Table of Contents
Even as payment security technology advances, malicious parties can always take advantage of human imperfections to gain access to sensitive information. With credit cards and other cashless alternatives continuing to gain popularity, we’ve seen an uptick in human-focused crimes that exploit human psychology to manipulate people into divulging confidential information, both online and offline.
These social engineering attacks are nothing new, with different forms of this kind of fraud having existed for centuries. With every new advancement in technology, fraudsters have found more tools to steal information and money from innocent consumers.
Fortunately, nowadays, it’s easy to find the safest credit card for online shopping. That being said, even the most secure credit cards require vigilance from cardholders to prevent fraud.
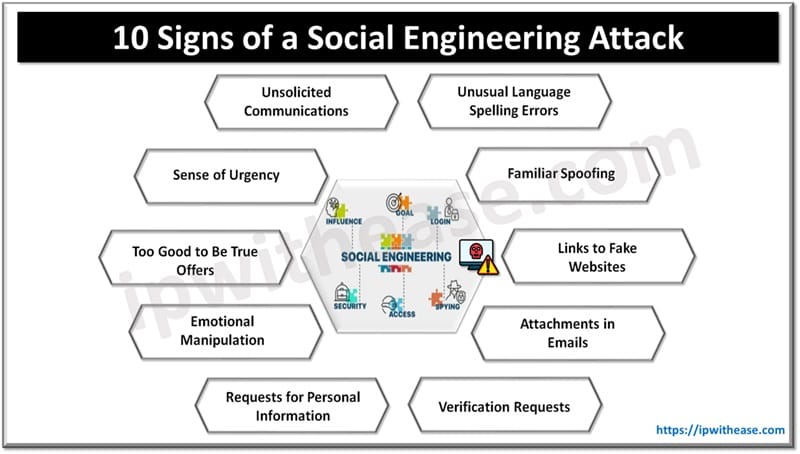
Signs of a Social Engineering Attack
Be sure to watch out for these online and offline signs of social engineering attacks that are meant to steal your credit card information:
1. Unsolicited Communications
If you receive unexpected emails, phone calls, or messages from unknown sources, you should be automatically wary. This is especially true for those requesting personal information or immediate action. In particular, watch out for promises of “prizes” for contests you never entered.
2. Sense of Urgency
Social engineering attacks often induce a sense of urgency to pressure you to act without thinking. Phrases like “Your account will be locked in 24 hours” are especially common red flags, particularly if you’ve done nothing to set off such an action.
3. Too Good to Be True Offers
Beware of offers that seem excessively generous or unrealistic, such as very low interest rates or instant prizes simply by filling out a form. Again, if you did nothing to warrant the offer, it’s probably a scam.
4. Emotional Manipulation
Attackers might use emotional appeals, such as claiming a family member is in trouble, to manipulate you into divulging information. These tactics are often through online channels, where it can be difficult to prove one’s identity, but they can also happen in person.
5. Requests for Personal Information
Requests for sensitive information, such as your credit card number and CVV, passwords, or government ID numbers are red flags. These must be disregarded immediately.
6. Unusual Language or Spelling Errors
Many social engineering attempts originate from non-native English or Filipino speakers. As a result, they may contain grammatical mistakes, awkward phrasing, or spelling errors. Make it a habit to double- or even triple-check texts and emails to make sure nothing is amiss.
7. Familiar Spoofing
A cyber attacker employing all the other above-mentioned techniques may also impersonate someone you know or an organization you do business with. They may use familiar logos, email addresses, or names to gain your trust and get you to divulge credit card details. Be very cautious if the person or business you think you know is speaking out of character.
8. Links to Fake Websites
Never accept or clink links in emails, texts, or chat messages from people you don’t know. These links will usually redirect you to websites that look legitimate but are designed to steal your information. If you get a suspicious message, don’t click and check the URL carefully for discrepancies.
9. Attachments in Emails
Unknown attachments are exceptionally dangerous since they may contain trojans or other malware that could not only compromise your information, but also do untold damage to your phone or computer.
10. Verification Requests
Lastly, scammers may ask you to “verify” your credit card details, often under the guise of a security check. It’s extremely rare for legitimate companies to request sensitive information this way, if at all. So, if you receive this request and never contacted the business in the first place, check for other red flags that may indicate a scam.
Pointers on Keeping Your Credit Card Details Safe
- Use Strong, Unique Passwords. Complex passwords are your first step in securing your credit card information and other online accounts, even from social engineering attacks. Simple passwords can often be inferred by savvy attackers, making them unsuited for modern data security needs.
- Enable Two-Factor Authentication (2FA). Where available, enable 2FA for an added layer of security. 2FA requires a second form of verification in addition to your password, such as a code sent to you via text message or email. Setting up 2FA ensures that no one can access your details unless they have a physical possession of your devices.
- Monitor Your Accounts Regularly. Regularly check your bank and credit card statements for any unauthorized transactions. Immediately report any suspicious activity to your bank.
- Be Cautious with Public Wi-Fi. Public Wi-Fi networks can be compromised by hackers or be intentionally set up by data thieves to steal your card information. If you need to make online transactions in public, use your data plan or set up a virtual private network (VPN) for a more secure connection.
- Stay Informed! While human nature remains fairly constant, both technology and the scams evolve all the time. Take the time to read the latest cybersecurity news and consider subscribing to your card provider’s email newsletter to learn the latest about social engineering attacks.
Secure Your Card and Financial Future from Human-Targeted Attacks
Social engineering attacks are about as old as our species. So long as there are systems with protections that demand imperfect human vigilance, they will always be vulnerable to bad-faith actors. Fortunately, being aware of the signs of typical social engineering attacks will give you the means to better secure your card information. Since malicious parties are likely to prioritize users with poor data security, even modest best practices like the ones we shared should be enough to prevent most potential issues, especially if they’re followed judiciously. Stay vigilant and you’ll enjoy a secure yet still convenient credit card experience for years to come.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.