There are various methods in which the two autonomous systems of different service providers can interact to provide service to same customer locations in different geographies.
Listed below are some suitable methods to achieve AS-AS communication –
1: Option A – VRF-VRF.
2: Option B has following three methods again
- 2A – Next-Hop-Self
- 2B – Redistribute Connected
- 2C – eBGP -Multihop
3: Option C – RR to RR.
Note – This document will only address to Option A – VRF-VRF communication.
The need for Inter-AS communication arises when a customer needs to have Connectivity across all its branch offices globally and no single service provider have network availability (feasibility) across all the branch locations of the same customer.
In such cases the Global service provider take help of regional service provider to cater to customer traffic in that region.
In this document we will go ahead and configure VRF-VRF method between two AS (AS100 of Service Provider 1 and AS200 of Service provider 2). Other options will be discussed in the upcoming posts.
TOPOLOGY

Router detail is shared in the table –
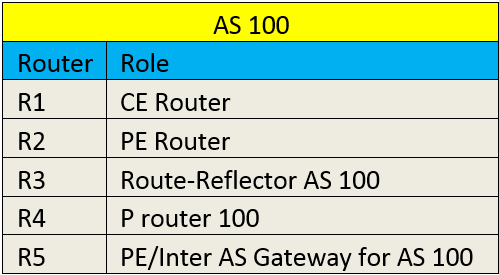
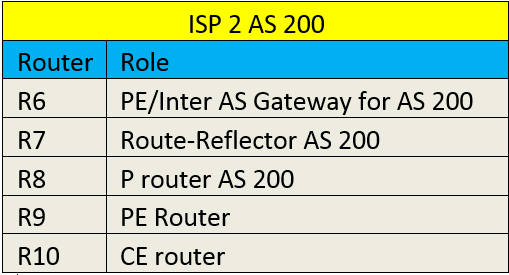
In the above topology R1 represents router at customer Site 1 and R10 represents router at customer site 2 in two different regions.
Service Provider 1(AS100) with the help of Service provider 2 (AS200) is able to cater to its customer site in a region in which it doesn’t have presence but service provider 2 has.
In order the achieve this an eBGP neighbourship is created between the AS gateways R5 and R6 using the respective VRF address-family.
Also the interfaces on which the two service providers connect should be under respective VRF.
Similarly if we have more than one customer here, we would require equal number of interfaces/sub-interfaces to connect between R5 & R6 and assign them to respective VRF. (This can also be stated as a drawback of using this method)
EXPECTED OUTPUT –
The scenario will be considered complete when Loopback of R1 is able to Loopback of R10.
SCENARIO AS BELOW –
R5 CONFIG:
interface FastEthernet0/1
vrf forwarding ASGW1
ip address 9.9.56.5 255.255.255.0
mpls ip
!
address-family ipv4 vrf ASGW1
neighbor 9.9.56.6 remote-as 200 #Creating IPV4 eBGP neighbourship with the Service Provider 2 Gateway Router R6#
neighbor 9.9.56.6 activate
exit-address-family
R6 CONFIG:
interface FastEthernet0/0
vrf forwarding ASGW2
ip address 9.9.56.6 255.255.255.0
mpls ip
!
address-family ipv4 vrf ASGW2
neighbor 9.9.56.5 remote-as 100 #Creating IPV4 eBGP neighbourship with the Service Provider 2 Gateway Router R5#
neighbor 9.9.56.5 activate
exit-address-family
COMPLETE CONFIGURATION –
R1 CONFIG –
interface Loopback0
ip address 9.9.0.1 255.255.255.255
!
interface FastEthernet0/0
ip address 9.9.12.1 255.255.255.0
!
router bgp 300
bgp log-neighbor-changes
network 9.9.0.1 mask 255.255.255.255
neighbor 9.9.12.2 remote-as 100
R2 CONFIG –
ip cef
vrf definition ASGW1
rd 2:2
route-target export 2:1
route-target import 5:1
!
interface Loopback0
ip address 9.9.0.2 255.255.255.255
ip ospf 1 area 0
!
interface FastEthernet0/0
vrf forwarding ASGW1
ip address 9.9.12.2 255.255.255.0
mpls ip
!
interface FastEthernet0/1
ip address 9.9.23.2 255.255.255.0
ip ospf 1 area 0
mpls ip
!
router bgp 100
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 9.9.0.3 remote-as 100
neighbor 9.9.0.3 update-source Loopback0
!
address-family ipv4
exit-address-family
!
address-family vpnv4
neighbor 9.9.0.3 activate
neighbor 9.9.0.3 send-community both
exit-address-family
!
