Table of Contents
Businesses are constantly moving more applications and services online and because of that cloud security is one of the top priorities for them. While security threats are a growing concern it is hard to manage who can access what resources in a cloud environment. If you are wondering what is the role of an Open Policy Agent (OPA), this is where it comes in.
To explain it in the simplest way, OPA is an open-source policy engine that serves to help organizations enforce access control and security rules on different platforms, including Kubernetes, APIs, and cloud infrastructure.
But, to learn more about how OPA enhances cloud security and access control, you should read the following explanations.
Why Cloud Security Needs Strong Access Control
To understand why cloud security needs strong access control, you need to know what are the struggles with traditional access control models in a cloud environment. The main struggles are:
- They are too rigid – The problem happens because new users, services, and applications are constantly added, and hardcoded rules don’t scale well in that case.
- They lack flexibility – When you need to manage security policies in different systems manually it takes a lot to be handled and errors can happen.
- They don’t provide centralized control – Security rules can get scattered on multiple tools and that can lead to inconsistencies.
Opposite to traditional access control models, OPA policy manages security in a centralized and scalable way, and that is the main reason why more companies are turning to OPA policy.
How OPA Improves Cloud Security
OPA is giving options and ways to define, enforce, and update security policies. Here are some key ways how OPA enhances cloud security:
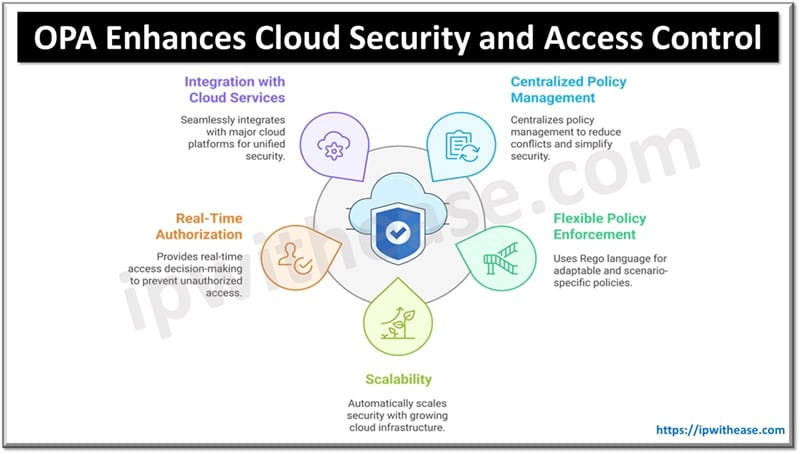
1. Centralized Policy Management
OPA doesn’t handle security rules on multiple systems. Instead, OPA allows organizations to create and manage policies in one place, and it has big benefits. It reduces the risk of conflicting policies. Also, this approach makes security easier to manage.
2. Flexible Policy Enforcement
Thanks to OPA, businesses can now define security rules in a simple, easy-to-understand language called Rego. This is one of the great solutions that allows teams to create policies that can adapt to different scenarios and don’t require changes to the underlying applications.
3. Scalability for Growing Cloud Environments
Businesses scale their cloud infrastructure but the main issue is that security policies need to grow with them too. Well, that’s where OPA is again excelling. Adding new users, microservices, or APIs; nothing is a problem with OPA because it can apply the right security controls automatically.
4. Real-Time Authorization
OPA can check every access request before being granted because OPA makes decisions in real time based on defined security policies. This reduces the risk of unauthorized access.
5. Integration with Popular Cloud Services
Although it is already impressive, there is more when it comes to OPA’s amazing benefits. OPA works with major cloud providers from AWS, Google Cloud, and Azure, to Kubernetes, service meshes, and API gateways. This makes it so much easier to enforce security policies across different environments.
How Businesses Use OPA for Cloud Security
Here are some common cases of how organizations usually use OPA to secure their cloud environment in different ways:
| Use Case | How OPA Helps |
| Kubernetes Security | Keeps under control which users and services can deploy workloads. |
| API Authorization | Only authorized users can access sensitive APIs and OPA also controls that. |
| Infrastructure Compliance | Helps in the usage of regulatory security policies automatically. |
| Microservices Access Control | Defines rules for service-to-service communication. |
Steps in Implementing OPA in Cloud Security
Implementation of OPA has extended areas of improvement in security, however, businesses can narrow the scope of implementation into:
- Define Security Policies – This involves stating rules that need enforcement, for example, access levels of users and API security.
- Deploy OPA – This involves the inclusion of OPA within cloud services and applications so that policies can be enforced.
- Test and Monitor Policies – OPA is continuously checking if security rules are working correctly. If a problem occurs, it will be adjusted immediately.
- Write Policy in Rego – OPA’s Rego language is for flexible security rules.
- Test and Monitor Policies- Security rules need to be continually tested if they are active and altered as required.
- Automate Policy Updates – CI/CD data pipelines that ensure real-time policy updates and enforcement.
Conclusion
Strong access control is what cloud security demands, and through OPA policies, organizations can definitely have a scalable way of embedding rules beyond heterogeneous platforms. Centralized management and time authorization coupled with easy integration with cloud services ensure that OPA further strengthens or widens a business’s flexibility in handling access policies.
Implementing OPA translates to a possible security improvement of an organization’s cloud infrastructure and overall minimal security risks. It also assures conformity to the industry standards.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.