Table of Contents
Organizations have been heavily investing in Anti-malware and threats protection solutions. Once such major attack which can affect IT assets is the risk of Zero-Day Attack/ Zero Day Exploit. Are you hearing it the first time? Do you want to know more about it? Follow this article with me.
In this blog, we discuss Zero Day Exploit, its process, its process, causes, detection and prevention or mitigation.
Zero Day Exploit
Zero Day Exploit is the attack (data theft) done by the hackers through new or recently discovered software Vulnerability that is unpatched or unknown to the software vendor. It is a dangerous attack as the users are not aware of the vulnerability, and this gives the attacker time to exploit the data and information of the users.
Some technical experts say that Zero Day attacks occur at the same time the vulnerabilities are made public. Others say that the attackers exploit the information for years until the vulnerability is discovered and patched. I feel both the definition make sense. Let understand this back in the article.
To have a good understanding of Zero Day Exploit, you should know the full process involved with it.
Zero Day Exploit: How you get attacked?
All the software and web applications will have many vulnerabilities/weaknesses when created. The software vendor or web companies will fix all the flaws and release the perfect version to the market. All the software and new applications were checked with the Common Vulnerability and Exposures (CVE) list.
What is the CVE list?
It is a list used by various Cyber security companies around the world. A unique identification number and description is given to all publically known cyber security vulnerabilities.
After all these measures, there may be new or undiscovered vulnerabilities in the software. It may be found by the users or in the self-examination of the developer or by an attacker. Let’s see what happens then.
Users Report It
The developer will release the security patch once reported. And there is no risk in this case. In rare situations, the attackers will learn this vulnerability and attack the software before the patch release. It proves the first definition of Zero-Day Exploit.
By Self-Testing
The company will fix the vulnerability in the next update. If serious, they will bring the whole application to Maintenance and will fix it as soon as possible. There is no chance for the attacker to enter.
Attacker Exploits and Sells It
The persistent probing of a determined hacker will force your security to crack and give a loophole (vulnerability) to enter the software. Both the vendor and user will not be aware of the vulnerability and exploit. The exploit sold for a large sum in the black market. And some attackers will use this vulnerability to induce malware into the system.
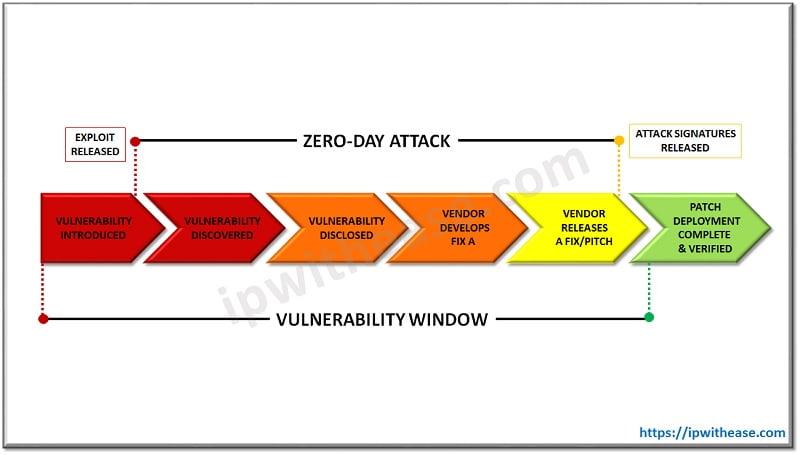
When they find it, they will rush to fix it. The day when the developer discovers the vulnerability, it is known as Day Zero. The time gap between the Attacker and the User’s discovery is called Vulnerability Window. The longer the Vulnerability Window, higher the risk.
Once the vulnerability is discovered and patched up, it is no longer called Zero-day Vulnerability, and the information is added with the CVE list.
Related – Top 5 Data Breaches in Cyber Security
How to Detect Zero Day Exploit?

By definition, it is clear that Zero Day attacks are hard to trace or detect. Most of the Zero Day Attacks are still unknown by the Vendor or Developer. The experts recommended some methods to detect the Zero Attacks, but still, they are not enough.
Machine Learning or Artificial Intelligence
Most of the Cyber security experts call Machine learning the long term solution. Traditional methods like Signature and Statistics based detection followed by the security companies are no use in the case of Zero-Day Attacks.
The statistics method uses a large past database to detect the threats, whereas the signature method uses past signs or symptoms to detect the malware. But both of these cannot find the unknown vulnerability which is the major cause of Zero-Day attacks.
The modern behavior-based detection method can help to find new vulnerabilities. The modern method instead of comparing with past information they check the internal behavior and interactions of the software. If it finds any malicious activities, they are reported to the user.
A hybrid solution where all three methods of detection coexist is under development with the machine learning or Artificial Intelligence technique. With this hybrid solution, it is expected it will be easy to detect Zero-Day Attacks in the future.
How to Prevent/Recover from Zero-Day Attacks?
Prevention
Prevention is always better than cure. In Zero-Day Attacks, there is no prevention, no cure. The security experts don’t even know what they are protecting and curing as the vulnerability is unknown. But here are some points for you to follow.
- Never install unwanted software to your system. Regularly review the software and uninstall the unnecessary ones.
- Make sure all the existing software is up-to-date.
- Deploy more firewalls to know any malicious attempt. Though you cannot prevent it, at least you can aware of it.
Recovery
The main rule of the recovery is to control the chaos. Here are some steps for an effective recovery.
- Allot the responsibilities separately, so the response team can act effectively once the chaos arise
- Control the spread of news to avoid unwanted panic and new threats. Keeps the information only between the relevant people.
- Train the team member using the latest tools to reduce the impact of Zero-Day Attacks.
- In case of individual back up your data and report to the vendor.
Zero Days attacks remain to be a dangerous threat and it is said the rate of attacks will be substantially high in future. I hope this article has given you a clear idea about Zero-Day Exploit. Please share your thoughts and question in the comment section below.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.