Table of Contents
Introduction to NAT
NAT converts a private address to be stamped with a public address, thus allowing that internal host to communicate across the Internet. NAT also translates multiple privately-addressed IPs to a single public address IP, which conserves the public address space. Below are some types of NAT:
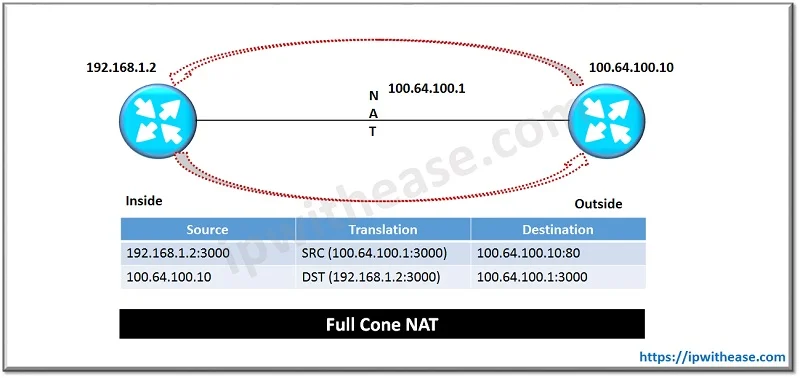
Full Cone NAT
The first type of NAT construct is full cone NAT (sometimes referred to as either one to one NAT or static NAT). Full cone NAT is the only type of NAT where the address and port are always open. All external hosts initiating connections to this port are allowed and translated to the internal host. Multiple full cone NATs configured using the same public IP, but the ports that are being translated internally must be different per internal host. Additionally, the internal and external ports don’t need to match.
Symmetric NAT
The second type of NAT is symmetric NAT (also referred to as dynamic PAT). Symmetric NAT has the advantage of allowing a large number of hosts behind a single IP address. Symmetric NAT is common in deployments where a number of users need access to the Internet, and the administrator does not want to consume a unique IP per user. With symmetric NAT, the original source IP will be translated to the outside IP address, and the source port will be translated to another port. This allows a theoretical limit of up to 63,335 hosts behind a single public IP.
With symmetric NAT, each internally initiated conversation to an outside host will be mapped to a NAT translation table. This is a key difference with full cone NAT. Because the mapping is created only when traffic is initiated from an internal host, external hosts cannot initiate connections to the internal host. This mapping is dynamic and will expire eventually, if there is no traffic matching that mapping entry.
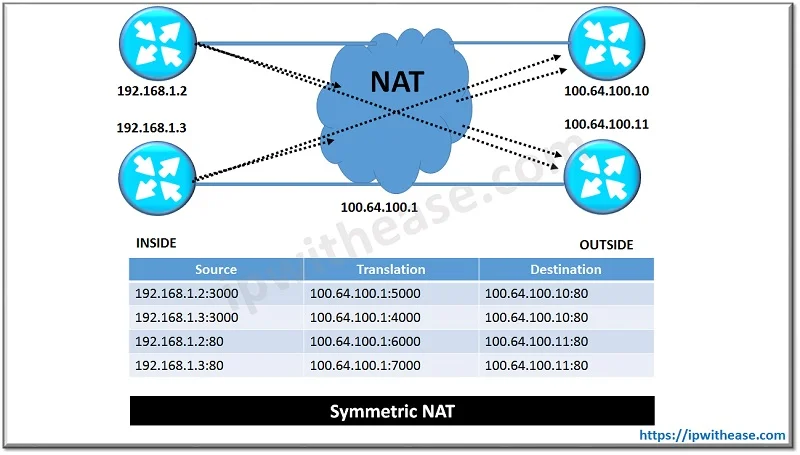
Address Restricted Cone NAT
The remaining types of NAT are variations of full cone and symmetric NAT. They build off the concepts already introduced but add some additional filtering to the IPs and ports in use. The first option is address restricted cone NAT. This type of NAT works similarly to full cone NAT, except it only allows external hosts to communicate to the internal host if that host has communicated with the external host before on any port. The external host can then initiate a connection with the internal host on any ports that have been NAT’ed.
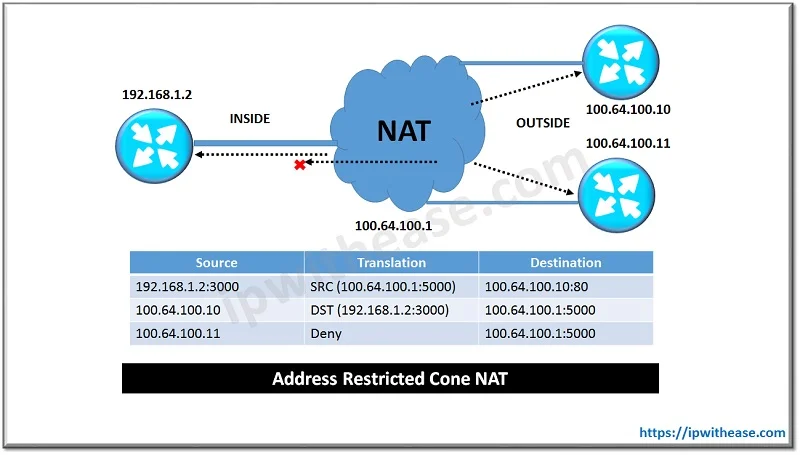
Port Restricted Cone NAT
The final type of NAT construct is port restricted cone NAT. This type of NAT is similar to address restricted cone NAT, except it uses the port number as a filter. When an internal host connects to a remote system, it connects to a destination port. This port is then added to the NAT filter, and if any external host wants to communicate with the internal host, it must have the same source port that the internal host used as its destination port. If any external host uses a different source port, the traffic will be denied. If another external host uses the same source port, it will be allowed.
NAT in SD-WAN
With the Cisco SD-WAN solution, there are certain types of NAT that work and some that have restrictions. vBond controller operates on the orchestration plane and is the glue of the fabric in regard to how NAT is handled. WAN Edge routers always reach out to the vBond controller first to learn about the rest of the components in the fabric. During this process, they also learn if they are behind a NAT device or not. When the WAN Edge initially connects to the vBond, it inserts its real IP address into the exchange.
When this packet passes through the NAT device, the source IP and possibly the source port are translated. Since the message still contains the WAN Edge’s real IP and port, the vBond is able to send a message back to the WAN Edge notifying it that it is behind a NAT (since the real IP differs from the NAT’ed IP received in the exchange). The WAN Edge will then insert this information into its OMP TLOC route and send this to the vSmart controller. If these values are different, then the WAN Edge is behind a NAT device. This information will then be reflected to all WAN Edges in the overlay, and they will use this information to build their data plane.
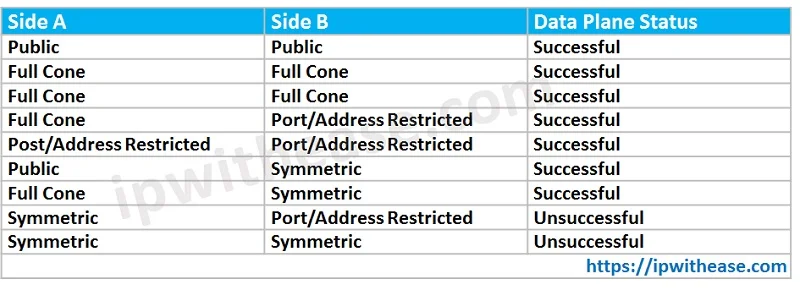
NAT Types and Data Plane Status
Continue Reading:
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj