Table of Contents
Introduction to Cisco ACI Tenant
Cisco Nexus ACI is the de-facto preferred fabric solution for the data center environment. Application Centric Infrastructure has introduced many terms that network community is not so much familiar to. Hence, in this article, we shall touch-base on ACI Tenant and related key components.
Traditional Network Approach
However, before explaining Tenants, a quick reference to Traditional network approach is imperative –
- If we wish to separate the traffic, then segmentation should be based on either L2 (VLAN or MAC) or L3 (IP subnet), which means one department traffic is segregated from another department using VLAN’s.
- If we wish to implement policy (QoS, ACL, and Segmentation) on a server, it will be configured on L3 hop (which is the gateway device), further based on the policies forwarding decision can be made. Since policies are built based on the IP subnet or VLAN’s, therefore if IP subnet or VLAN changes occur, all the policies such as QoS, ACL, Segmentation will become ineffective and consequently, policies need to be updated or new ones configured. The traditional network has a dependency on the IP subnet or on VLAN’s where applications are recognized by their IP address or VLAN’s.
- In order to have a common broadcast domain for a set of services like Web or APP or DB, a general understanding is to consider one network having one VLAN. We map services like APP/ DB/ Web with IP address. Therefore, it is right to say that servers are not recognized by their services but by their IP address in traditional network setups.
Related- Cisco ACI
Cisco ACI Approach
Contrary to above-described scenarios, ACI will not perform segregation based on VLAN’s, instead, it uses Tenants and VRF’s (Private Network) to provide IP address isolation. End Point Groups are used for grouping of policies on an object. Bridge Domains are used to provide multicast and broadcast isolation (like VLANs). All these components are required to contain routed traffic.
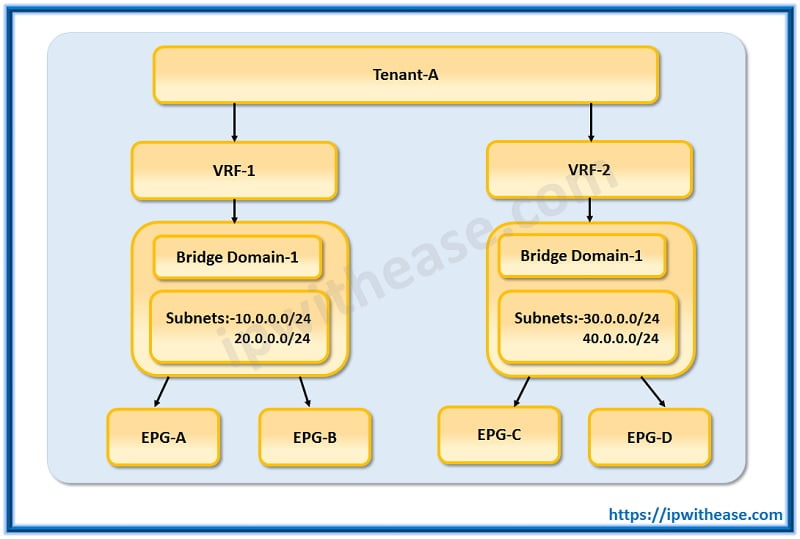
Subsets of Tenants: VRF’s/ Bridge Domain/ EPG’s
Private networks have a direct relationship with Bridge Domain’s, while others are parent-child relationships. Subnets and Bridge domains are a child of Tenants. As shown in the above diagram, Tenant may have multiple Private Networks and Private Network may be linked to multiple bridge domain and in the same way, Bridge domains may have multiple child subnets.
Below is the detailed information on the components
1. Tenants
It refers to a logical unit for management. Tenants can be customers, business units (BU’s), groups who have separate administration and data flows. Tenants provide secure and exclusive virtual computing environment and can contain Multiple Private networks (VRF Instances). Tenants allow re-use of IP address space; multiple tenants may have the same subnets.
Let’s take an instance where a company has multiple departments (sales, HR, Marketing) in their network and all departments require separation from their business and operational boundaries. Tenants would help to create different departments with their own private network. One tenant cannot talk with another tenant.
Cisco ACI Tenant
By default, we have three ACI tenants in Cisco:
- Common Tenant: Provides common services to all tenants, shared L3/ Shared Private network/ shared bridge domains/ DNS/ DHCP/ Active directory.
- Infra Tenant: Internal Fabric communication is possible with this tenant, which includes interaction between the switch to switch (leaf, spine, Application Virtual Switch (AVS)) and switch to Application Policy Infrastructure Controller (APIC). The Infra tenant does not have any relationship with user space (tenants) and it has its own private network space and bridge domains.
- Tenant: Used for in-band and OOB management. It allows us to configure access policies for fabric nodes. With the help of mgmt. tenant, we can access fabric nodes.
2. Private Network (VRF)
It provides IP address space isolation for tenants. We can define one or more layer 3 networks (VRF instances) and one or more bridge domains per network.
3. Bridge domain
It refers to a container that carries multiple subnets. BD also refers to the default gateway of subnets. It cannot be considered as VLAN since it carries multiple subnets, however, it is similar to the VLAN layer 2 broadcast domain. It can be considered as advance VLAN, which has multiple subnets in a single broadcast domain. Suppose we have 1000+ SQL servers and administratively they all need to be in a single group since they are having the same policies. Using a bridge domain we can group all the same in one domain without any L3 routing.
4. EPG (End Point groups)
An End Point Group (EPG) is a group of End Points that require common services and policies, such as a server farm.
Continue Reading
Cisco ACI Benefits over VMware NSX
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj