Table of Contents
The world of cybersecurity is always in flux – the relevant technologies are always evolving, so the types of threats you might encounter are always changing. If you’re in a business or any other type of organization that operates online, you’re likely going to want to know what you can do to stay one step ahead.
Fortunately, there is plenty of knowledge being shared by those in your position, which can help you to carve out the most effective path ahead – it just takes understanding the key technological players in this emergent landscape.
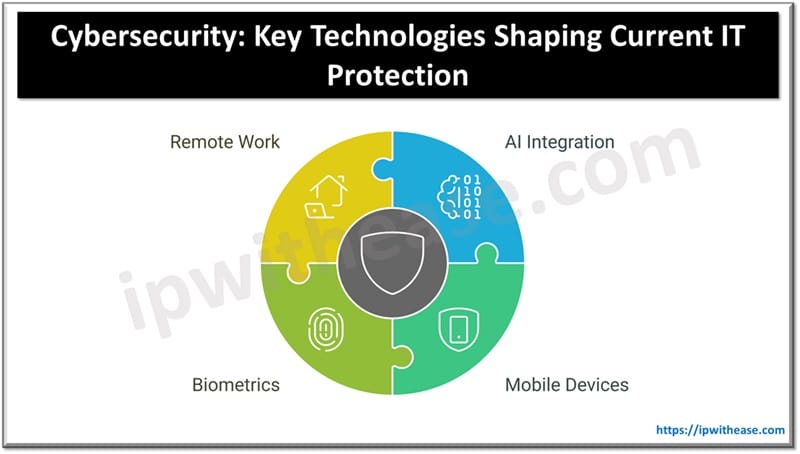
What Role Does AI Play?
The question on many people’s minds will undoubtedly revolve around AI, especially when this topic comes up. This is because of how unavoidable the technology has become in recent times. Indeed, it has proven to be a major player in cybersecurity. However, understanding how it’s utilized can help you make the most of what it offers rather than using it too broadly or too generally to be effective. Due to the role that AI tools play in analyzing large amounts of data within a short span of time, they’ve become essential in detecting and responding to threats within a reasonable timeframe.
Understanding how these kinds of tools have shifted from being a helpful addition to something more foundational takes a more thorough understanding of the modern cyber security priorities. In business, this might mean putting more resources here than you currently allow, including your time and research.
Mobile Devices and Biometrics
It’s important to recognize that the presence of new technologies in the world of security isn’t just about allowing you more options to defend yourself – they can also create whole new vulnerabilities and considerations. The prevalence of mobile devices is a good example; with an estimated 90% of the world carrying smartphones, it is more than likely that this would be an area targeted by cyber attackers.
However, this also opens up new avenues of protection. While biometrics were used before, they became popular in smartphone technology. Their widespread nature now means that each person has a much more tailored security method for their device, such as two-point verification security features, and facial recognition. These aren’t foolproof, though, and the presence of false positives and false negatives speaks to that.
Remote Work Environments
Culture and societal norms change over time, and in many ways, that’s what has happened with the rise of remote working. For many people and businesses, it offers employees a way of striking a more comfortable work/life balance – whether as part of their working model or just an aspect of something hybrid. However, being outside of a bespoke office environment naturally means that there will be new security considerations for the business. Weighing this against the benefits of remote working will result in a different outcome for every brand. Still, it also means that more consideration is going towards patching up vulnerabilities that might emerge through working from home.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.