attack
- Digital Surface attacks include managed applications and assets such as known websites, internal servers that are managed by the organization itself.
- It also covers shadow IT which means those asset presents in the organization however not included in database or inventory. Such as forgotten web servers, sites, or any installed software.
- Third-party managed servers are also a weak point in an organization, it includes data centers, network infrastructure, application, and coding.
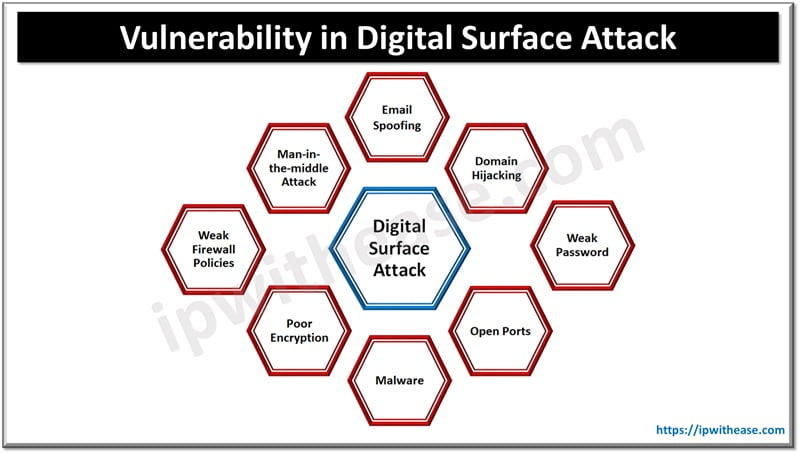
Parameters Responsible for Digital Surface Attack
Parameters which are responsible for Digital Surface Attack are:
- Data Breach and Data Leakage: Excess demand for cloud storage increases data breach and data leakage.
- Email Spoofing: Poor email security can lead to email hack or spoofing of the confidential data.
- Open ports in Network devices: open ports allow hackers to hack the gateway devices of any network.
- Man-in-the-Middle attack: Low security features in the network or software may invite man-in-the-middle attacks.
- Malware, poor passwords, breach in firewall policies are also the reason for Digital Surface attacks.
Physical Surface Attack
Whatever is accessible physically in an organization is vulnerable to Physical Surface attack. Example laptop, desktop, hard-drives, mobiles, printers, physical servers, firewalls and routers, Biometric machines, cameras, wi-fi.
What happens if any physical device is compromised?
- Attacker can easily get the access of interconnected devices of vulnerable system
- Attacker can scan sensitive and confidential data from the system
- Attacker can spread virus, malicious traffic in the network through the compromised device
- Attacker can destroy important information from the system
- Expose sensitive data to outside world which may impact organization’s reputation
- Delete access rights to the system so that authenticated user not able to access the machine
However, the most common way to get access to any physical device is through the people directly. That’s why we need to understand how Social Engineering Attack works that is used to gain information about any organization by exploiting social tactics.
Social Engineering Surface Attack
Social engineering is a technique used by hacker and cyber attackers to manipulate users to disclose or reveal confidential and sensitive information. The data obtained is then used to gain access to systems.
Commonly Used Methods of Social Engineering Attack
Some commonly used method of Social Engineering Attack are:
- Phishing: It is a way to trap victims through malicious links, fake emails, malware attacks on systems.
- Pharming: Cybercriminal sends malicious code to the victim and gains access to the user’s system.
- Piggybacking: Hacker (intruder) able to walk into the organization by following someone who has authorized access.
- Dumpster diving: Attackers try to get the data from company trash.
Surface Attack Management and Mitigation Plan
Attack surface management refers to observing, investigating, and mitigating vulnerability in terms of cyberthreat.
It contains all vulnerability assessments, security controls and security measures that go into mapping and protecting the attack surface, mitigating the chances of a successful attack.
Steps which are used to perform for risk mitigation and vulnerability assessment.
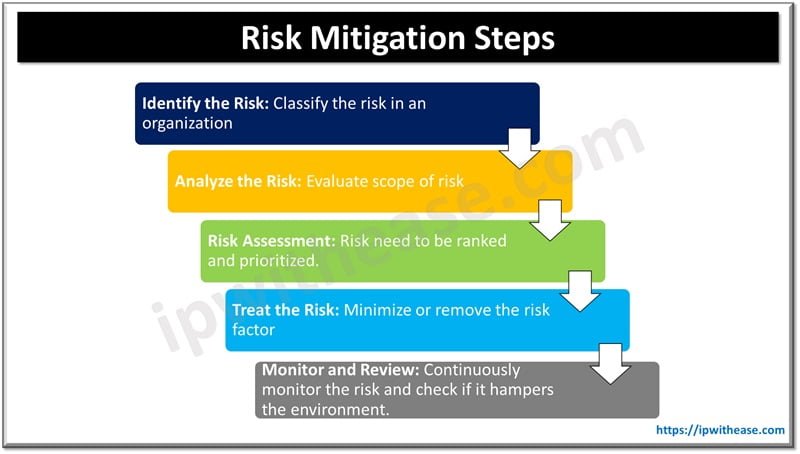
Step 1: Identify the Risk
It is important to identify as many risk factors as possible. Risk can be divided into many parts such as legal, environmental, market or regulatory risk,
Advantages of this approach is to document the list of risks which are present in any system.
Step 2: Analyze the Risk
This approach is used to determine the scope of risk. Severity and gravity of risk is assigned to every risk factor,
Such as physical access to Data Center risk severity is High, in a same way weak password risk severity is moderate.
Step 3: Evaluate the Risk
Evaluation of risk involves a team which presents documentation to management based on their analysis. Risk assessments are further divided into two parts:
- Qualitative Risk: Qualitative risk analysis inclines to be more subjective. It points to identify risks as to measure both the likelihood of a specific risk event occurring during the project life cycle and the severity it will have on the process.
- Quantitative Risk: As the name justifies, it focuses more on quants or stats of the risk. In other words, quantitative risk analysis assigns a numerical value to type of risk, for example — risk A has a 10% chance of occurring, and risk B has 60% chance of occurring.
Step 4: Treat the Risk
Further, every risk needs to be treated and eliminated from the environment by using multiple steps. In a risk management resolution, all the associated participants can be sent notifications from within the system. The discussion about the risk and its probable solution can take place from within the system. Higher management can also closely monitor the solutions.
Step 5: Monitor and Review
Continue to monitor the mitigation plan post risk assessment. Continuously monitor the outcome of the mitigation test and ensure that plan is working appropriately.
Preventive Measures
Steps helpful to reduce attack surface:
- Remove Complication: Implement simple policies which are easy to understand and reduce complexity in implementation.
- Monitor Vulnerability: Performs regular network scan in organization to identify the weakness and associated threats.
- Prefer Zero-Trust-Policies: It ensures that appropriate access has been given to the users.
- InfoSec Trainings: Provide infosec training to the employees on a regular basis to avoid any human error.
Conclusion
If any organization shadows the best practices, it will significantly reduce the attack surface in the environment. However, we can’t protect everything instantly, things have changed from time to time as the requirements and infrastructure changes constantly.
Continue Reading:
Using ACL to Mitigate IP Address Spoofing
Network Vulnerabilities and the OSI Model
ABOUT THE AUTHOR

I am here to share my knowledge and experience in the field of networking with the goal being – “The more you share, the more you learn.”
I am a biotechnologist by qualification and a Network Enthusiast by interest. I developed interest in networking being in the company of a passionate Network Professional, my husband.
I am a strong believer of the fact that “learning is a constant process of discovering yourself.”
– Rashmi Bhardwaj (Author/Editor)