address-family ipv4 vrf ASGW1
neighbor 9.9.12.1 remote-as 300
neighbor 9.9.12.1 activate
neighbor 9.9.12.1 as-override
exit-address-family
R3 CONFIG –
ip cef
interface Loopback0
ip address 9.9.0.3 255.255.255.255
ip ospf 1 area 0
!
interface FastEthernet0/0
ip address 9.9.23.3 255.255.255.0
ip ospf 1 area 0
mpls ip
!
interface FastEthernet0/1
ip address 9.9.34.3 255.255.255.0
ip ospf 1 area 0
mpls ip
!
router bgp 100
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 9.9.0.2 remote-as 100
neighbor 9.9.0.2 update-source Loopback0
neighbor 9.9.0.4 remote-as 100
neighbor 9.9.0.4 update-source Loopback0
neighbor 9.9.0.5 remote-as 100
neighbor 9.9.0.5 update-source Loopback0
!
address-family ipv4
exit-address-family
!
address-family vpnv4
neighbor 9.9.0.2 activate
neighbor 9.9.0.2 send-community extended
neighbor 9.9.0.2 route-reflector-client
neighbor 9.9.0.4 activate
neighbor 9.9.0.4 send-community extended
neighbor 9.9.0.4 route-reflector-client
neighbor 9.9.0.5 activate
neighbor 9.9.0.5 send-community extended
neighbor 9.9.0.5 route-reflector-client
exit-address-family
R4 CONFIG –
ip cef
interface Loopback0
ip address 9.9.0.4 255.255.255.255
ip ospf 1 area 0
!
interface FastEthernet0/0
ip address 9.9.34.4 255.255.255.0
ip ospf 1 area 0
mpls ip
!
interface FastEthernet0/1
ip address 9.9.45.4 255.255.255.0
ip ospf 1 area 0
mpls ip
R5 CONFIG –
ip cef
vrf definition ASGW1
rd 5:5
route-target export 5:1
route-target import 2:1
!
address-family ipv4
exit-address-family
!
interface Loopback0
ip address 9.9.0.5 255.255.255.255
ip ospf 1 area 0
!
interface FastEthernet0/0
ip address 9.9.45.5 255.255.255.0
ip ospf 1 area 0
mpls ip
!
interface FastEthernet0/1
vrf forwarding ASGW1
ip address 9.9.56.5 255.255.255.0
mpls ip
!
router bgp 100
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 9.9.0.3 remote-as 100
neighbor 9.9.0.3 update-source Loopback0
!
address-family ipv4
exit-address-family
!
address-family vpnv4
neighbor 9.9.0.3 activate
neighbor 9.9.0.3 send-community both
exit-address-family
!
address-family ipv4 vrf ASGW1
neighbor 9.9.56.6 remote-as 200 #Creating IPV4 eBGP neigghbourship with the Service Provider 2 Gateway Router R6#
neighbor 9.9.56.6 activate
exit-address-family
R6 CONFIG –
ip cef
vrf definition ASGW2
rd 6:6
route-target export 6:1
route-target import 9:1
!
address-family ipv4
exit-address-family
!
interface Loopback0
ip address 9.9.0.6 255.255.255.255
ip ospf 1 area 0
!
interface FastEthernet0/0
vrf forwarding ASGW2
ip address 9.9.56.6 255.255.255.0
mpls ip
!
interface FastEthernet0/1
ip address 9.9.67.6 255.255.255.0
ip ospf 1 area 0
mpls ip
!
router bgp 200
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 9.9.0.7 remote-as 200
neighbor 9.9.0.7 update-source Loopback0
!
address-family ipv4
exit-address-family
!
address-family vpnv4
neighbor 9.9.0.7 activate
neighbor 9.9.0.7 send-community both
exit-address-family
!
address-family ipv4 vrf ASGW2
neighbor 9.9.56.5 remote-as 100 #Creating IPV4 eBGP neigghbourship with the Service Provider 2 Gateway Router R5#
neighbor 9.9.56.5 activate
exit-address-family
R7 CONFIG –
ip cef
interface Loopback0
ip address 9.9.0.7 255.255.255.255
ip ospf 1 area 0
!
interface FastEthernet0/0
ip address 9.9.67.7 255.255.255.0
ip ospf 1 area 0
mpls ip
!
interface FastEthernet0/1
ip address 9.9.78.7 255.255.255.0
ip ospf 1 area 0
mpls ip
!
router bgp 200
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 9.9.0.6 remote-as 200
neighbor 9.9.0.6 update-source Loopback0
neighbor 9.9.0.8 remote-as 200
neighbor 9.9.0.8 update-source Loopback0
neighbor 9.9.0.9 remote-as 200
neighbor 9.9.0.9 update-source Loopback0
!
address-family ipv4
exit-address-family
!
address-family vpnv4
neighbor 9.9.0.6 activate
neighbor 9.9.0.6 send-community extended
neighbor 9.9.0.6 route-reflector-client
neighbor 9.9.0.8 activate
neighbor 9.9.0.8 send-community extended
neighbor 9.9.0.8 route-reflector-client
neighbor 9.9.0.9 activate
neighbor 9.9.0.9 send-community extended
neighbor 9.9.0.9 route-reflector-client
exit-address-family
R8 CONFIG –
ip cef
interface Loopback0
ip address 9.9.0.8 255.255.255.255
ip ospf 1 area 0
!
interface FastEthernet0/0
ip address 9.9.78.8 255.255.255.0
ip ospf 1 area 0
mpls ip
!
interface FastEthernet0/1
ip address 9.9.89.8 255.255.255.0
ip ospf 1 area 0
mpls ip
R9 CONFIG –
ip cef
vrf definition ASGW2
rd 9:9
route-target export 9:1
route-target import 6:1
!
address-family ipv4
exit-address-family
!
interface Loopback0
ip address 9.9.0.9 255.255.255.255
ip ospf 1 area 0
!
interface FastEthernet0/0
ip address 9.9.89.9 255.255.255.0
ip ospf 1 area 0
mpls ip
!
interface FastEthernet0/1
vrf forwarding ASGW2
ip address 9.9.109.9 255.255.255.0
mpls ip
!
router bgp 200
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 9.9.0.7 remote-as 200
neighbor 9.9.0.7 update-source Loopback0
!
address-family ipv4
exit-address-family
!
address-family vpnv4
neighbor 9.9.0.7 activate
neighbor 9.9.0.7 send-community both
exit-address-family
!
address-family ipv4 vrf ASGW2
neighbor 9.9.109.10 remote-as 300
neighbor 9.9.109.10 activate
neighbor 9.9.109.10 as-override
exit-address-family
R10 CONFIG –
interface Loopback0
ip address 9.9.0.10 255.255.255.255
!
interface FastEthernet0/0
ip address 9.9.109.10 255.255.255.0
!
router bgp 300
bgp log-neighbor-changes
network 9.9.0.10 mask 255.255.255.255
neighbor 9.9.109.9 remote-as 200
VERIFICATION:
R1#ping 9.9.0.10 source 9.9.0.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 9.9.0.10, timeout is 2 seconds:
Packet sent with a source address of 9.9.0.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 280/323/372 ms
R1#traceroute 9.9.0.10 source 9.9.0.1
Type escape sequence to abort.
Tracing the route to 9.9.0.10
VRF info: (vrf in name/id, vrf out name/id)
1 9.9.12.2 96 msec 92 msec 32 msec
2 9.9.23.3 [MPLS: Labels 19/22 Exp 0] 208 msec 152 msec 128 msec
3 9.9.34.4 [MPLS: Labels 19/22 Exp 0] 484 msec 184 msec 100 msec
4 9.9.56.5 [MPLS: Label 22 Exp 0] 128 msec 144 msec 140 msec
5 9.9.56.6 196 msec 168 msec 136 msec
6 9.9.67.7 [MPLS: Labels 19/22 Exp 0] 336 msec 276 msec 264 msec
7 9.9.78.8 [MPLS: Labels 19/22 Exp 0] 252 msec 248 msec 268 msec
8 9.9.109.9 [MPLS: Label 22 Exp 0] 228 msec 216 msec 244 msec
9 9.9.109.10 240 msec 284 msec 196 msec
Able to see the loopback route of R1 on R6:
R6#sh ip bgp vpnv4 vrf ASGW2
BGP table version is 4, local router ID is 9.9.0.6
Status codes: s suppressed, d damped, h history, * valid, > best, i – internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
Origin codes: i – IGP, e – EGP, ? – incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 6:6 (default for vrf ASGW2)
*> 9.9.0.1/32 9.9.56.5 0 100 300 I #Next-Hop is router R5#
*>i 9.9.0.10/32 9.9.0.9 0 100 0 300 i
Able to see the loopback route of R10 on R5.
R5#sh ip bgp vpnv4 vrf ASGW1
BGP table version is 4, local router ID is 9.9.0.5
Status codes: s suppressed, d damped, h history, * valid, > best, i – internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
Origin codes: i – IGP, e – EGP, ? – incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 5:5 (default for vrf ASGW1)
*>i 9.9.0.1/32 9.9.0.2 0 100 0 300 i
*> 9.9.0.10/32 9.9.56.6 0 200 300 I #Next-Hop is router R6#
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj