Table of Contents
As workloads, databases and apps continue to migrate to the cloud, client-side attacks are growing in volume and severity. Threat actors are becoming more aggressive in exploiting vulnerabilities that tend to be overlooked amid the growing complexities of cloud and hybrid infrastructures. These weaknesses can even be found in popular applications that are widely used in cloud services. For example, in July 2024, Google itself suffered an embarrassing attack on its Chrome web browser, resulting in a leak of passwords for around 15 million users. Google said this was due to a change in product behavior that lacked proper feature protection. The issue bears some similarities with the CrowdStrike disruption, which took place the same month.
Because interacting with cloud-based tech generally involves less reliance on software installed on local devices, many people assume that client-side cyber attacks are less common. However, data management and client-side security are still critical in the cloud era. As we’ll soon see, client-side attacks are as potent and frequent as ever.
Client-Side Attacks vs. Client App Attacks
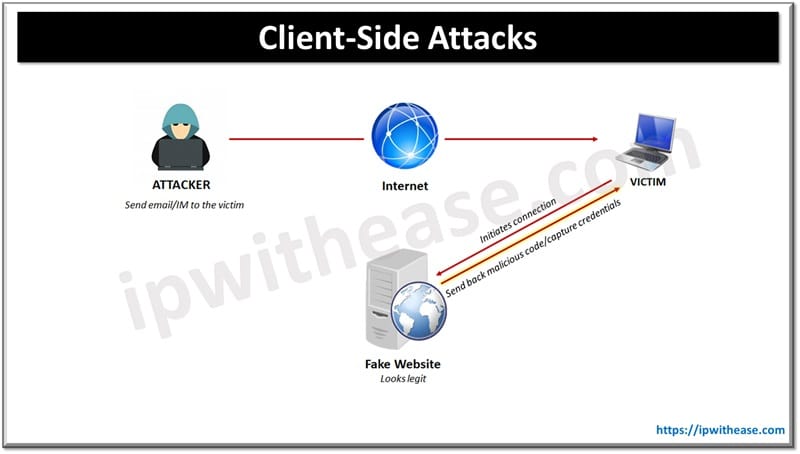
In order to understand and prevent client-side attacks, it’s important to first understand what makes them different from client app attacks. Client-side attacks refer to malicious or harmful actions aimed at the client-side components of a web application. These client-side components include the web browser used to access the web app, the device itself, the operating system, and other software that may interact with the web app.
In other words, it is inaccurate to associate the rise of cloud computing with the reduction of client-side attacks, because the latter target web apps, which have seen growing adoption in parallel with cloud computing. Client-side attacks do affect client apps, particularly web browsers. However, their main target is the web app being accessed through the client app.
With the increased adoption of cloud computing, organizations employ more web apps that entail the use of client-side components, especially web browsers. This creates a complexity, as explained below, that provides threat actors more opportunities to exploit security weaknesses As such, it is crucial to implement formidable client-side protection in addition to defending the web app itself.
The Complexities of Securing Web Apps
With most client apps, developers have greater control over the security of the software they release. They can implement defense mechanisms with minimal restrictions. With web applications, developers have to take into account frameworks, libraries, plugins, and other components needed to run the web app. This entails the development of large and complex codebases, which, in turn, creates more challenges in detecting and fixing vulnerabilities.
Web apps increase attack surfaces because they can be accessed through different web browsers and other applications. An online payment web app may be secure when accessed through the Safari browser, for example, but it may have security weaknesses when accessed through another browser, such as Chrome.
Development and security teams need to optimize app security with regard to the different web browsers used. In contrast, with client apps, the development and security teams only have to worry about optimizing the security of a single application.
Third-Party Dependencies
In addition to the complexities arising from the use of web applications, there are also challenges associated with third-party dependencies. Many web applications integrate third-party scripts or services for different purposes like analytics, the running of ads, and social media interactions.
This can create security risks, as attackers can compromise third-party services and introduce malicious scripts into the web browsers that run the web app. Compromised third-party components such as libraries, frameworks, and services are quite common. Nearly one-third of security breaches are attributed to third-party vectors.
It is important not to downplay this risk and ensure a thorough review of third-party dependencies especially in view of current practices when it comes to software supply chains. Misconfigurations, unexpected changes, and other problems in non-native software components contribute to the continued viability of client-side attacks.
Vulnerabilities in End-User Devices
There are billions of web-enabled devices in use worldwide. Many of these devices are cheaply produced products that have serious security weaknesses. They may have misconfiguration problems, outdated operating systems, and poor or nonexistent patching plans to address zero-day vulnerabilities.
These end-user devices are prone to various attacks, from malware infection to browser manipulation and phishing. Many enterprises forego security screening when acquiring new connected hardware to reduce acquisition costs. This means introducing poorly secured devices into their networks, contributing to the growing problem of client-side attacks.
IoT devices, in particular, are known to be easy targets for threat actors because it is difficult to secure them individually, and organizations have yet to build their proficiency in securing new kinds of devices.
Weak Security Practices
Another problem that greatly contributes to the continued rise of client-based attacks is the lack of sound security practices. Some enterprises have strong security policies on paper, but their implementation needs massive improvement. Some enterprises do not undertake input sanitization and validation for their web apps, exposing their apps to cross-site scripting and other attacks. Others do not take session and token management seriously, which makes it easy for cross-site request forgery and other attacks to successfully compromise apps. In addition, many fail to secure sensitive data in transit, allowing man-in-the-middle attacks to successfully intercept the information transmitted between servers and devices.
Also, many organizations are not well-versed in the ability of client-side attacks to bypass traditional server-side defenses. They deploy firewalls, intrusion detection systems, web application firewalls, and other solutions to protect their web apps, but they fail to facilitate or aid the implementation of security practices in the devices that access the web apps. They only focus on protecting their web apps and pay little to no attention to the cybersecurity practices of app users.
The security practices of end users, or their lack thereof, is a significant factor in the success of client-side attacks. Many end users fall victim to session hijacking, phishing, man-in-the-browser attacks, and other cyber threats that target web apps because of their lack or limited cybersecurity awareness.
In Conclusion
The age of cloud computing has introduced numerous benefits, but it also comes with a host of new security challenges. One of the most serious threats is client-side attacks, which rise with the popularity of cloud computing because they target web applications and affect client or locally installed apps, web browsers in particular. The threats are evolving, so it is crucial to put in the extra effort to address the complexities, the risks in third-party dependencies, end-user device vulnerabilities, and weak security practices.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.