Table of Contents
Enterprise networks are complex affairs , there is a mix of locations – branch offices, campus, remote workers, and they connect using LAN and WAN connections. There may be many devices on the physical layer including routers, switches, firewalls, wireless LAN controllers , Load balancers etc. There are multiple connections that exist at the logical layer as well such as VPNs, routing protocols , access lists, firewall rules etc.
Enterprises use a lot of hardware appliances such as new firewalls, new routers and WLC appliances. If you need to start a new service in enterprise networks, network administrators wish to have a solution where on a single click we can set up a new firewall or a WLC virtual appliance.
About Cisco SD Access Fabric
Today we look at Cisco SD Access which automates user and device policy for any application across the wireless and wired network via a single network fabric like SDN/cloud solutions work.
Components of Cisco SD Access
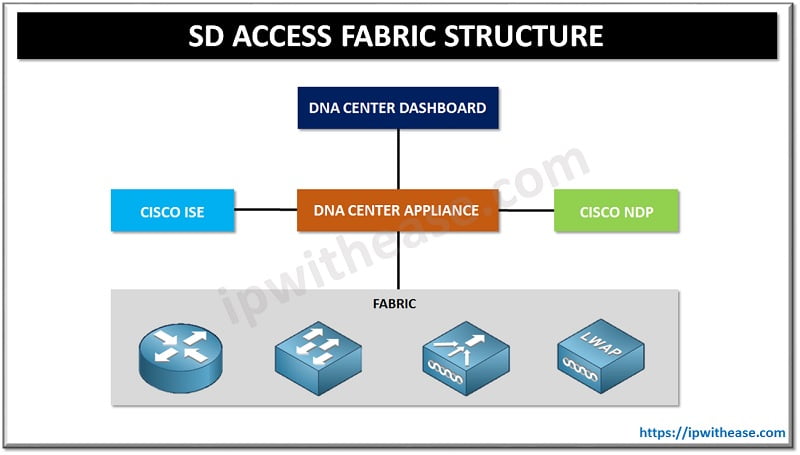
There are five main components of SD Access:
- Fabric
- DNA Center Appliance
- Identity Services Engine (ISE)
- Network Data Platform (NDP)
- DNA Center Dashboard
Fabric has all hardware components such as routers, switches, wireless LAN controllers, access points etc. These devices run IOS and IOS XE. SD Access uses an underlay for traffic forwarding traffic ; and provides a transport mechanism. Overlay network will be used for different sets of services as the overlay network is flexible and programmable. Fabric comprises of three key components namely LISP , VXLAN and CTS :
Control plane based on Locator Identity Separator Protocol (LISP)
It simplifies routing by removing destination details from the routing table and moving it to a centralized mapping system like DNS . The query is sent to a central LISP mapping system and asks for where the destination address is. LISP is used on data plane, but it can only tunnel L3 traffic. SD Access uses a modified version of VXLAN on the data plane and it supports L2 encapsulation.
On the policy plane Cisco TrustSec, Scalable Group Tags (SGT), and the SGT Exchange Protocol (SXP) are used. Similar network policy requirements of a shared group are added to endpoints who need it and SGT is added to the group. SGT is a tag that is separate from network address and network policies (QoS, PBR etc) can be attached to it.
DNA Center Appliance
It is Cisco’s SDN controller for organization networks and supports IOS/IOS XE devices.
DNA Center Dashboard
It provides overview of network health and drill down menus to quickly identify for quick identification and remediation of issues. It allows quick creation of physical maps and logical views of enterprise networks.
Identity Services Engine (ISE)
DNA Center and ISE dynamically map users and devices to scalable group tags or security group tags. Scalable groups resolve the shortcomings and all traffic is tagged based on automatic profiling of the user by access switch. The access switch determines the user id, device, location, time of access, and other data points. Tag is a numeric value which the administrator assigns manually to access switches and ISE automatically administers and transmits information to each supported device , exchanges certificates, and provision user access policies.
Network Data Platform (NDP)
Multipurpose , real time, network data collection and analytics engine used to do business analysis to explore business potential of network data.
Cisco SD Access Fabric features
- Designing network, applying policies, provision of network segments and users’ groups in fraction of time
- Enhanced security with separate users, lines of business, devices, and application traffic without redesigning of network
- Set policies for both wired and wireless networks with ease and flexibility
- Provides analytics and telemetry information to monitor and improve network
- Facilitates distributed networks and secure remote workforce with zero trust policies and dynamic segmentation of network based on business requirements
- Policy driven provisioning, remediation guidance and reduce time spent on managing network operations
- Building standard based network fabric which converts a high-level business policy into network configuration
Continue Reading:
SD-WAN Fabric Bring Up in Cisco Viptela
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj