Table of Contents
Provisioning and management of highly secure access to network services and applications is every organization’s goal. Unlike usage of access control mechanisms based on network topology, latest innovations allow policies using logical groupings. Highly secure access is maintained in a uniform and consistent manner even if devices are moved in mobile or virtual environments. Traffic classification according to the contextual identity of the endpoint instead of its logical IP address enables the deployment of flexible access controls for dynamic network environments and data centres.
Today we learn more in detail about SXP Protocol which uses contextual identity of endpoints instead of conventional methodology, its use cases, advantages and disadvantages, architecture etc.
About SXP Protocol
SXP or Scalable group tag eXchange Protocol as the name is called are Scalable group tags assigned to endpoints used to connect networks having common network policies. Every Scalable group tag is identified by a unique SGT ID. SXP is a control Plane mechanism to transport endpoint’s SGT with IP address from one SGT aware network to another SGT aware network.
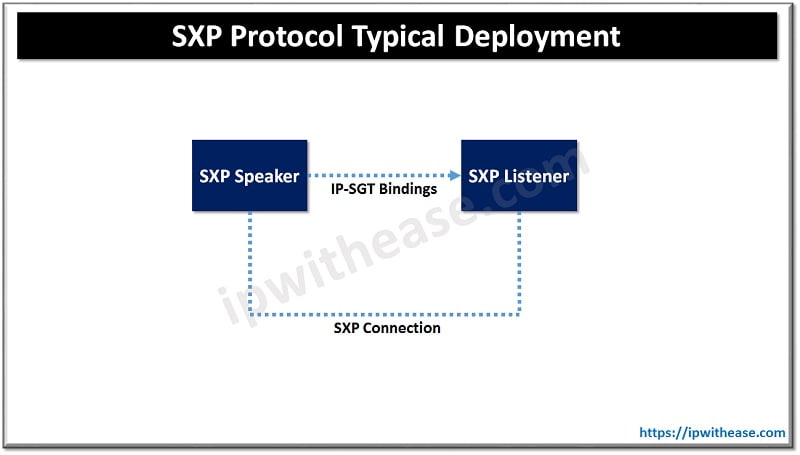
Scalable group tags used at control plane mechanism and let transport of data from one SGT aware network to another SGT aware network. SXP uses TCP protocol to have SXP connection between two separate network devices. The SXP peer is designated as speaker and listener. Peers can be configured to operate in bi-directional mode (can act as speaker or listener both). Either of the peers can initiate connection however binding information is propagated from speak to listener always.
SGT aware network devices make policy decisions based on the role and intent of the endpoint expressed as Scalable group and represented by SGT tag. SGT is a 16-bit value which Cisco ISE assigns to the user or endpoint session upon login.
Components of SXP protocol
- SXP Connection establishment
- IP SGT binding propagation
SXP connection establishment –
SXP connection is point to point and uses TCP as underlying transport protocol. SXP connection consists of: – Source IP address and Peer IP address which is used to construct TCP connection. SXP connection can be unidirectional or bi-directional communication. One peer acts as a SXP speaker and the other one acts as SXP listener. SXP speaker is responsible to send IP-SGT bindings SXP listener is responsible for collecting the IP-SGT bindings received from speaker peer and also does management of bindings received from several connections.
SXP connection password – Same authentication mechanism is required if SXP data integrity is in question. (MD5 or TCP-AO). The passwords should match on both peers in MD5 and key chains if TCP-AO is used.
An SXP connection maintains the following states: OFF, PENDING_ON, DELETE_HOLD_DOWN and ON.
Each of these states indicates connection status
- ‘ON’ state then SXP connection is set up successfully.
- ‘OFF’ indicates connection initiation not started
- ‘PENDING_ON’ means response is awaited from peer
- ‘DELETE_HOLD_ON’ means connection is terminated (only listener can be in this state)
IP SGT bindings propagation –
Once the SGT is assigned to the user session next step is to propagate SGT. SGT propagation can happen in two ways: inline or SXP. The packets get tagged on the uplink port and through infrastructure. The upstream switch continues to tag the traffic in the entire infrastructure. The tag is completely independent irrespective of whether it is IPv4 or IPv6. With tag being applied to every layer 2 link policy can be enforced at any point in infrastructure.
Features of SXP Protocol
- Simple to deploy
- Reduction in static access control lists
- Limit’s malware propagation
- Uses MD5 for authentication and integrity checks
- Supports single hop or multiple hop SXP aggregation
- Fine grained and dynamic
- SGT based policy creation and enable enforcement on switches, routers, WLANs, Firewalls, Web security appliance etc.
- Dynamic classification of users / devices within existing network
Continue Reading:
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj