F5 BIG IP platform has functionalities and features which tend to deliver higher performance and at the same time foster improved security. One such intelligent quality provided by these Application Delivery Devices is the Full-Proxy feature.Full-Proxy mode is an enhancement to packed based working of traditional Routers and Firewalls. Let’s further understand how Packet based design and Full Proxy differ from each other –
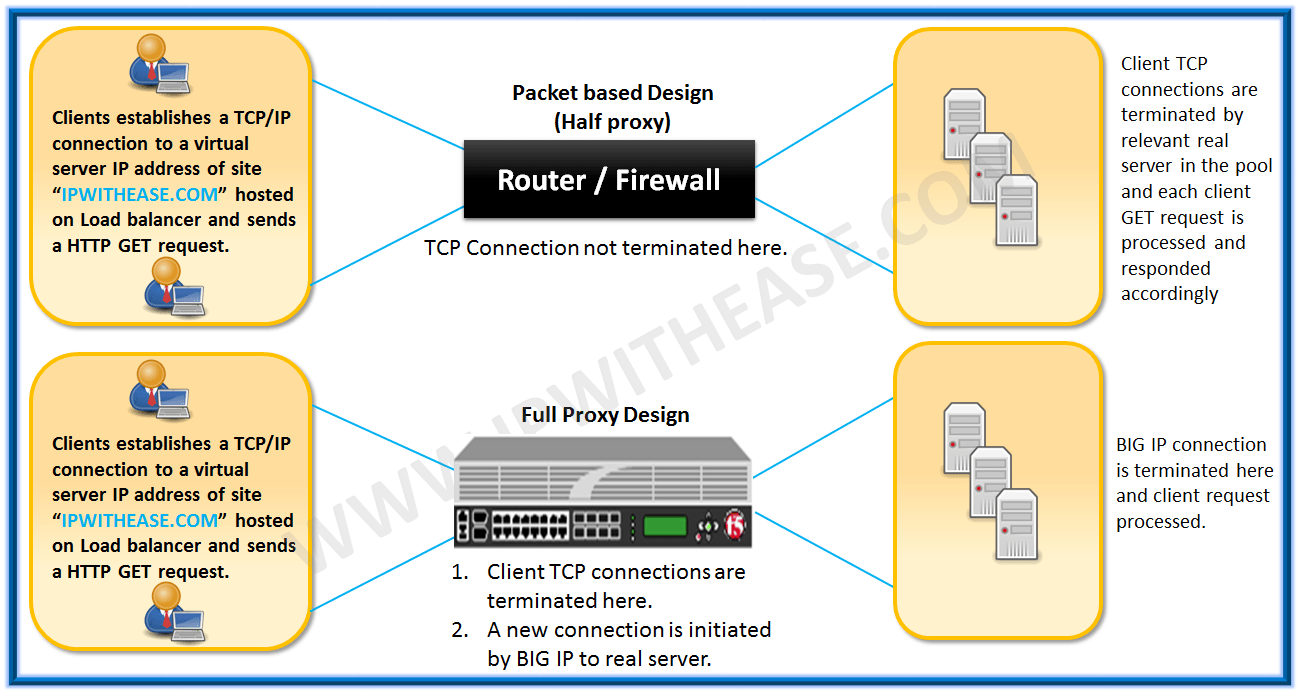
Packet based solution is nothing but similar to our Router/Firewall which simply are located in middle of communication stream and forward packet to destination. Packet based designs have a single TCP/IP connection between client and server. With the help of Access-list or Firewall Rule one can block or allow traffic, which may not be the best of designs since we don’t have much view on the traffic passing through the device or can’t control the traffic traversing through the device.
Let’s see how more intelligence is brought with introduction of F5 BigIP platforms. Full Proxy based design goes beyond the magnitude of just understating the traffic flow traversing through the device. Instead F5 box functions as endpoint and originator of protocols. With full proxy mode, we have 2 separate TCP/IP connections which means direct connection to server from client is not there and however, we have BIGIP in middle of client and server. Now we have 1* TCP/IP connection from Client to F5/BIG-IP (full proxy device) and 1* connection from F5/BIG-IP (full proxy device) to server, this means now you have better control on the traffic which is passing over the F5/BIG-IP. The proxy performs to role ie Firstly it acts as server to the client and secondly acts as client to the real server. Furthermore, each can have independent parameters applied, such as idle timeouts, buffers, MTU, window size and so on.
Here are some benefits of using full proxy design: –
- Inspection, manipulation and modification of application layer data
- iRules (working above OSI Model layer four)
- Advanced Persistence methods
- SSL offload
- TCP Optimizations
- HTTP Compression, Caching and Pipelining
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj