Table of Contents
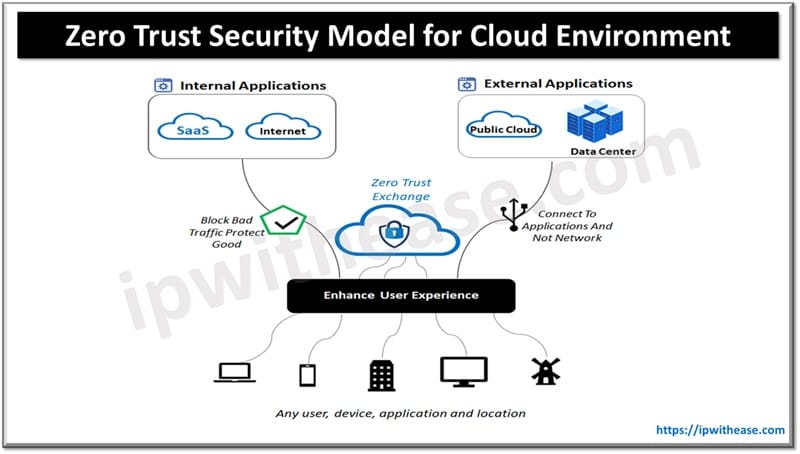
The world of cyber threats is always shifting and keeping cloud environments safe is getting harder. The old thought was that if something was inside the network, it was safe. But that just doesn’t work anymore. The Zero Trust security model changes how things are done by sticking to a “never trust, always verify” rule. Basically, every user, device, and app has to be checked out and approved all the time before they can access anything. Since cybersecurity is such a big deal, really getting to know and using the Zero Trust model is super important for keeping your cloud environment secure.
Cybersecurity itself is one of the most interesting science topics today, as it blends elements of computer science, artificial intelligence, and behavioral psychology to outsmart cybercriminals. The Zero Trust model is a prime example of how scientific advancements in security strategies continue to evolve to counteract sophisticated digital threats.
Understanding the Core Principles of Zero Trust
Before we understand how to set things up, we must grasp what Zero Trust is all about. This model relies on three main ideas: check everything, give the least access needed, and always assume someone’s trying to break in. Checking everything means you need to confirm who’s trying to get in by looking at different things like who they are, how secure their device is, and where they’re coming from. Giving the least amount of access means users and apps only get the permissions they need to do their job, which helps limit any damage if an account gets hacked. Lastly, assuming a breach means always monitoring network activity and segmenting systems to reduce the impact of potential security incidents.
Identifying and Classifying Cloud Assets
A successful Zero Trust implementation starts with identifying all assets in your cloud environment. These assets may include cloud applications, virtual machines, databases, APIs, and storage services. Sorting your data by how sensitive and important it is can help you focus your security efforts. Knowing where your most valuable information is helps you devise better protection plans so that your high-risk stuff gets the tightest security.
Implementing Strong Identity and Access Management (IAM)
Keeping track of who can get in is super important in a Zero Trust approach. Identity and access management tools are key for checking who’s using the system and what devices they’re on. It’s a good idea to make multi-factor authentication a must. This adds another layer of safety since users have to prove who they are with more than just a password. Role-based access control is another way to tighten security. It gives permissions based on what someone does at their job instead of who they are, cutting down on the chances of giving too many rights. Plus, you can use just-in-time access to hand out temporary permissions only when needed and then take them away right after. Keeping an eye on user activity all the time can also help spot anything weird that might show there’s a security issue.
Securing Network and Data Traffic
Zero Trust is all about keeping all your network traffic safe. Microsegmentation enhances cloud security by breaking down the network into smaller segments, restricting the lateral movement of potential intruders. This approach keeps a security breach limited to just a small part so it doesn’t go all over the place. Also, by encrypting data when you send it and when it’s stored, you’re making sure it stays safe from prying eyes even if someone tries to grab it. And let’s not forget about API security since APIs are often targets for attacks. Setting up secure API gateways with strong authentication, authorization, and monitoring can help block unauthorized access and keep your data safe from leaks. Plus, using security tools that leverage AI can really boost your monitoring game, spotting unusual activity in real-time and catching suspicious behaviors before they turn into bigger problems.
Ensuring Device and Endpoint Security
Every device that accesses a cloud environment must meet security standards to prevent vulnerabilities. Implementing device posture checks ensures that only compliant devices gain access. This means requiring endpoint security software, up-to-date patches, and encrypted storage. EDR tools help boost security by spotting and handling threats on single devices. Keeping your systems updated and patched is super important too since systems that aren’t updated often give attackers a way in. Ensuring that all endpoints remain up to date significantly reduces security risks.
Automating Security Policies and Monitoring
Keeping a Zero Trust approach in place means you need to keep an eye on things all the time and automate as much as you can. That’s where Cloud Security Posture Management tools come in handy. They constantly check your cloud security settings and make sure you’re following the best security practices. Security Information and Event Management systems help by gathering security logs in one place, which makes spotting weird activity or potential threats across different cloud setups a lot easier. Plus, with automated responses powered by AI, you can tackle threats right away without having to do everything by hand. This lets your security teams focus on bigger picture tasks instead.
Continuous Testing and Improvement
Zero Trust isn’t just something you set up once and forget about. It’s an ongoing journey that needs regular check-ins and tweaks. Doing security audits every now and then helps spot any weak spots in your current rules and setups. Penetration testing, which is like running practice attacks, gives you a good look at any vulnerabilities that need fixing. Keeping your security rules updated often makes sure your system can handle new threats and stay in line with any regulations. As cyber threats keep changing, being proactive and always working on your security is the only way to keep your cloud environment tough and ready.
Final Thoughts
Using a Zero Trust security model for your cloud setup is a smart way to protect your sensitive info and keep out the bad guys. By making sure everything is verified all the time, breaking up your networks, and having strong access controls, companies can really lower their security risks. Plus, automation makes things even better by simplifying how you keep an eye on things and respond to issues. Just keep in mind that Zero Trust isn’t something you set and forget; it needs ongoing tweaks. Staying on top of your security rules, checking the system often, and adjusting to new threats will keep your cloud secure in this ever-changing world.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.