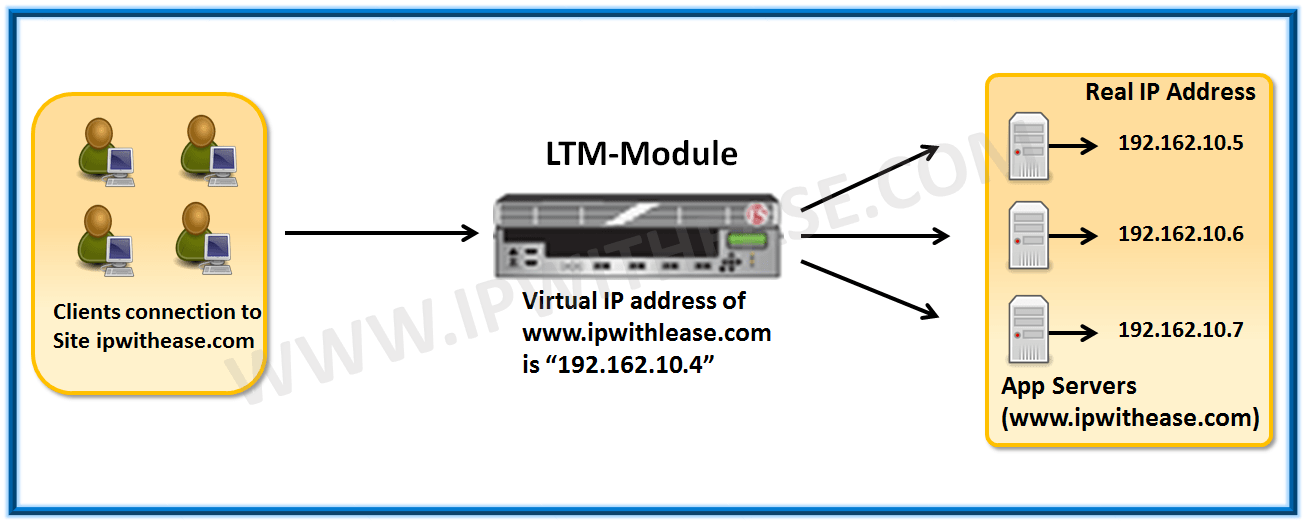
LTM is abbreviation for Local Traffic Manager used to manage the traffic which is designated for the servers (application) and initiated by multiple clients.
LTM supports Client to Server communication by providing redundancy, reliability and improved performance. To be concise, an LTM balances the load across all the bunch of physical servers where the applications are hosted.
Related – F5 Load Balancer Interview Questions
It decreases the burden on the servers and improves the overall performance of the application. Infact, the Full Proxy based design of LTM provides a great deal of control on application traffic, even further, we can manage, inspect and report application traffic which is entering and exiting from the network.
Let’s take an example to understand LTM better –
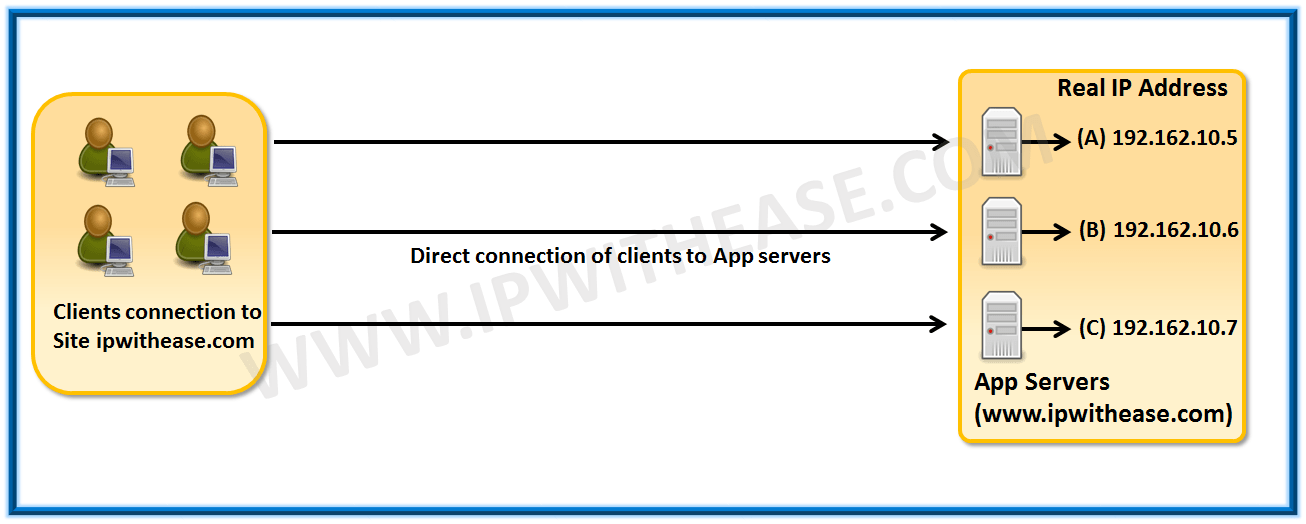
In the example, all client requests directly go to application destination servers, which may cause destination application servers to quickly get overloaded. Maybe server A is addressing to more resource requests and utilizing 90% of resources and other servers are handling lesser requests than server A (i.e. 30% or 40%). Any client request landing on server A will definitely suffer slowness .At the same time, Servers B and C have enough free resources which are not judiciously utilized. The typical system has no mechanism to find out efficient distribution of requests to servers . To address this challenge, BIG-IP LTM is the answer – It sits between clients and the application servers and performs all multiple functions such as
- Load balancing
- Traffic acceleration
- Access control to application security and protect all servers from attack individually.
The above shared points tend to provide end users better experience and improved application security .
Here are some Key features of LTM module: –
- SSL offloading – SSL connection from client to server terminated on BIG-IP LTM instead of server, BIG-IP will initiate simple TCP/IP connections since SSL connections consume CPU. This helps to reduce the CPU utilization of the servers.
- SSL certificate based authentication and termination – Any https request coming from client are authenticated on BIG-IP LTM, if certificate matches then request will be forwarded to webserver if not then dropped.
- Intercept and redirect incoming network traffic – URL redirection from ipwithease to ipwithease/LTM.
- Compression and optimization on http traffic and Packet filter for network access control
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj