Table of Contents
Data is a valuable asset which attackers want to steal, destroy or possess to fulfil their malicious intent. In the initial days of computing organizations relied on perimeter security defenses and the approach of ‘once authenticated then trusted always’. In today’s scenario when geographical boundaries are quickly diminishing and users can operate from anywhere in the world this approach no longer works. This new age of computing brought the approach of ‘zero trust architecture’ which means trust no one and verify at each stage.
In today’s topic we will learn about zero trust model, how it is different from earlier models of perimeter security, and what are the five steps methodology to implement zero trust architecture.
What is Zero trust
Zero trust network security model is a response to traditional model of security where organizations relied only on perimeter security defenses such as firewalls. But as physical boundaries started diminishing fast as public and private cloud took over this traditional approach failed to protect the organization networks and sensitive data. As once hackers passed away from corporate firewalls they were able to move laterally inside the internal systems without the risk of being caught or discovered. The perimeter itself could not be defined clearly as applications and data stores are distributed on-premises and over cloud, having users accessing them from anywhere on the globe using a variety of devices.
Instead of the age-old belief to assume that everything inside a perimeter Corporate firewall is secure, the zero-trust model works on the principle of verification of each access request and it is treated as if it is generated from an open network. Where a request is originated, what resource access is requested works on the principle of “never trust, always verify’. Every access request is authenticated, authorized and encryption is applied before providing access. Micro-segmentation and least access privileges principles are followed to minimize the risk of exposure and lateral movement. Real time threat detection and analytics are utilized to detect and respond to anomalies in a timely manner.
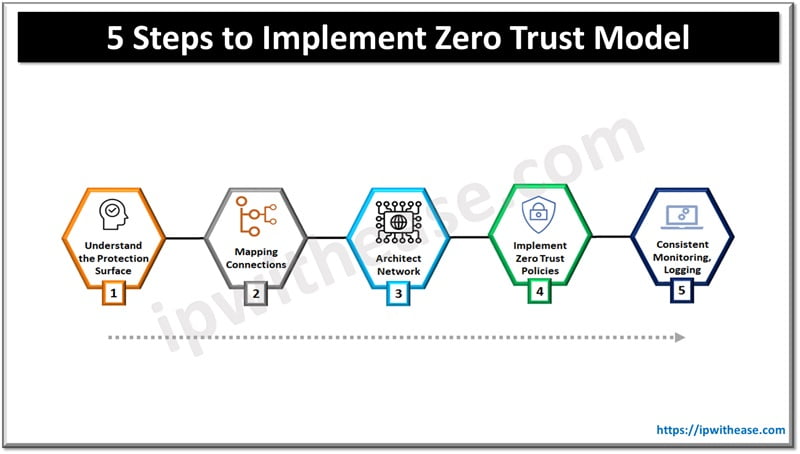
Steps to Implement Zero Trust Model
Organizations know that zero trust is an effective approach to cyber threats. Building a zero-trust architecture using a five-step model helps to secure data and networks. Let’s do some deep dive into this.
Step 1: Define the Attack Surface
To reduce attack surface zero trust approach works on the principle of identification of surface which needs to be protected rather than protecting everything which is getting added into the network. The ‘protect surface’ comprises critical data, applications, assets and services which are the most valuable asset for the organizations.
Some critical assets examples are:
- Sensitive data – credit card, health information, personally identifiable information (PII) such as customer credentials, and intellectual property (IP)
- Critical applications – databases, transactions and authentication
- Physical assets – Point of Sale terminals (POS), medical equipment, manufacturing assets and IoT devices
- Corporate services – such as DNS, DHCP, active directory etc.
Under zero trust approach organizations move their critical assets and services near to protected surface.
Step 2: Implement Controls on Network Traffic
The network traffic movement across the network determines its protection strategy. It is important to gain insight into all interdependencies of assets which require protection. Mapping network traffic allows addition of security controls to assets to enforce access control over them.
Step 3: Custom Zero Trust Network
Zero trust model provides a blueprint to implement, monitor and secure networks. However, each organization’s requirements are unique to its business hence once an organization has identified its critical assets, services, applications it is time to define layered defense approach and mapped flows relative to business needs.
Related: Zero Trust Network Access vs Zero Trust Application Access
Step 4: Design Your Own Zero Trust Policies
Once zero trust network is established organizations are required to deploy policies using ‘Kipling methodology’ for whitelisting resources for which access is required. Based on the Kipling method, determine – who, what, where, why and how? Technique of his poem ‘six serving men’.
- Who should have access to resources?
- What application is used inside the protected surface to access the resource?
- When is the resource accessed?
- Where is the destination of the packet?
- Why is the packet trying to access resources within a protected surface? And
- How is the packet accessing resources within the protected surface from application?
Security policy application based on such detailed assessment ensures only legitimate application communication happens.
Step 5: Monitoring and Logging for Improved Security
Review of all logs, internal and external all through layer 7, focusing on operational aspects of zero trust is the prime objective eventually. It is an iterative process where inspection and logging of all traffic including the network provides insight into the security posture of network over time.
Once zero trust architecture is defined you can move your applications, data, critical assets and services from legacy networks to zero trust network for more effective strategy on security.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj