Table of Contents
One key aspect of network and security engineer is to have a good understanding of well-known services and their port numbers (TCP and UDP).
What is a TCP Port?
A TCP port is a numerical identifier in networking used to specify a particular service or application on a device. Ports, combined with IP addresses, help direct traffic to the correct destination and process. There are 65,536 possible TCP ports, ranging from 0 to 65,535. Ports 0 to 1023 are considered well-known or system ports, while ports 1024 to 49151 are registered ports. Ports 49152 to 65535 are known as dynamic or private ports.
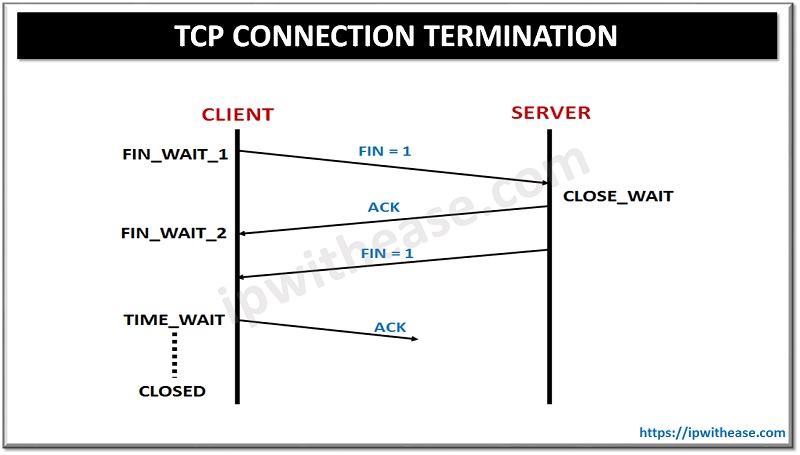
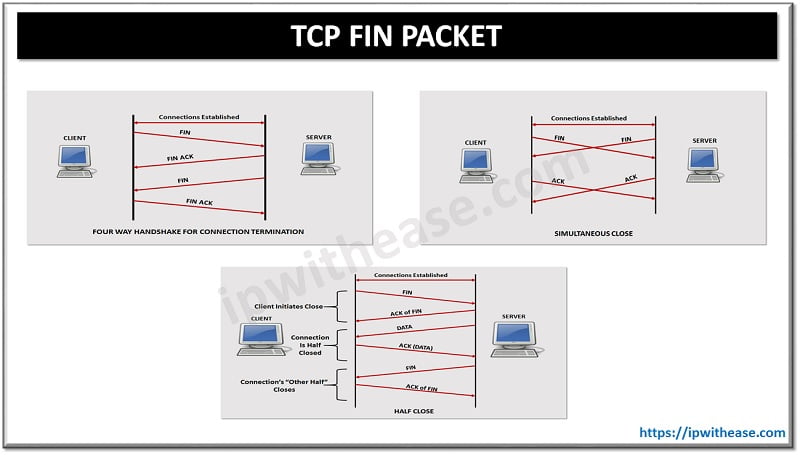
Difference between TCP and UDP ports
TCP (Transmission Control Protocol) is connection-oriented, meaning it ensures that data is received in the correct order. UDP (User Datagram Protocol) is connectionless, meaning it sends data without establishing a connection or guaranteeing order, which can result in faster transmission but less reliability.
List of TCP Port Numbers Information
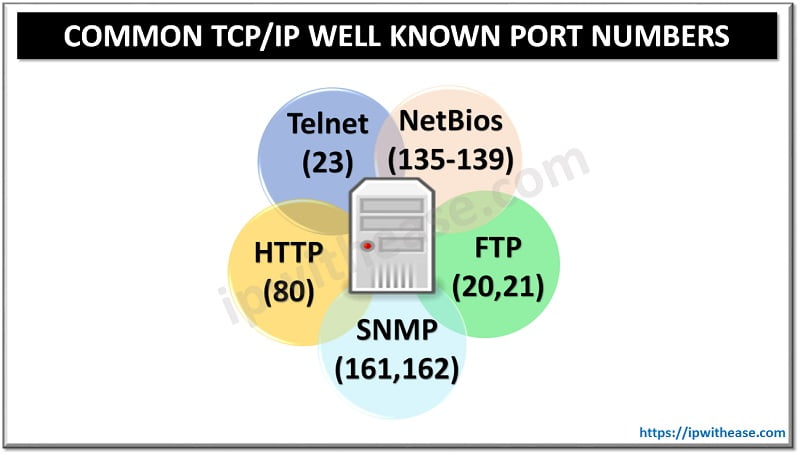
Below is a list of commonly used well-known protocols and their port number. Additionally, RFC reference will help to have more detail on the enlisted transport-layer common port numbers:
Related- TCP vs UDP
| PORT NUMBER | TRANSPORT PROTOCOL | SERVICE NAME | RFC |
|---|---|---|---|
| 20, 21 | TCP | File Transfer Protocol (FTP) | RFC 959 |
| 22 | TCP and UDP | Secure Shell (SSH) | RFC 4250-4256 |
| 23 | TCP | Telnet | RFC 854 |
| 25 | TCP | Simple Mail Transfer Protocol (SMTP) | RFC 5321 |
| 53 | TCP and UDP | Domain Name Server (DNS) | RFC 1034-1035 |
| 67, 68 | UDP | Dynamic Host Configuration Protocol (DHCP) | RFC 2131 |
| 69 | UDP | Trivial File Transfer Protocol (TFTP) | RFC 1350 |
| 80 | TCP | HyperText Transfer Protocol (HTTP) | RFC 2616 |
| 110 | TCP | Post Office Protocol (POP3) | RFC 1939 |
| 119 | TCP | Network News Transport Protocol (NNTP) | RFC 8977 |
| 123 | UDP | Network Time Protocol (NTP) | RFC 5905 |
| 135-139 | TCP and UDP | NetBIOS | RFC 1001-1002 |
| 143 | TCP and UDP | Internet Message Access Protocol (IMAP4) | RFC 3501 |
| 161, 162 | TCP and UDP | Simple Network Management Protocol (SNMP) | RFC 1901-1908, 3411-3418 |
| 179 | TCP | Border Gateway Protocol (BGP) | RFC 4271 |
| 389 | TCP and UDP | Lightweight Directory Access Protocol | RFC 4510 |
| 443 | TCP and UDP | HTTP with Secure Sockets Layer (SSL) | RFC 2818 |
| 500 | UDP | Internet Security Association and Key Management Protocol (ISAKMP) / Internet Key Exchange (IKE) | RFC 2408 – 2409 |
| 636 | TCP and UDP | Lightweight Directory Access Protocol over TLS/SSL (LDAPS | RFC 4513 |
| 989/990 | TCP | FTP over TLS/SSL | RFC 4217 |
Download the table: List of TCP Port Numbers
Related FAQs
What happens if a port is blocked?
If a port is blocked by a firewall or security software, the specific service or application using that port will not be able to communicate over the network. For example, if port 80 is blocked, users may not be able to browse websites using HTTP.
How can I check which ports are open on my system?
You can check open ports using network utilities like:
– netstat: To view active connections and listening ports on a system.
– nmap: A powerful tool for network scanning and auditing.
– telnet: To check if a specific port is open by trying to connect to it.
What is port forwarding?
Port forwarding is a network configuration that redirects incoming traffic on a specific port to another IP address and port. It’s commonly used to allow remote access to services running inside a private network.
Are there reserved TCP ports that I should avoid using?
Yes, ports 0 to 1023 are reserved for system or well-known services, so it’s generally recommended to avoid using these for custom applications unless needed. Registered ports (1024 to 49151) are also associated with specific services but are available for general use.
Why are some TCP ports considered insecure?
Some ports are considered insecure due to vulnerabilities in the services running on them or their susceptibility to attacks. For example, Telnet (port 23) is insecure because it transmits data in plaintext, making it vulnerable to eavesdropping.
How do I secure TCP ports on my network?
You can secure ports by:
– Using a firewall to block unnecessary or unused ports.
– Using secure versions of protocols (e.g., using SSH instead of Telnet).
– Keeping software and services up to date to prevent vulnerabilities.
– Implementing intrusion detection/prevention systems (IDS/IPS) to monitor port activity.
Continue Reading
Difference between IP Address and Port Number
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj