Table of Contents
What is AES (Advanced Encryption Standard)
AES (Advanced Encryption Standard) is a type of encryption which is easy to use and secure for every communication. It is a symmetric type of encryption; the same key is used for encryption and decryption.
AES has been chosen to replace DES, as DES is a weak encryption and easily breakable by an attacker hence in 2001 NIST released FIPS 197 which mandates the use of AES in place of DES. AES has used a fixed block cipher with 3 different lengths of keys: 128 bits, 192 bits, 256 bits.
Based on key length, the number of rounds are decided: 128-bit keys require 10 rounds of encryption. 192-bit keys require 12 rounds of encryption. 256-bit keys require 14 rounds of encryption. The higher the key length, the stronger it is.
| Name | Block size | Key size |
| Advanced Encryption Standard (AES) | 128 | 128, 192, 256 |
AES Applications
Now a days AES is used in multiple applications like,
- Wi-Fi: Wireless uses AES to encrypt communication between network device so that intruder cannot hack the session by using session ID. Wi-fi uses only AES mode of encryption.
- Mobile Applications: Many social networking apps (like Snapchat and Facebook Messenger) use AES encryption to securely transfer data like photos and messages over the internet.
- VPNs (Virtual Private Networks) : VPN is used to connect with peer network/location over the tunnel in a secure way, for encryption method AES is applied to the tunnelled traffic as it is lightweight and fast.
AES is also used in password protection files, Programming Languages, compression tools.
AES Modes
There are 5 different modes through which AES performs encryption and decryption. Each mode has its own method to process blocks to execute encryption.
| Modes of AES | Name |
| ECB Mode | Electronic Code Book mode |
| CBC Mode | Cipher Block Chaining mode |
| CFB Mode | Cipher FeedBack mode |
| OFB Mode | Output FeedBack mode |
| CTR Mode | Counter mode |
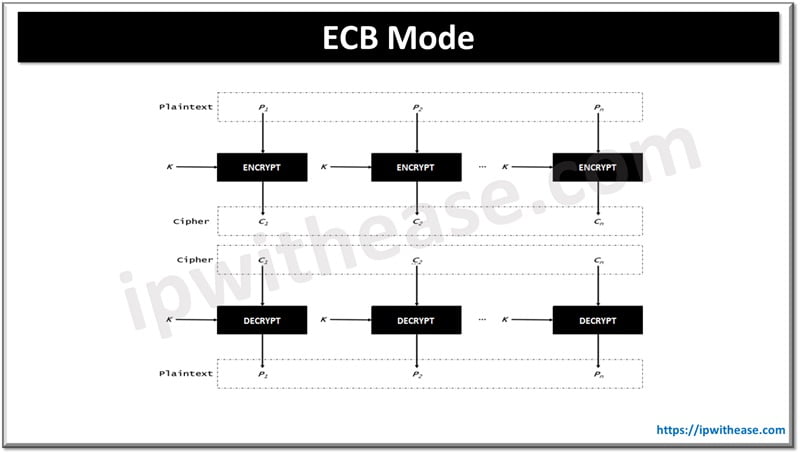
ECB Mode
Electronic Code Book (ECB) mode is the least secure and simplest mode.
- Each time the algorithm processes a 128-bit block, it encrypts the block using the chosen secret key which means if the algorithm encounters the same block multiple times, it will produce the same encrypted block.
- If a plain text block repeats itself, then cipher text also gives the same output of encrypted message (fig. 1.1)
- Each block is encrypted separately / independently to the other block
- If an enemy were prying/spoofing on the traffic session, they could simply build a “code book” of all the possible encrypted values.
- After enough blocks were captured, cryptanalytic techniques (the art or process of deciphering coded messages without being told the key.) could be used to decipher some of the blocks and break the encryption scheme.
- Hence ECB is not secure for complex networks where security of data is a prime requirement.
- It is used in the network where fast response is required and transfer small chunks of data at a time
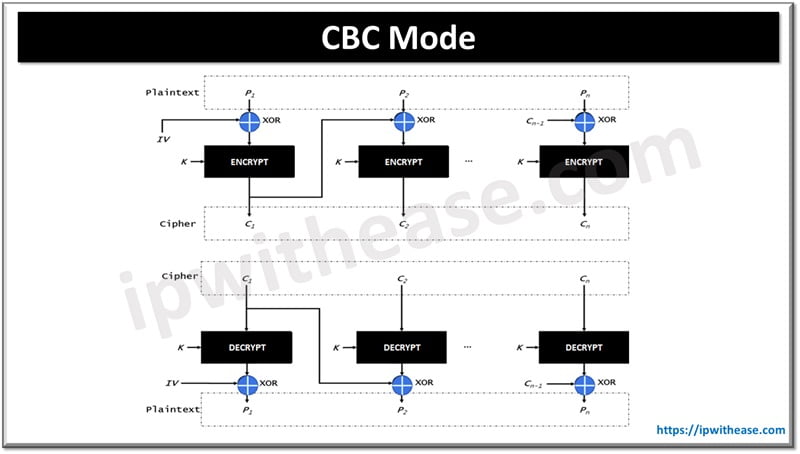
CBC Mode
Cipher Block Chaining Mode (CBC) Each block of unencrypted text is XORed with the block of ciphertext immediately preceding it before it is encrypted using the AES algorithm.
- The decryption process simply decrypts the ciphertext and reverses the XOR operation. CBC implements an IV (Initial Vector/any random number) and XORs it with the first block of the message, repeating the same operation every time.
- We can use the plaintext block XOR function with the IV.
- The IV must be sent to the receiver, perhaps the same key will be used throughout the process.
- In CBC mode, it will encrypt the output to the ciphertext block. In the next block, we will use the encryption output to XOR operation with a plaintext block until the last block.
- We will get the different cipher text output even if we put the same plain test as an input. However, there is a limitation of CBC mode, if a plaintext or ciphertext block is broken, it will affect all following blocks. Means if one block is corrupted then it will be impossible to decrypt any following cipher text and next block as well.
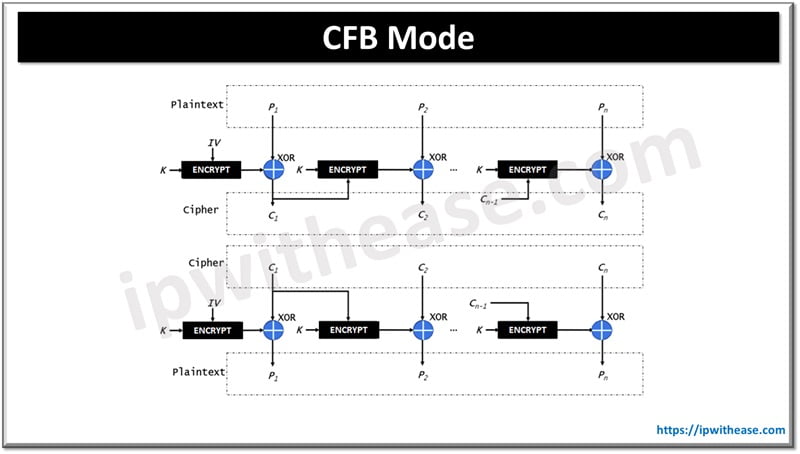
CFB Mode
Cipher Feedback (CFB) mode is the streaming cipher version of CBC.
- In other words, CFB works against text produced in real time.
- As the buffer becomes full, it is encrypted and then sent to the recipients. Then the system waits for the next buffer to be filled as the new data is generated before it is in turn encrypted and then transmitted.
- Other than the change from pre-existing data to real-time data, CFB operates in the same fashion as CBC. It uses an IV, and it uses chaining.
- Before performing XOR function with plaintext block CFB encrypts the IV (initial Vector/random number) to get Cipher text
- We will encrypt the encryption result to the plaintext by applying the XOR function.
- CFB mode doesn’t encrypt plaintext straight, it uses the ciphertext along with XOR function and plaintext to get the ciphertext output.
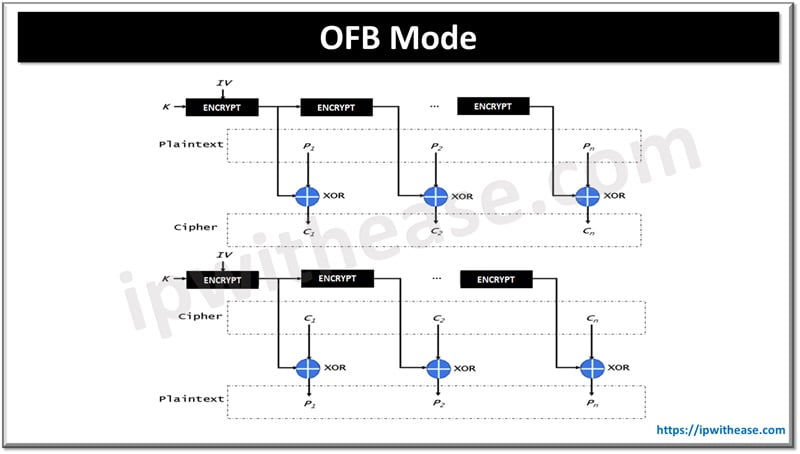
OFB Mode
Output Feedback Mode In output feedback (OFB) mode, AES executes a similar function to CFB. AES performs XOR functions in the plaintext with a seed value.
- Initialization Vector is used to generate seed value for the first encryption text.
- . Next seed value is derived from previous. OFB doesn’t follow the chaining function due to which transmission errors do not affect decryption of the coming block.
- In this mode, initially IV is encrypted. Then, XOR function will be performed on plain text to get Cipher text.
- Encryption performed on IV hence this is different from CFB. It cannot encrypt/decrypt the IV in parallel to key and cipher text creation. IV decryption is separate from other processes hence its decryption won’t be affected by broken block.
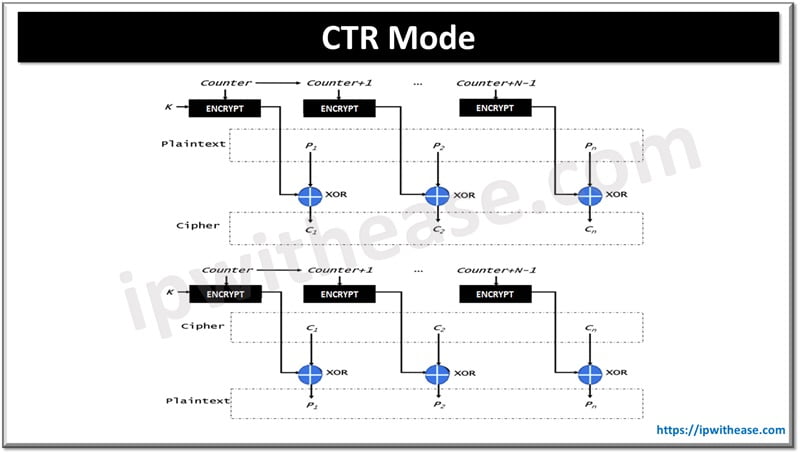
CTR Mode
Counter Mode AES when run in Counter (CTR) mode works in the same way that is used in CFB and OFB modes. It uses a stream cipher to convert plain text to cipher text.
- Counter mode uses a simple counter that increases after every operation.
- Generating the seed value for individually encryption/decryption operation from the outcomes of the previous seed values.
- XOR operation performed on the encrypted block by using a key.
- Plain text block is encrypted by key and counter, post encryption XOR operation is performed.
- All encrypted blocks use the same key through-out the process.
- CTR also does not propagate errors as OFB does.
Summary
| Modes of AES | Summary |
| ECB Mode | Simple and raw encryption Works for 16-byte data block Least secure among all other modes |
| CBC Mode | Uses IV to secure the block Not suitable for large data block as it has performance issue Wrong block affect all the succeeding blocks |
| CFB Mode | Acts as a stream cipher Accepts traffic in smaller units, 8-bits block Wrong block affect all the succeeding blocks Not often used in commercial applications |
| OFB Mode | No parallel computing Encrypt data in advance by using key and IV |
| CTR Mode | Designed for special data, like video, Voice over IP(VoIP) Block with errors can impact only current cipher block Fast as it uses parallel computing |
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj