Table of Contents
What is DNS Sinkhole?
The DNS sinkhole is a mechanism to falsify a response to a DNS query for a known malicious domain/URL and causes the malicious domain name to resolve to a definable IP address (fake IP) that is given to the local server.
Let’s understand DNS and Malicious attacks first…
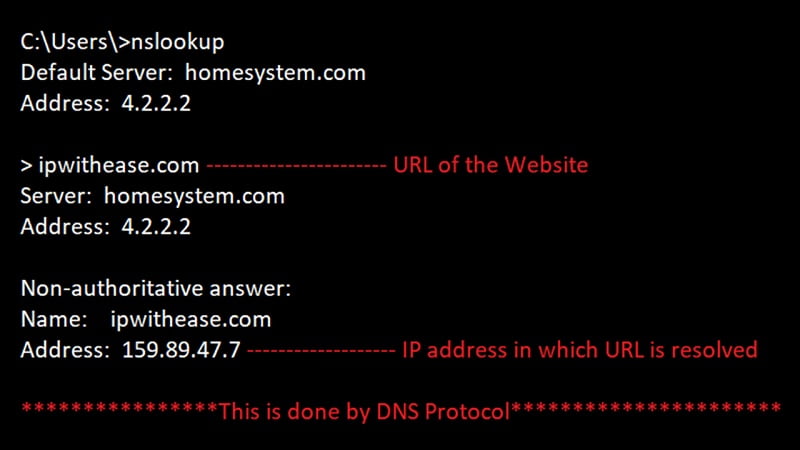
DNS (Domain Name System) is a protocol which is used to access the internet. Basically, DNS protocol route s the domain name with IP address over the network. It is a database in which information of internet hosts/hostname is mapped with IP address and vice-versa. The purpose of DNS is to resolve domain names (like ipwithease.com) to IP addresses (159.89.47.7). Below is an example whereby using the “nslookup” command, a query is raised to the designated DNS server inquiring about the IP of the URL or Website (In this case “ipwithease.com”). The response given by the DNS server is respective IP of ipwithease.com i.e. “159.89.47.7”.
Now-a-days internet traffic is very prone to attacks, specifically malware attacks. Infact, it is a cyberattack which performs unauthorized actions on a user’s machine/system or any network by using false links/emails. Attacker sends a malicious URL to a user in the form of a link or email which directs traffic to a malicious or otherwise fraudulent web page or website. And whenever traffic goes to the internet, it uses a DNS server to communicate with malicious websites/normal sites (as DNS server changes URL to IP address – which is routable format).
Here, DNS Sinkhole plays an important role as it is used to spoof DNS servers to deter resolving hostnames of specified URLs. DNS sinkhole is used by organisations to prevent communication of user traffic to malicious websites.
Moreover, when a user tries to access a sinkhole URL (fake/false URL configured locally), a customized web page can be shown. This web page can be created with customised corporate policy restriction messages and can be hosted on a local server.
How DNS Sinkhole works?
We can understand the DNS Sinkhole scenario by comparing two networks, one in which a normal DNS server is installed in the network whereas another network has DNS Sinkhole implemented in it.
Below diagram (Fig 1.1) illustrates Phishing attack in a Network.
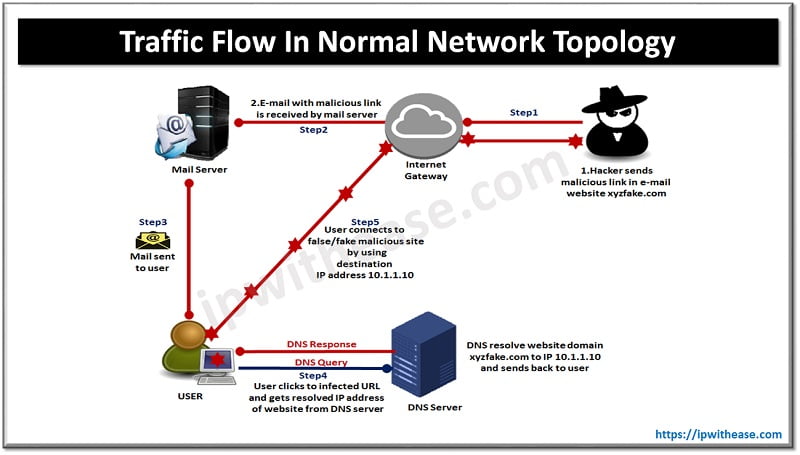
(Figure 1.1 – Traffic Flow In Normal Network Topology)
Phishing emails are one of the most used types of scam emails. A phishing fraud happens when the fraudster tries to fool someone with the intention of stealing sensitive data. E.g., sending malicious links/attachments to someone. Spelling and grammar errors (appple.com, extra “p” in name ) indicate frauds in email and such kind of emails are commonly used by hackers.
The hacker sends an email to the user in which some malicious link or attachment is shared.
Next, the user is enticed into downloading the attachment or clicking the link or providing sensitive information to the attacker. Phishing link will be redirected to another website where a cyber attacker captures the user’s data.
One way to get familiar with their tactics is to carefully study the email messages that scammers sent.
Figure 1.2 illustrates how DNS Sinkhole works when a user clicks on the malicious link.
DNS sinkhole interrupts the DNS request and responds with an authoritative answer configured by the company.
Step-by-Step process of DNS Sinkhole
- User receives an email along with some known URL in it (let’s suppose URL name is password-reset.com)
- User clicks on the URL
- User machine sends DNS Query to DNS
- DNS validates that URL comes under malicious list (Malicious URL list is configured in server)
- DNS server responds with DNS Sinkhole IP which is an address of any isolated server where all malicious/suspicious URLs are redirected by DNS server.
- Moreover, an Information Security message will prompt on the user system which notifies the initiator that the submitted URL is a malicious link.
As shown in the below figure (1.2), during step 4 (steps 1, 2 and 3 remain same as previous diagram), Malware on the compromised client tries to initiate connection to website xyzfake.com hosted on 10.1.1.10, which is a known suspicious domain configured in the DNS Sinkhole. User traffic hits DNS Sinkhole, which hijacks the DNS query and responds as sinkhole IP address to the user along with customized company threat policies.
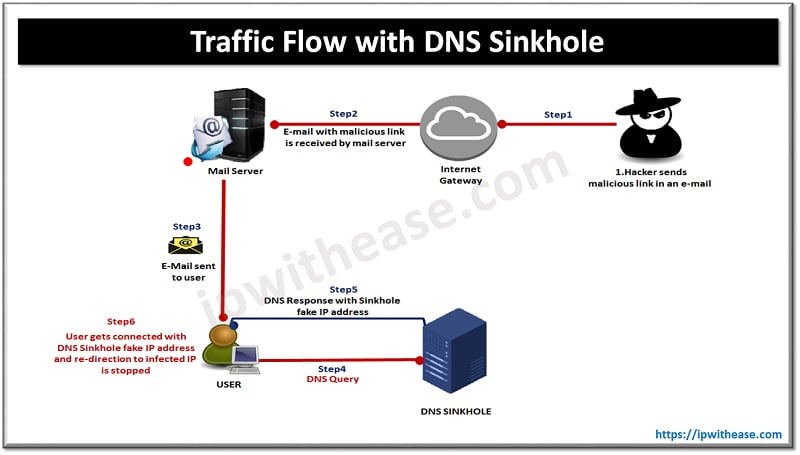
(Figure 1.2 – Traffic Flow with DNS Sinkhole)
Prerequisites to deploy DNS Sinkhole in Network
- Malicious traffic should pass through internal DNS server
- DNS Sinkhole feature must be configured in Firewall (Palo Alto, Cisco, Juniper etc.) if the internal DNS server is not parsing malicious traffic.
- A DNS sinkhole can only detect the infected system, it cannot prevent malware from being replicated or cloned to other systems.
- DNS Sinkhole traffic needs to forward to threat analyser for further analysis of logs, hence log analyser is required to examine the suspicious traffic.
- DNS Sinkhole server should be placed in an isolated zone so that external network attackers cannot identify the fact that their traffic has been mitigated and monitored.
Limitations of DNS Sinkhole
- Sometimes non-suspicious websites/URLs might be marked as malicious depending on their behaviour. This might cause a big issue in an organization by blocking connections to useful sites. Such cases are called False Positive alerts.
- While maintaining an external sinkhole service/third-party server, organization network information like IP, user-ID, LAN subnets etc. will be logged in the third-party server which is like providing all the data of the organization to a doubtful server.
Conclusion
DNS sinkholes are useful for day-to-day network operations and management, threat log analysis, and overall security, as well as a research tool to improve their ability to identify threats in the network and prevent attacks. It makes log analysers an important weapon in the cyber security stream.
Continue Reading:
SASE (Secure Access Service Edge): Cyber Security
Spear Phishing Attack: Cyber Security
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj