Imagine a large organization setup with users roaming in their workspace as per their network policies. Traditional way of managing network access using ACL or access control lists using IP address, subnet details and VLANs is a time-consuming activity. Policy inconsistency, unused policies not removed from the network once defined, lead to policy violations granting unauthorized access to network resources are some of the key limitations.
Today we look more in detail about Cisco TrustSec which simplifies provisioning and management of secure access to network services, its key features, architecture and how it works etc.
Introduction: Cisco TrustSec
Cisco TrustSec helps to establish domains of secure networks with trusted network devices. Device authentication is peer based in the secure network. Communication between devices over links is secured with encryption, integrity check, data path protection algorithms.
Device and user credentials are used during authentication to classify packets by Security groups (SGs) once they enter the secure network. Packet classification information is maintained by packet inline tagging mechanism. The security group tag (SGT) permits enforcement of access control policy with enablement of endpoint devices to act on SGT to traffic filtering.
Features of Cisco TrustSec
- Provides active endpoint scanning for wired, wireless or remote connections
- Supports employees bringing their own devices to work with unprecedented visibility and controls
- Centralized policy enforcement to enable policy creation and consistent policy enforcement across company infrastructure
- A single unified appliance interface to authenticate, authorize, account, posture management, profiling, and guest management
- Contextual visibility into ‘who’, ‘how’, ‘what’, ‘when’ for user identities and devices in the network
- Guest users enablement with restricted access to specific resources
- Role assignment via tags for authorization of users and devices independent of topology
- MACsec encryption to provide data visibility along with confidentiality
Use cases for Cisco TrustSec
- Network segmentation
- Threat containment by device isolation
- Segmentation of IoT devices
- Enterprise policy enforcement to hybrid and multi-cloud environments
- Enhanced access security for BYOD (Bring your own devices)
- Simplification of extranet controls for business and supplier partners
Cisco TrustSec Architecture
The Cisco TrustSec architecture comprises of three key elements:
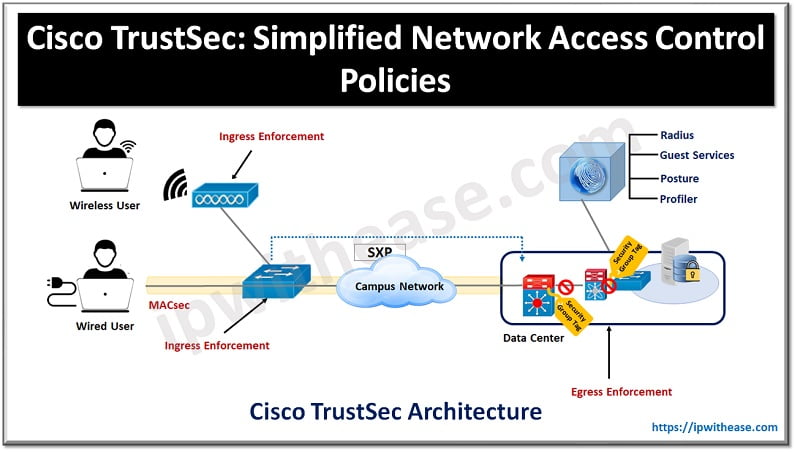
- Network Infrastructure Authentication – The very first device authenticates with an authentication server and as new devices join the network, they are authenticated by their peers already present in the network. Authentication server categorizes each new device and assign a security group-based access control (based on its identity, role, and security posture)
- Security group-based access control mechanism – Topology independent access policies based on roles of source and target devices is tagged
- Security of communication – encryption enabled hardware, message integrity check, data path replay protection and secure communication on links between devices is available
Each device in Cisco TrustSec domain act in one of the following roles:
- Supplicant – unauthenticated device trying to join TrustSec connected with peer
- Authentication server – validation of the identity of supplicant and policy issuance
- Authenticator – authenticated device which can authenticated supplicants
Cisco TrustSec: How does it work?
Cisco TrustSec works on some basic principles (3 of them) as under:
- Tag classification and assignment
- Tag transportation throughout the network
- Enforcement of policy
Tag Classification and Assignment
The process of implementing a policy group tagging (SGT) involves classifying endpoints according to various factors, including the user, device type, device posture, and location. Scalable Group tag or (SGT) is Cisco ISE assigned 16-bit tag to endpoint either dynamically or statically.
Dynamic classification methods such as 802.1x, WebAuth or MAB are used in the access layer whereas static classification is used in switches in data centers with connected servers.
Tag Transportation throughout the Network
Post SGT assignment to endpoint tag transportation happens throughout the network using capable devices. Inline tagging and Secure Exchange protocol is used to perform transport. Inline tagging is done by switches by adding SGT information to the Ethernet frame.
Devices which do not support inline tagging, their Secure Exchange protocol (SXP) is used for SGT transportation. Switches support inline tagging and Secure Exchange protocol is used by router and firewall domains.
Enforcement of Policy
It is done using Secure Group ACL (SGACL). These policies are defined on the basis of source and destination SGT. Policy enforcement is an authorization matrix with source and security group members on one side and destination and security group members on the other side.
Each box in SGACL specifies the permission between source and target system. SGACL only dictates what to allow or what to deny and no target or source information. With SGACL the number of ACL entries are restricted and become less complex as now instead of specifying source and target it deals with groups. On the basis of a simple formula, we can calculate requirements for ACL entries in the permission matrix.
4 SGT (Source) * 3 SGT (Target) * 3 permissions = 36 ACL entries
Quick tip!
Cisco TrustSec market share is (0.03%)
Continue Reading:
What is SXP Protocol? Scalable group tag eXchange Protocol
Cisco SD-WAN Security: Application Aware Enterprise Firewall
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj