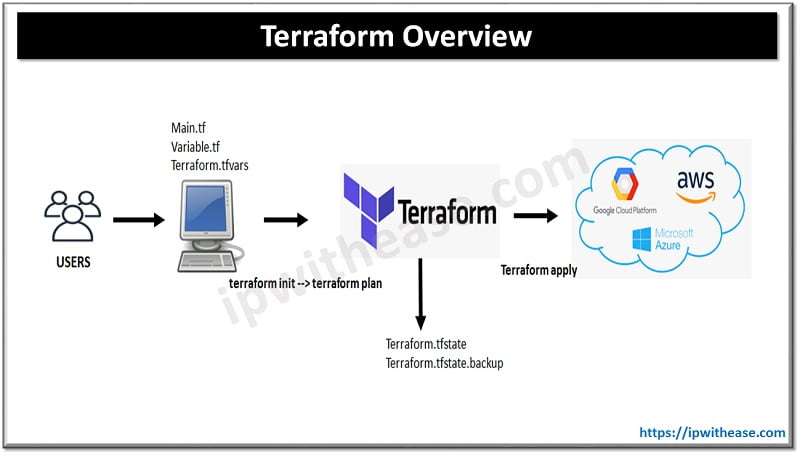
Table of Contents
Deployment of MX Appliance is quite easy to provision for the first time without any first time configuration required. First step, connect the appliance to the Internet and access it from the Meraki Dashboard. When an appliance is connected to the internet, assign the subnet range and DHCP settings from the Dashboard. Also assign static IP addresses to devices such as APs and printers within the branches.
MX Deployment: LAN & WAN
Let’s get started configuring appliances with LAN and WAN settings.
- Connect the appliance to the DSL/cable modem through the modem’s Ethernet output.
- Set MX series WAN IP address and DNS settings, with the following 2 options
- Appliance will negotiate with local ISP to get IP via dynamic assignment.
- Alternatively, if ISP has provided you with a static IP address and DNS settings, enter them manually.
- Login to Dashboard account at https://dashboard.meraki.com.
- To verify that the device is accessible in the Dashboard, go to Security & SD-WAN then Monitor and then Appliance status.
- Assign a subnet for the branch.
- Go to Security & SD-WAN and Configure and Addressing & VLANs.
- Choose whether want a Single LAN or multiple VLANS under Routing > LAN Setting.
- Assign subnet range for VLAN. For example, if subnet is from 192.168.11.1 to 192.168.11.254, you’ll need to enter the following information in the Subnet field: 192.168.11.0/24.
- Assign VLAN Interface IP. This sets the IP address of the MX device on this LAN.
- Choose your DHCP option.
- For locations with a third-party DHCP server.
- Go to Security & SD-WAN and Configure then DHCP.
- Select do not respond to DHCP requests.
- For locations with DHCP service.
- Open Security & SD-WAN and Configure and DHCP.
- Select Run a DHCP server.
- For locations with a third-party DHCP server.
- Connect a laptop to one of the LAN ports of the MX. Be assured that there is uninterrupted Internet access and that you are getting an IP address within the subnet field you have assigned.
Site-to-site VPN
All VPN peer’s device needs following prerequisite should be matched.
- Pre shared key (PSK) or certificate.
- Public IP addresses of other peer devices and NATed subnets behind the peer devices.
- Phase1 and Phase2 parameters should be matching with other settings.
When above conditions matched, peer devices establish the VPN tunnel through the following:
- Connecting to each other directly, jointly negotiating VPN phase1 and phase2 offers.
Related: Site to Site VPN vs Remote Access VPN
Meraki site-to-site VPN is different
Above steps are manual and therefore chance of human error. MX devices are very different; they are all connected to the Dashboard and automatically provision VPN based on information provided.
- MX device advertising its public IP address and its NATed subnets to the Dashboard.
- When VPN is enabled, VPN peers automatically reach out to each other and initiate an IPSec VPN connection.
- The Dashboard assigns a unique pre-shared key for all participating VPN peers.
- Finally, the Dashboard sends a globally adjusted route map to each device, so that they all know how to reach each other’s NATed subnets.
Setting up site-to-site VPN with Meraki MX devices
Creating a site-to-site VPN tunnel to the Hub from the branch.
- Open Security & SD-WAN and Configure then Site-to-site VPN.
- Select Hub from the VPN type options.
- Select ‘Enabled‘ from drop down under VPN Mode for the local subnets that should be available on the VPN.
- Select Automatic from the NAT traversal options.
MX Warm Spare – High-Availability Pair
For configuration of warm spare failover (HA), Go to the Security & SD-WAN and Monitor Then Appliance status and select Configure warm spare near the upper-left side of the page, below the device name. In the window that appears, Choose Enabled. Enter the serial number of the secondary MX appliance and select the desired WAN1 or WAN2, then select Update. HA to provide redundancy for internet connectivity and appliance services when an MX security appliance is being used as a routed gateway.
WAN Virtual IPs
Virtual IP address is assigned to both the primary and warm spare appliance. In and Out traffic uses this address to maintain the same IP address during a failover and reduce disruption. The virtual IPs are configured on the Security & SD-WAN and Monitor then Appliance status page, under the Spare section in the upper-left corner of the page. If two WAN uplinks are configured, a VIP can be configured. VIP must be in the same subnet as the IP addresses of both MX appliances for the uplink it is configured for, and it must be unique.
Continue Reading:
16 Benefits of Cisco Meraki as a Cloud-Managed Networking Solution
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj