UBRL is a bandwidth policing (microflow policing) allowing to rate limit traffic flows, not only as a normal policer does, it allows a policer to be applied to all traffic to or from a specific user. Lets now drill deep into how UBRL works, which platforms support UBRL and some scenarios as to how UBRL can be deployed and configured.
Related- Traffic Policing vs Shaping
Cisco Platforms supporting UBRL –
- Catalyst 6500 (Supervisor Engine 720)
- Catalyst 4900M (Supervisor Engine V-10GE)
- ASR 9000
Cisco Catalyst 6500 supports 2 different types of policing – Aggregate policing and microflow policing. A total of 1023 aggregate policers and 63 microflow policers are supported on the Supervisor Engine 720, and it supports just over 128,000 flows. An aggregate policer applies a rate-limiting policy to all traffic in a VLAN or port that matches set classification criteria
The microflow policer differs in that it applies a rate-limiting policy on a per-flow basis. Whereas the aggregate policer limits the total amount of traffic entering that VLAN, the same microflow policer would only limit each flow to the stated rate.
Cisco catalyst 6500, 4900M and ASR 9000 all employ micro policer to rate limit policy on per-flow basis where it dynamically learns traffic flows and rate-limit each unique traffic flow to an individual rate on per-flow basis.
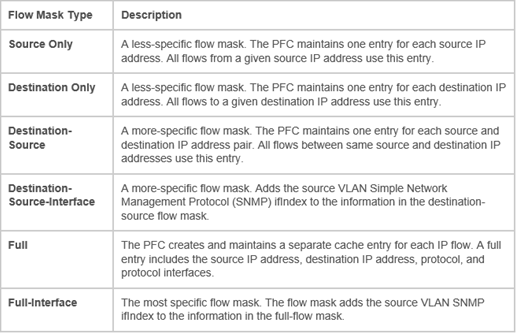
Flow Mask –
The flow mask identifies fields in the packet header that are used to perform a lookup into the NetFlow table and is what defines a flow
Flow Masks Available on the PFC3x of 6500
Flow Masks Available on Cisco ARS 9000
Configuring Bidirectional UBRL – Catalyst 6500
UBRL is well suited to university requirements, where student traffic can compromise available bandwidth on the campus. The sheer volume of peer-to-peer (P2P) traffic created by a host of file-sharing applications is usually the main culprit. Many universities seek ways to limit this traffic to a more manageable level. UBRL can be applied to rate limit both outbound and inbound traffic to users of the network.
Bidirectional UBRL Scenario Example
In this example two flow masks will be combined to limit traffic to and from users in the computer science faculty. Each user (student) will be limited to uploading or downloading no more than 1 Mb of data. The computer science faculty uses the 202.25.1.0/24 subnet. In order to achieve this, the following configuration could be applied:
6500(config)# access-list 142 permit ip 202.25.1.0 0.0.0.255 any
6500(config)# access-list 143 permit ip any 202.25.1.0 0.0.0.255
6500(config)# class-map identify-outbound-student
6500(config-cmap)# match access-group 142
6500(config)# class-map identify-inbound-student
6500(config-cmap)# match access-group 143
6500(config)# policy-map police-student-traffic-outbound
6500(config-pmap)# class identify-outbound-student
6500(config-pmap-c)# police flow mask src-only 1000000 1000 conform-action transmit exceed action drop
6500(config)# policy-map police-student-traffic-inbound
6500(config-pmap)# class identify-inbound-student
6500(config-pmap-c)# police flow mask dest-only 1000000 1000 conform-action transmit exceed action drop
6500(config-pmap-c)# interface gig8/22
6500(config-if)# service-policy input police-student-traffic-inbound
6500(config-pmap-c)# interface gig8/23
6500(config-if)# service-policy input police-student-traffic-outbound
In this example, two separate ACLs are defined: one to classify outbound traffic by focusing on the source subnet and the second to classify inbound traffic focusing on the destination subnet (this is return traffic back to the faculty). Two separate policers are configured: one for outbound traffic and one for return traffic. Each policer uses a different flow mask to match on interesting traffic to or from the faculty. For outbound traffic, the policer uses a source only flow mask to match on traffic originating from the faculty. Each unique user will be limited to 1 Mb of upstream bandwidth. Return traffic matching on the inbound policer sues the destination-only IP flow mask. This matches on faculty user addresses and limits their download bandwidth also to 1 Mb.
Configuring Bidirectional UBRL – ASR 9000
In this example, two class-maps are created, one for inbound and another for outbound traffic, and match criteria are defined. The policy-maps are applied on the input and output direction of the interface.
Class-map match-all ubrl-src
match precedence 0 1 2 3
match flow-key src-ip
!
Class-map match-all ubrl-dst
match precedence 0 1 2 3
match flow-key dst-ip
!
policy-map ubrl-mult-src
class ubrl-src
police rate 200 kbps
!
!
policy-map ubrl-mult-dst
class ubrl-dst
police rate 200 kbps
!
!
interface gigabitethernet 0/0/0/4
service-policy input ubrl-mult-src
service-policy output ubrl-mult-dst
!
End
Reference –
ABOUT THE AUTHOR

I am here to share my knowledge and experience in the field of networking with the goal being – “The more you share, the more you learn.”
I am a biotechnologist by qualification and a Network Enthusiast by interest. I developed interest in networking being in the company of a passionate Network Professional, my husband.
I am a strong believer of the fact that “learning is a constant process of discovering yourself.”
– Rashmi Bhardwaj (Author/Editor)