Table of Contents
Introduction to Certificates in Cisco SD-WAN
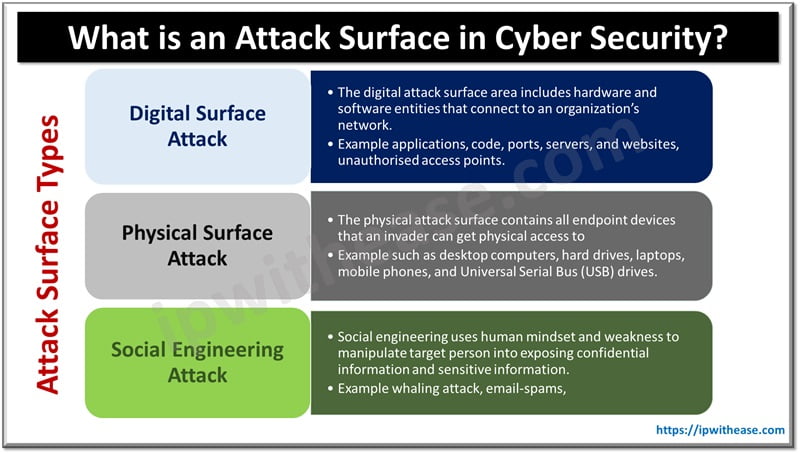
Certificates are critical to the secure integrity of the Cisco SD-WAN solution, thus certification management is of utmost importance. Not only does the solution use a whitelist model to authenticate the solution components, but each controller also provides its identity via a certificate. Each controller (vManage, vBond, and vSmart) will mutually authenticate each other via these certificates and build their control plane connections.
In CISCO SD-WAN,
- The first whitelist is a controller list that is created by manually adding the controllers to the vManage GUI. This list gets distributed to vBond, where it is pushed to the vSmart controllers during the authentication process. The controller list contains the certificate serial numbers for each of the controllers. These serial numbers are used as part of the authentication process.
- The second whitelist identifies the approved WAN Edges in the environment. This list can be downloaded from the PnP portal at https://software.cisco.com or can be retrieved via the Sync Smart Account mechanism within vManage. Once retrieved, the list is distributed to the other controllers by vManage.
Certification Management: The Authentication Process
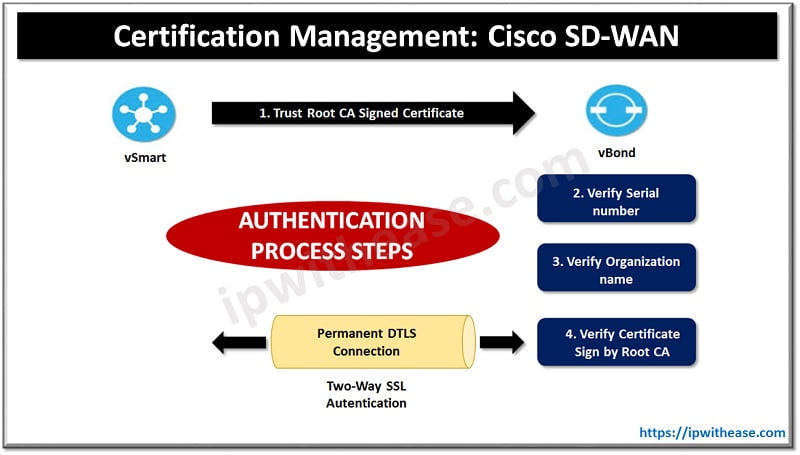
Certificate trust will be validated by checking to make sure the certificate presented is signed by a mutually trusted Root CA. Note that the Root CA certificate chain must be installed on all devices before this can occur. By default, root certificates are already installed for the Symantec, DigiCert, and Cisco CAs. Hence, manually installing the root CA chain is only required when using your own CA. This is a two-way authentication, and each controller authenticates the other one in parallel.
Inside the sending controller’s certificate is the organization name. This value is checked against the locally configured one. This organization name needs to match enterprise-wide. The receiving controller verifies the peer’s certificate serial number against the authorized whitelist received from vManage.
Note that when the vBond is being authenticated, this serial number is not used.
- Automated certificate signing request with Symantec/DigiCert CA.
- Manual certificate signing request with Symantec/DigiCert CA.
- Manual certificate signing request with Cisco PKI CA.
- Certificate signing request with Enterprise CA.
Automated certificate signing request with Symantec/DigiCert CA
- CSR is generated via the vManage GUI for each controller and automatically sent to the Symantec/DigiCert CA.
- Once this is complete, a Cisco CSOne case needs to be opened and the signing request will be authorized.
- After the signing request is authorized, the Symantec/DigiCert CA will generate certificates. vManage will automatically retrieve the certificate(s) and install them on the corresponding controllers.
Manual certificate signing request with Symantec/DigiCert CA
- Administrator will generate a CSR for each controller and manually upload the file to the Symantec/DigiCert portal.
- A CSOne case will then need to be opened and, once the CSR is authorized, the administrator will receive the certificate via email or via download link.
- The administrator will then need to manually install this certificate via the vManage GUI. vManage will then push the certificate to the relevant controller. This type of deployment would be utilized if the controllers have no Internet connectivity or a firewall is blocking HTTP/HTTPS connectivity to the Symantec/DigiCert portal.
Manual certificate signing request with Cisco PKI CA
- Administrator will need to manually generate and upload the CSR to the PnP portal at https://software.cisco.com.
- Once the CSR is authorized, the administrator will need to manually retrieve the certificate(s) from the PnP portal and upload it to vManage, where it will be distributed to the other controllers.
Certificate signing request with Enterprise CA
- Administrator will need to install the root chain from the enterprise CA on each controller.
- Certificate signing requests can be generated for the corresponding controllers via the vManage GUI.
- Administrator would then download the CSR and submit the request for signing to the enterprise CA. Once the CSR is authorized and a certificate is generated, the same process noted previously can be used to upload the signed certificate to the vManage GUI for the appropriate controller.
How to Install Signed Certificate?
Go to Settings > Certificate Signing by Symantec, you selected the Manual option for the certificate-generation process, use the Install Certificate button to manually install certificates on the controller devices. Save them on a server in your local network. Then install them on each controller:
- In the Controllers tab, go to Install Certificate.
- Select a file, or copy and paste the certificate text.
- Click Install. Certificate identifies the controller automatically.
How to Export Root Certificate?
- In the Controllers tab, Go to the Export Root Certificate button.
- Click Download to export the root certificate to a file.
View a Certificate Signing Request
- In the Controllers tab, go to the device.
- Click on the More Actions icon to the right of the row, and click to view CSR.
View a Device Certificate Signing Request
- In the Controllers tab, go to the device.
- Click on the More Actions icon to the right of the row, and click View Device CSR to view the certificate signing request (CSR). Actions icon allows you to view three components:
- View Device CSR
- Generate Feature CSR
- View Feature CSR
View the Certificate
- In the Controllers tab, go to the device.
- Click on the More Actions icon to the right of the row and click View Certificate.
Generate a Certificate Signing Request
- In the Controllers tab, go to the device.
- Click on the More Actions icon to the right of the page and Generate CSR.
- Click Download to download the file to your local PC.
Generate a Feature Certificate Signing Request
- In the WAN Edge List tab, choose a device.
- Click the More Actions icon to the right of the row and Generate Feature certificate signing request.
- In the Generate Feature CSR window, click OK to continue with the generation of feature certificate signing request.
Invalidate a Device
- In the Controllers tab, go to the device.
- Open the More Actions icon to the right of the page and click Invalidate.
- Click OK.
View a Signed Certificate
- In Cisco vManage, select the Configuration > Certificates screen > select Controllers.
- Select the device whose certificate you wish to view.
- Click the More Actions icon to the right of the row, and select View Certificate.
Continue Reading:
Cisco SD-WAN Security with Intrusion Detection and Prevention(IDS/IPS)
Cisco SD-WAN: Ways to Secure Network
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj