Table of Contents
Zero Trust security ensures that your employees, partners, and contractors can securely access your network from remote locations. Instead of relying on networks and trust, access is managed based on identities and devices, constantly validating users and denying access to malicious attacks.
Zero Trust architecture consists of various security models: ZTNA, ZTAA, and ZTA. It is crucial to understand the distinctions between them as they determine the level of network protection and security posture. This blog post aims to clarify the difference ZTNA vs ZTAA.
Zero Trust Network Access
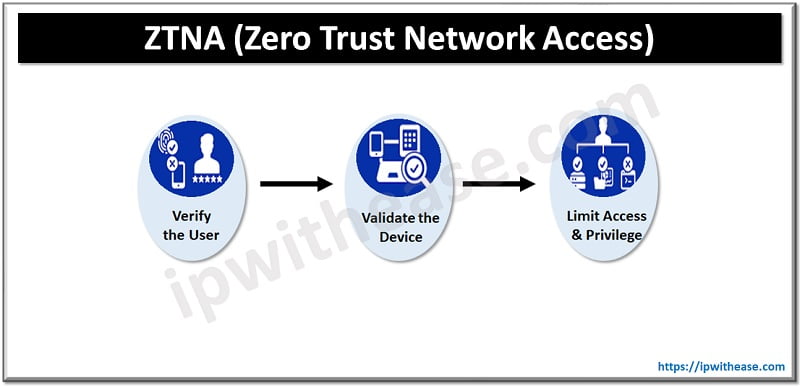
Zero Trust Network Access or ZTNA is a category of technology that provides secure remote access to applications and services. Unlike VPN, ZTNA provides secure access on an application basis, automatically setting up and tearing down the tunnels as necessary. But to understand ZTNA it is very important to know the model and framework it’s based on.
ZTNA is a component or subgroup of the Zero Trust security model. This model provides you a philosophy on how you should approach Network Security. This also helps to understand how we should accomplish ZTNA.
Zero Trust Security Model
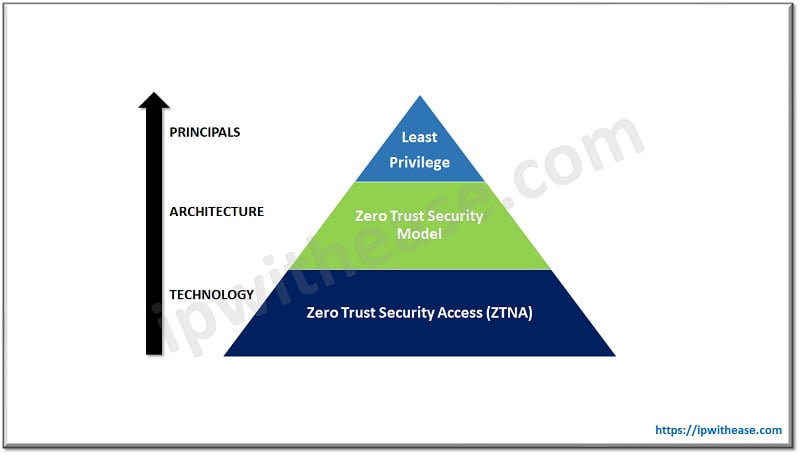
Zero Trust Security Model specifies that no one from outside or inside of the network is to be trusted unless the identifications have been thoroughly checked. Assumption is that anyone can be compromised; it doesn’t matter if someone resides in the same network or across the globe, everyone must be verified.
In other words access to applications and resources are not accepted based on the location which means users inside or outside of the network are not to be trusted by default. Users can be verified and given only the minimum amount of access that they need. Means if a user is authorized to access any application “A” would not be allowed to access any other application in the network.
Verification accomplished in different ways depending on the implementation but at the minimum it includes the following 2 pillars.
- Identify🡺 it specifies the user identifications, authentications and authorization. In other words who are you, who you claim to be and are you authorized to that resource.
- Context🡺 how the user is trying to access the resources. This pillar is based on the least privileged model. Users are only granted the least possible amount of access that they need. Applications are hidden from the user if the user doesn’t have access.
- Security🡺 it focuses on the device in which user is connecting on. If you verify who you say you are and you should allow accessing the resource. Security posture may encompass several security checks on the user machine to make sure the device is compliant. Means a software installed on a user machine checks several conditions before allowing access to the user.
Furthermore Zero Trust isn’t limited to the giving access however Zero Trust continuously monitors the user activity and validates the changes in Identity, context and security.
Zero Trust Application Access
ZTAA is a layer 7 approach to secure the application level of infrastructure which means ZTAA gives users the right of entry to particular applications. ZTAA provides security and control to applications in the network.
Why would we require a ZTAA solution in our network?
Type of work culture has changed in the last few years. Now-a-days employees are doing work from home, accessing data from cloud environments and performing tasks with third party clients are few examples of how the business has transformed.
VPN doesn’t provide end to end security for such a type of network and fails to provide compliance as well. To secure remote based networks and to provide end to end security ZTAA has been introduced with Zero Trust principles.
ZTAA Features
- Remote Access🡺 ZTAA is designed to secure the Cloud/remote access network which uses applications remotely. Now a day’s on-premises network is obsolete. Organizations have been moved to the hybrid network in which remote work is allowed to the users. So when users access any application over VPN or remote network, in that case ZTAA validates the privileges and monitors network traffic throughout the session. Moreover connection will be denied and blocked immediately if someone tries to access the unauthenticated application.
- Granular Monitoring Approach🡺 ZTAA uses granular monitoring to track the session step by step. It calculates the risk factor for a particular application, how it’s being used by the user, what is the severity of the risk and displays the details to the associated device.
- Provide Layer 7 Security 🡺 ZTAA provides security from system level which means if user trying to access any application from his system then tracking will be starting from user’s system to application server.
- Provide Compliance 🡺 PCI DSS, HIPPA are the regulatory approach to regulate unauthorized access of any organization’s data. ZTAA applies Zero Trust principle to ensure that unauthorized access is not allowed in the network.
ZTNA vs ZTAA: Comparison Table
Below table summarizes the differences between the two:
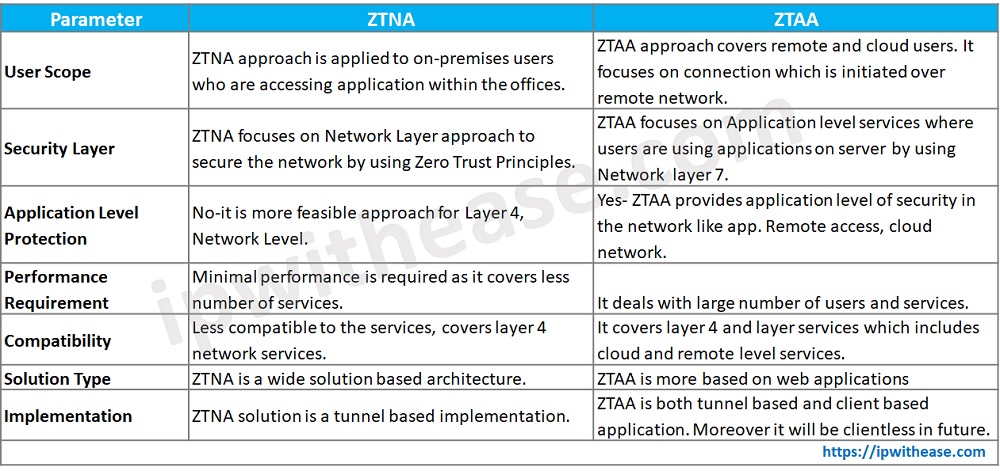
Download the comparison table: ZTNA vs ZTAA
Continue Reading:
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj