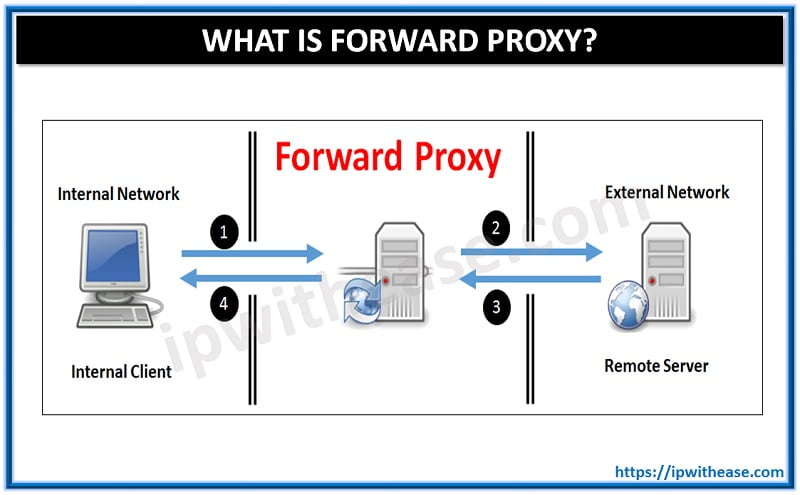
Privacy Enhancing Technology
With the rise of digital healthcare, protecting patient data has become more critical.
Fortunately, we have privacy enhancing technologies (PETs) to help us protect our data online and offline.
This blog post will look at PETs and how they can provide data solutions by protecting your data. We’ll also explore some of the best privacy enhancing technologies available today and how you can make sure your data is protected with PETs.
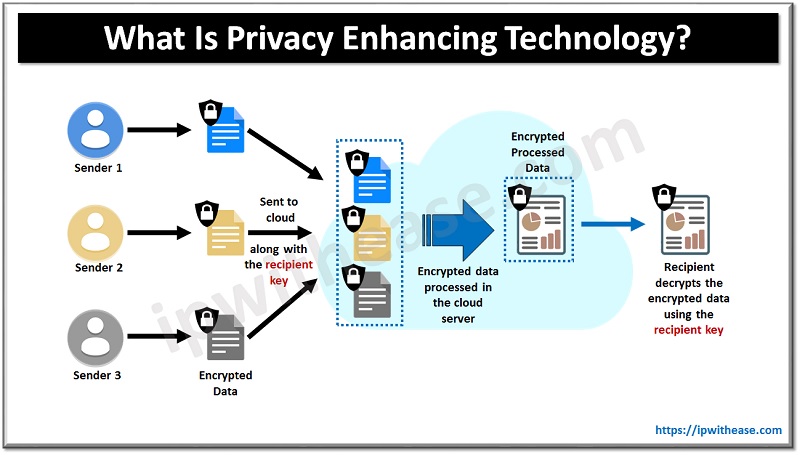
What is Privacy Enhancing technology and how does it work?
Privacy enhancing technology (PET) is a term used to describe any tool, software, or hardware that helps protect user privacy. PETs use encryption algorithms and other techniques to protect against unauthorized access to sensitive data, including personal information or health records. For example, when you input your credit card number into an online store, you use a form of PET called end-to-end encryption that protects your credit card information from being stolen.
Why do we need Privacy Enhancing technology in healthcare?
As healthcare moves increasingly online, it becomes more critical to ensure that patient data remains private and secure. This is where PETs come in; they allow us to securely store and share sensitive medical information without compromising patient confidentiality. By using PETs in healthcare settings, we can ensure that patient data remains secure while allowing doctors to access the information they need to provide effective treatment.
How can Privacy Enhancing technology provide data solutions and protect you?
PETs use a variety of strategies as data solutions for protecting data both online and offline. For example, many PETs employ encryption algorithms that scramble the data so it cannot be read by anyone who does not have access to the key used for unlocking it.
Other privacy enhancing data solutions include firewalls that prevent unauthorized users from accessing sensitive systems; authentication tools that verify user identities before granting access; and digital signatures, which authenticate documents via cryptographic methods such as hashing algorithms or public key cryptography. All these technologies work together to provide comprehensive protection for your online and offline data.
What are some of the best Privacy Enhancing technologies available today?
Many privacy enhancing technologies are available today, from simple software solutions to complex hardware systems explicitly designed to protect large amounts of sensitive information. Some popular examples include Secure Sockets Layer (SSL), Virtual Private Networks (VPN), two-factor authentication (2FA) systems such as Google Authenticator or Authy, Zero Knowledge Proof protocols like Zcash, Homomorphic Encryption (HE) systems like Microsoft SEAL library, as well as distributed ledger technology such as Blockchain networks like Ethereum or Hyperledger Fabric.
Investing In Privacy Enhancing Technology: In Closing
Protecting patient confidentiality is essential for providing effective healthcare services in the modern world; however, doing so requires using powerful tools and data solutions such as privacy enhancing technologies (PET). This blog post explored PETs and how they work by providing secure storage and sharing options for sensitive medical information.
We also looked at some of the best privacy enhancing technologies available today and how they can help protect your online and offline data. By understanding how these powerful tools work together, we can ensure our patient’s confidential information remains safe while still allowing them access to the healthcare services they need when they need them most. Thank you for reading.
Continue Reading:
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.