Table of Contents
‘Cyber attacks’ does this ring a bell in your ear and what about ‘AI-powered cyber attacks’ does this ring the bell more loudly?
The role of Artificial intelligence or AI in cyber attacks can no longer be ignored anymore. Both attackers and defenders use AI as a medium to meet their objectives, good or bad. Using AI powered tools the magnitude of cyber-attacks can be intensified and doubled by threat vectors. These cyberattacks exploit AI capabilities to learn, adapt and execute complex tasks more accurately and at a speed compared to humans.
AI capability to learn and process vast amounts of data is a powerful mechanism to optimize malicious activity and outperform traditional defence mechanisms used so far in protection of organization data from malicious actors.
In this article we will learn about AI powered cyber-attacks, types of AI based cyber-attacks, challenges in defending against AI powered cyber-attacks, Defensive measures and practises to stay ahead.
AI-Powered Cyber Attacks
In 2024, the cost of cyber attacks to businesses reached $9.5 trillion world wide and experts claim that it would reach $10.5 trillion by year 2025. AI has revolutionized AI and cybersecurity. AI driven tools are used by cybercriminals to launch AI based sophisticated cyber-attacks. AI powered phishing mails, malware are hyper-personalized, accurate mimicry of trusted contacts. AI generated deep fake voices are used in 15% CEO fraud cyber attacks in the year 2024. AI is used to steal credentials without involving user interaction. There are a variety of AI powered attacks being launched. We will look into them more in detail here.
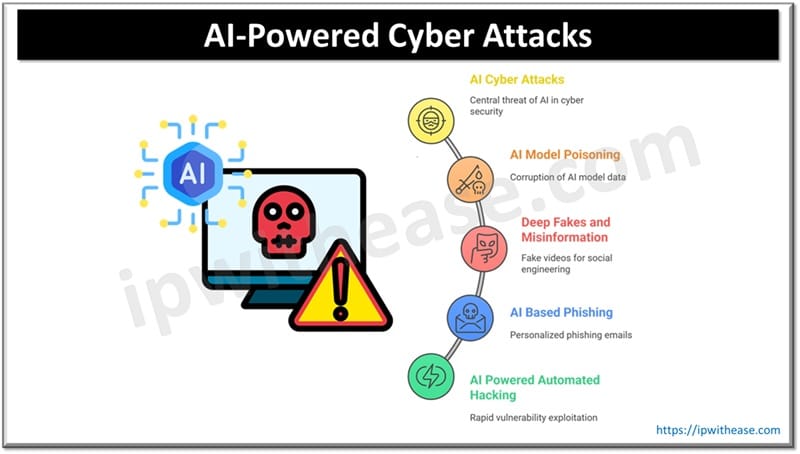
Types of AI Cyber Attacks
AI Powered Automated Hacking
With aid of AI algorithms vulnerabilities can be detected and exploited at the speed of light as compared to humans. With the use of AI enabled scanners, threat actors can scan and discover undisclosed vulnerabilities quickly and systems can be compromised in a few seconds or minutes.
AI Based Phishing
More sophisticated and personalized phishing mails can be created using AI tools and techniques. AI is used to create more authenticated and personal phishing mails. Data coming out of social media is analyzed by AI and used to generate highly customized messages for its targets.
DeepFakes and Mis-information
Highly realistic fake videos are generated using AI and impersonate the victim to spread misinformation and conduct a social engineering attack
AI Model Poisoning
Corruption of data fed into AI models will manipulate the outcome or output from the model. This is concerning where crucial systems are involved which could lead to severe damage
Defensive Measures and Best Practices to Stay Ahead
To stay ahead in this game of cat and mouse, it is important to evolve cyber security defense strategies, establish a robust data governance and train employees and the public about AI powered threats and deep fakes.
Be you are a developer or business professional, IT engineer or a common user it is important to understand these threats and help in strengthening cyber security posture:
- Zero Trust Architecture – ‘Verify and trust no-one’ should be the current principle. verification of each device and user identity irrespective of where it is operating from. (location does not matter)
- AI Powered Cyber Tools – Invest in AI powered cyber security tools such as threat detection, vulnerability management, incident response etc. AI based threat detection systems process data and detect anomalies and patterns of indicative threats, user behavior monitoring using AI behavior analytics tool can be used to detect variations in established norms, Incident response powered with AI can help in assessing risk severity, prioritization of actions, AI powered real time threat intelligence solutions help in analyzing threat data and mitigate threats in real-time.
- Training Your Employees – Recurring training and awareness programs help in reduction of phishing attacks.
- Secure Your Code – Use tools such as SonarQube, Veracode etc to scan your software code and libraries on ongoing basis
- Collaborate with Cyber Security Experts – Engage with industry experts to get insight into latest threat vectors
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj