Table of Contents
Due to mass scale cloud penetration and hosting of business applications over the web have increased the cyber security threats tremendously. Organizations are focusing on securing their business applications along with maintaining the performance metrics. Web applications like any other local applications are prone to vulnerabilities and components weaknesses which may arise due to lapses during the software development lifecycle stages, poor coding practices, lack of adequate testing, using end of life or end of support technologies and frameworks in developing applications.
In today’s topic we will learn about Web application security tools, their purpose, characteristics, their importance and types of threats they help to identify, mitigate and block.
Web Application Security
Before we do a deep dive into web application security it is important to understand what web application security is and why it is so important for organizations and businesses who use them. It is equally important for service providers and vendors of applications to ensure their software is securely built and provide adequate protection for data stored or processed by them.
Web application security popularly known as WebAppSec is the idea to build websites, applications in a secure way and ensure they function AS-IS even under attack. There are collections of security controls combined together and engineered into the web application so as to protect its assets from malicious threat actors.
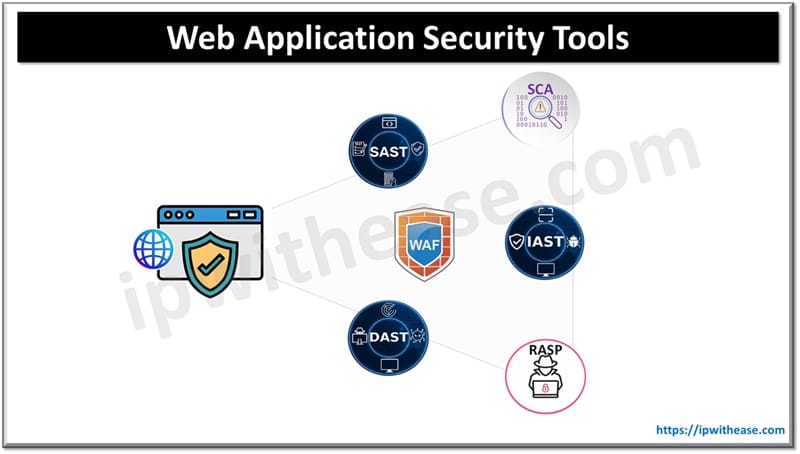
Common Web Application Security Risks
Let’s look at some popular web application security risks:
Zero-day Vulnerabilities – Unknown vulnerabilities or flaws in the application for which fix is not available can be exploited by bad actors. There are more than 20,000 zero-day exploits every year.
Cross-Site scripting (XSS) – It is a vulnerability which allows the attacker to inject client-side scripts into the application to gain access to sensitive information , impersonating the legitimate user or tricking the user to reveal confidential information.
SQL Injection (SQLi) – It is a vulnerability in which an attacker exploits vulnerabilities by way of a database search. Using SQLi, attackers gain unauthorized access to the system, modify or create new user permissions, or manipulate or do data destruction.
Denial of Service (DoS) or Distributed Denial of Service (DDoS) – Attackers overload the targeted system or its network using attack traffic. When the server is no longer able to handle the volume, it crashes and stops handling the incoming requests.
Cross Site Request Forgery (CSRF) – Here attackers trick users to make a request for authentication and authorization by leveraging account privileges masquerading as the user.
Web Application Security Tools
Web application security tools perform a variety of scans and help in identifying, blocking and preventing exploitation of vulnerabilities. Let’s look at some key tools in this space which help in prevention of web application vulnerabilities.
Static Application Security Test (SAST)
This tool analyses application source code during the development stage and helps in detecting coding and design deficiencies which could lead to vulnerabilities. e.g. Burp suite, Veracode
Dynamic Application Security Test (DAST)
These tools analyze code at runtime including the underlying framework and systems. It needs manual configuration of DAST for each application under testing. e.g. Qualys scanner
Software Composition Analysis (SCA)
These tools analyze applications for identification of open source software (OSS) and third-party components used in applications having vulnerabilities or licensing restrictions.
Interactive Application Security Test (IAST)
These tools observe behaviour of applications such as input, data flow, logic and output. The IAST agents are deployed in application to perform runtime analysis of these components including memory.
Let’s look at some tools which help in block attacks targeted to web applications:
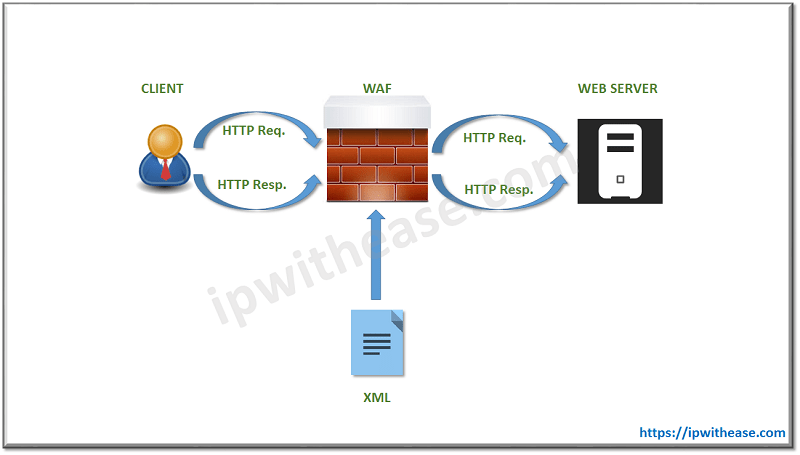
Web Application Firewall (WAFs)
These are software-based gatekeepers which protect applications against malicious HTTP traffic. They place a filter between attackers and web application servers and block traffic which is malicious such as SQL injection, CSRF and XSS.
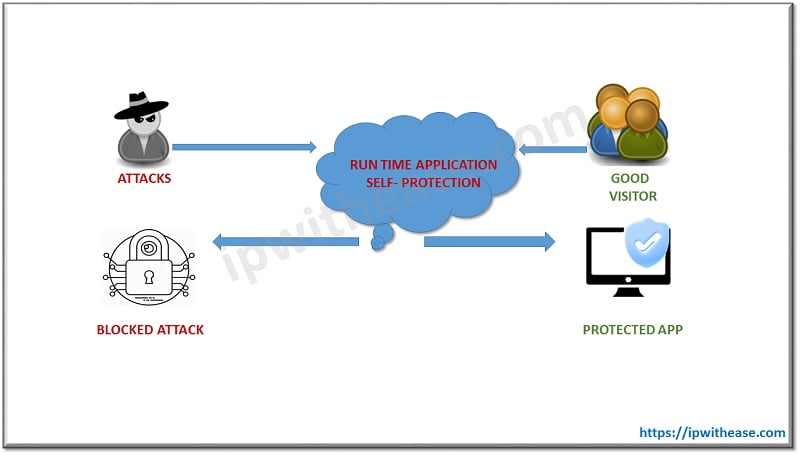
Runtime Application Self-Protection (RASP)
These tools detect and block malicious attacks by implementation of in application instrumentation. SDK is used to integrate RASP directly into codebase or deploy agents on host at runtime.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj