Table of Contents
Most businesses become the victims of these cyber attacks because they are unaware of them. Are you wondering what is a Cyber Attack? Who does it? And why they do it? You’re in the right place. Today in this article, you will get all the information regarding them.

What is a Cyber Attack?
Cyber Attack is nothing but an assault launched by cybercriminals in an attempt to disable, expose, alter, destroy, steal or gain unauthorized to make unauthorized use of anything valuable to an organization or a person.
It is just a digital form of crime, where the cybercriminals use malicious code to crack the security and get into the user’s computers. There are many types of Cyber attacks; the attackers change the methods by rotation.
For example, in May 2017, Ransomware like WannaCry threatened the world. And in 2018 crypto miners’ attacks made the news. By 2020 ransomware is back to use now. Like this, the trend and methods of cyber attacks keep on changing.
Organizations, millionaires, and celebrities are targeted by these cybercriminals. But world nations assume the existence of Cyber terrorism and the chances of cyber warfare between nations.
Related – Zero Day Exploit
Why do they do it?
What are the motives and purpose of cybercriminals? This question is unanswered for years. The motives of many past attacks are still unknown. Here are the common reasons for the attacks.
In the case of Organizational Victims, the motives can be…
- To steal business financial details.
- To exploit the Customer’s financial details.
- To get Customers or users log in or other credentials
- To copy Customer databases and clients.
- To know the intellectual properties and business ideas.
Cyber-attacks against the businesses are mostly aimed at financial gains. In some cases, it can be done by competitors or users with personal motives.
When it comes to individuals the motives are hard to find. There can be personal hatred, financial motives, spying, and more. World Governments are also targeted by Cyber terrorists with different motives.
Common Types of Cyber Attacks
Here are some common types of Cyber Attacks you should be aware of:
DoS and DDoS attacks
DOS refers to the Denial of Service and DDoS is expanded as Distributed Denial of Service. The first DOS attack was recorded back in 1996. A group of people crowding the entry door of a shop and making it hard for the original customers is what happens in the DoS attacks.
Here the attackers use various methods of trafficking and make the network or the machine resources unavailable temporarily or for a certain period. Here there is no direct benefit for the attackers. But if the attacker is the competitor of the victim then there is a huge return.
Related – What is DOS and DDOS Attack?
Man-in-the-middle attack
This has different names like the monster-in-the-middle, machine-in-the-middle, monkey-in-the-middle, and shortly called MITM attacks. Here the attacker secretly enters the communication between the two parties who believe that they are directly connected. The attacker can intercept and even alter the private conversation between the two parties.
The attacker can intercept the communication between the user and server, two individuals, employees, and employers and steal much valuable information and create miscommunication between them. These attacks are made in different ways – Session hijacking, IP spoofing, etc…
Phishing attacks
Phishing is the method used by cybercriminals to attain Personal or confidential data through deceptive emails and websites. Here the attackers disguise themselves as valid and legitimate organizations. They send fake emails and invitations to users in a convincing way, luring the users to click the malicious sites in the link.
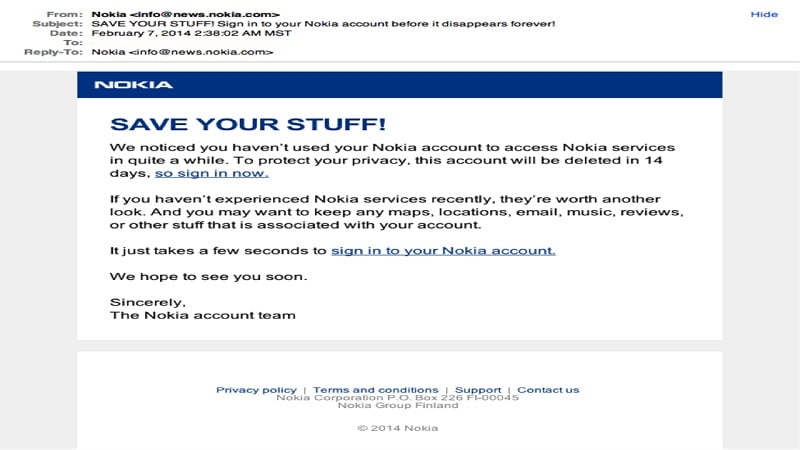
In this way, they make the users download the malware or malicious applications created by them or exploit confidential data or information from them.
SQL Injection
With the advancement of database-driven websites and web applications, SQL Injection becomes a common threat. Here the attackers enter a malicious SQL query in the field of Input to find if there any SQL injection vulnerability.
If so, then he performs the SQL attacks, thus altering, copying, deleting, and accessing the data in the database. This type of attack various consequences like Identity spoofing, credentials theft, etc…
Malware Attack
Malware is malicious software that is installed without the consent of the users and affects the working of the computer. The malicious software is designed with the motive to attack or damage the user’s computer.
There are different types of Malware like Ransomware, Trojan horse, etc…Mostly Malware attacks are done as follow up for the above-said attacks.
Conclusion
It’s true; we cannot fight the unknown enemy. But still, people fall for the existing or known Cyber threats because they are unaware of them. So if you are planning your future in this digital world then it is your responsibility to aware of the new and existing Cyber attacks and Threats, and one best way to do it is by enrolling in the best Cyber Security Course that can help you enhance your cyber security skills. Always prevention is better than cure.
Continue Reading:
What to Do if You’re Affected by Data Breach?
Network Vulnerabilities and the OSI Model
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.