Table of Contents
These days many new terminologies are introduced and it becomes necessary to know about these terminologies and understand them well. Microsegmentation divides networks into isolated segments to limit lateral movement. Whereas, Zero Trust is a security model that assumes no implicit trust and verifies every access request.
In this blog, we are introducing Microsegmentation and Zero trust terms. We will discuss their functionality and how they differ from each other.
Let’s start with Microsegmentation first.
What is Microsegmentation?
Microsegmentation is a technique of network security that helps security architects to divide the data center reasonably in different security segments down to the individual level of workload and then we define security controls with reference to each workload.
It is the micro-segmentation that enables the IT industry to deploy different security policies inside the data center with the help of network virtualization technology.
Related – IDS vs IPS – Difference in Network Security
There is no need to install multiple firewalls in this method. Micro segmentation is also used to protect the virtual machine (VM) in the enterprise network which is policy-driven.
As the security policies in micro-segmentation are applied to individual networks, it acts as resistance to attack.
Micro-segmentation uses network virtualization technology for the creation of granular secured zones in all the data centres & cloud deployments, and isolates the individual workload and makes them secure.
How Does Micro-Segmentation Help in Networking? Network Microsegmentation
Micro-segmentation architecture helps networks by creating “demilitarized zones” for security purposes within the single data centers & multiple data centers.
In this, fine-grained security policies are tied to individual workloads and it limits the attacker’s ability to move from the data center even if it infiltrates the perimeter defences.
It simply means that it can easily eliminates server to server threats in the data center and securely isolates the networks from each other and reduces the chances of the total attack surface of the network.
When you compare different micro-segmentation vendors, always keep one thing in mind – to look for a vendor which uses the advanced technology of Microsegmentation and provides decent solutions.
It should also have a feature of flexible policy creation and capabilities like breach detection. It will make the implementation process easy and helps you in a quick win from starting.
During the implementation process, it is important to choose a future proof approach so that it can easily merge with the ongoing models like containers in addition to virtual machines, bare-metal servers, and cloud instances.
Now we will move to another terminology that is Zero trust?
What is Zero Trust?
Zero Trust is a strategic initiative that helps in preventing successful data breaching by removing the concept of trust from the network architecture of an organization. It is based on the principle of “never trust, always verify”.
It is designed for the protection of the modern digital environment from leveraging network segmentation, Layer 7 threat prevention, prevention of lateral movement and simplifying user access control of granular.
The concept of zero trusts was introduced by John Kindervag when he was a vice president & principal analyst for the Forrester Research which is based on the realization that traditional methods of security models are operated on the outdated assumptions which say inside every organization’s network there is trust.
Under the model of Zero Trust, it is believed that the user’s identity is not at all compromised and all the users act responsibly & can be trusted. This model says that trust is vulnerable.
Once the users on the network including threat actors & malicious insiders are allowed to move freely and can access the data whatever they want. There is no limit. Mind one thing that infiltration of the attack is not often the targeted location.
Always remember one thing that this model is not based on making a trusted system rather it works on eliminating the trust. Most of the data breach is caused due to the misuse of privileged credentials.
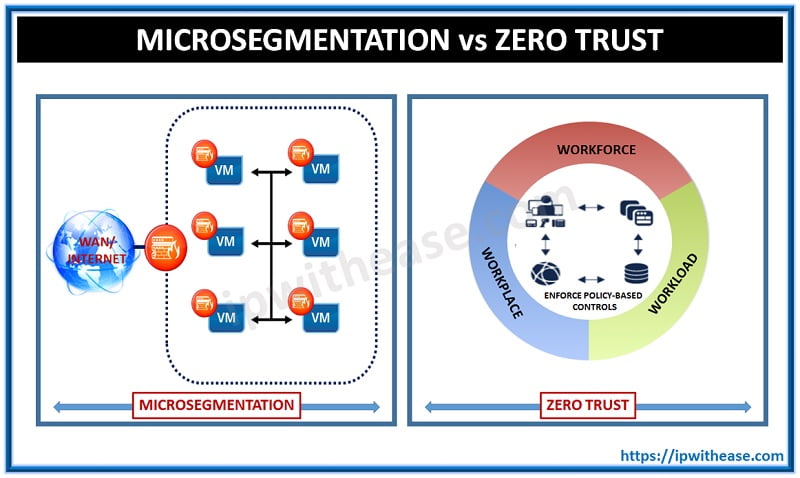
Comparison: Microsegmentation vs Zero Trust
Now that we have gone through the basics of Microsegmentation and Zero trust, below table helps us understand how both differ in comparison to each other.
Key Differences between Zero Trust and Microsegmentation:
| Parameter | Microsegmentation | Zero Trust |
|---|---|---|
| Definition | Network security technique that segments networks into smaller zones. | Security model assuming no implicit trust; always verify. |
| Primary Goal | Limit lateral movement within the network. | Eliminate implicit trust and continuously authenticate users/devices. |
| Scope | Focused on internal network segmentation. | Broad security model encompassing users, devices, networks, apps, etc. |
| Granularity | Fine-grained Per application, workload, or process. | Holistic Applies to all access and identity points. |
| Trust Model | Trust within microsegments, control access between them. | “Never trust, always verify”—no trusted zones. |
| Authentication | Typically network-level controls like ACLs or firewalls. | Identity-centric Enforces multi-factor auth, policy-based access |
| Enforcement Points | Firewalls, hypervisors, or SDN at segment boundaries. | Everywhere – devices, users, apps, endpoints, etc. |
| Common Technologies | NSX, Illumio, Cisco Tetration, etc. | Zscaler, Okta, Microsoft Zero Trust solutions, etc. |
| Use Case | Protecting East-West traffic in data centers. | Secure remote work, cloud access, BYOD, internal threats. |
| Implementation Complexity | Moderate to high Requires network visibility and planning. | High Involves org-wide identity, policy, and infrastructure changes. |
| Best Used With | Zero Trust (as a component). | Can incorporate microsegmentation as a control. |
Download the comparison table: Microsegmentation vs zero trust
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj