Table of Contents
As technology is advancing and more and more organizations are moving to cloud computing, using AI in their services and applications the threat landscape is also expanding exponentially. With cyber attacks on rise, application security is a major concern for today’s enterprises.
Threat modelling is a way to build into the design stage itself security in application. Threat modelling can be undertaken at any stage of application development but if it is done from the inception of the product it helps in early determination of the threat landscape application would face eventually.
It identifies, communicates and understands the latest threats and helps in deriving mitigation strategies in the early stages of development.
In this article we will learn more in detail about Threat modelling, how threat modelling works? why threat modelling is important, its benefits, understand malicious proxies and mitigation techniques.
What is Threat Modelling
In threat modelling methodology an application and data is secured by analyzing hypothetical scenarios, system diagrams and testing techniques. Identification of security vulnerabilities help in risk assessment, mitigation and strengthen the cyber security posture of an application. However, threat modelling also considers all other kinds of threat such as floods, earthquakes, theft etc. which can disrupt business and find a way to address them.
How Threat Modelling works
Let’s look at steps in detail to define a threat model.
- Determine the scope – firstly determine how much deep dive you want to do in your organization’s security structure. Initially keep it simple if you are doing this for the first time.
- Identification of assets – identity the systems, applications and intellectual property you want to keep in scope
- Identify potential threats – identify potential threats such as hackers, malicious insiders, natural disasters, man-made disasters , technical issues and so on.
- Identifying vulnerabilities – since in earlier step you identified assets and potential threats you will be able to figure out which design controls you need to strengthen here
- Assess the risks – for each of the assets , identified threats due a deep dive and consider evaluating the likelihood and impact of each of these identified threats
- Mitigate risks – once we identify design deficiencies, threats and their likelihood we need to derive mitigation strategies to improve design, eliminate vulnerabilities, establish strong encryption, and robust incident response plans.
- Refinement and validation – establish a process to periodically review and validate, update your threat model as systems evolve and the threat landscape is ever changing.
What are Malicious Proxies
As more and more organizations and individuals rely on proxies for security, secrecy and evading regional restrictions there is a risk of malicious proxies which are used by hackers to launch attacks, data breaches, or any other illegal activities.
The malicious proxies are dangerous as they employ reverse proxy and cookie injection techniques to bypass MFA or 2FA. The malicious proxies operate on the principle of reverse proxy where a hacker leads the end user tricking into clicking a malicious URL which looks like a legit URL /link. When the end user tries to login using their credentials on a fake web page the proxy forwards authentication request to the malicious page and thereby capturing the credentials using a cookie injection technique.
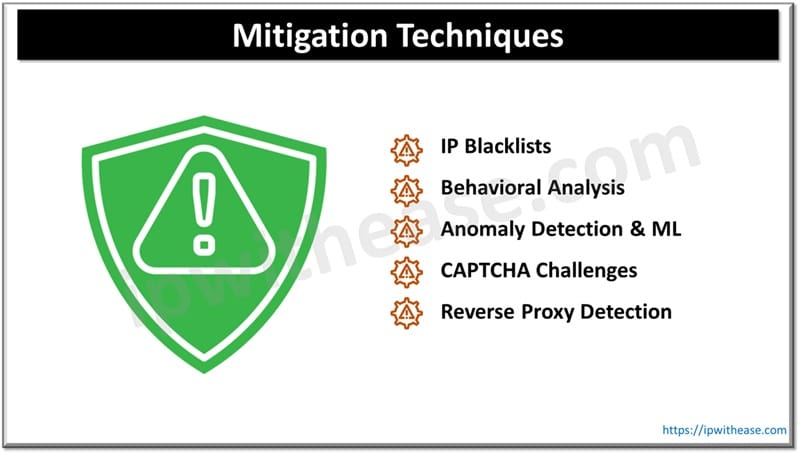
Mitigation Techniques
IP Blacklists
This is the most commonly used method to detect malicious proxies. IP blacklists have a list of all known malicious IP addresses which enable organizations to block traffic from these blacklisted IP addresses. These blacklisted IP addresses are derived from a real-time threat intelligence feed that can help to reduce risk of false positives and block known malicious IP addresses.
Behavioral Analysis
It involves monitoring behavior of incoming web traffic and pattern identification with malicious proxies. For example, unusual web traffic or repeated connection requests coming from a specific IP address could indicate a malicious proxy involvement.
Anomaly Detection and Machine Learning
These emerging techniques have drastically improved the malicious proxy’s detection as these help in identification of anomalies in network traffic which is not usually identified in manual analysis due to its sheer volumetric. A machine learning program can ear-mark an IP address as suspicious if it shows patterns of frequent user agent changes and irregularity in geolocation data.
CAPTCHA Challenges
CAPTCHA challenges can effectively deter multiple login attempts or automatic scrapping.
Reverse Proxy Detection
Detect usage of reverse proxies which often hide their origin by examination of HTTP Headers.
Threat intelligence sharing with other organizations and cybersecurity communities help in effective detection of emerging threats and malicious proxies.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj