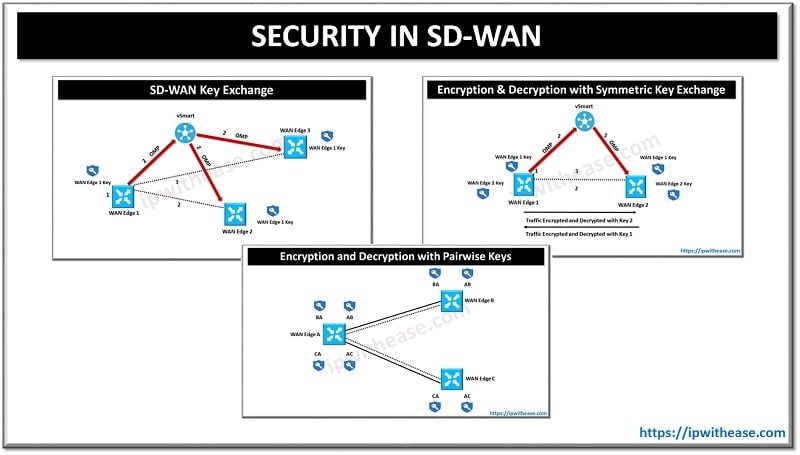
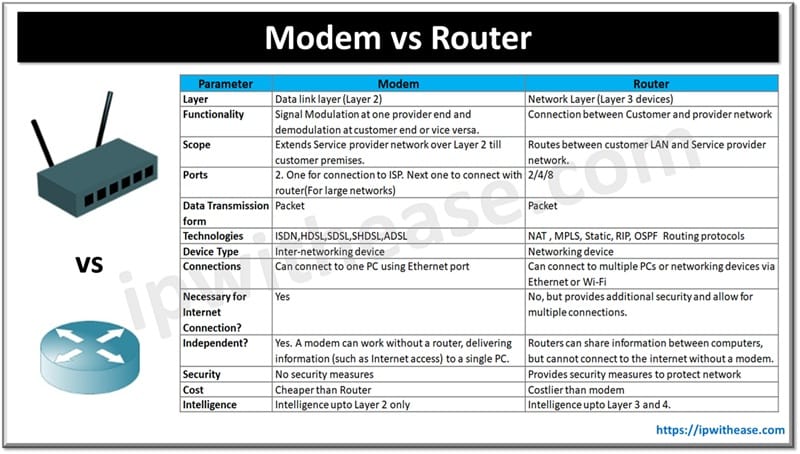
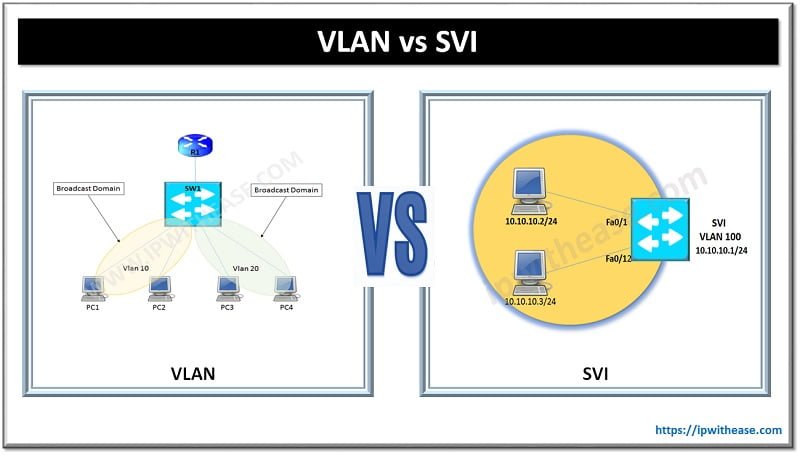
Table of Contents
This blog discusses 3 methods to configure route leaking between VRF and Global Routing table (GRT). Routes in VRF table can be leaked to Global routing table and traffic communication is possible. MP-BGP need not be implemented to meet the requirement.
Configuration Methods: Route Leaking between VRF and Global Routing Table
These 3 Methods mentioned below can be used on Route leak from Global Routing Table into the VRF table (VRF1) and vice-versa:
1. Route map and VRF Receive configuration
2. Static route Configuration
3. Dynamic routing Configuration
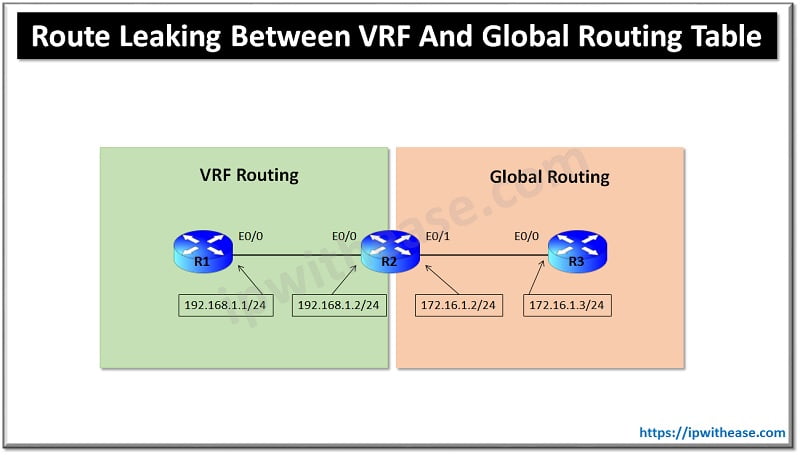
Method 1: Route Map and VRF Receive Configuration
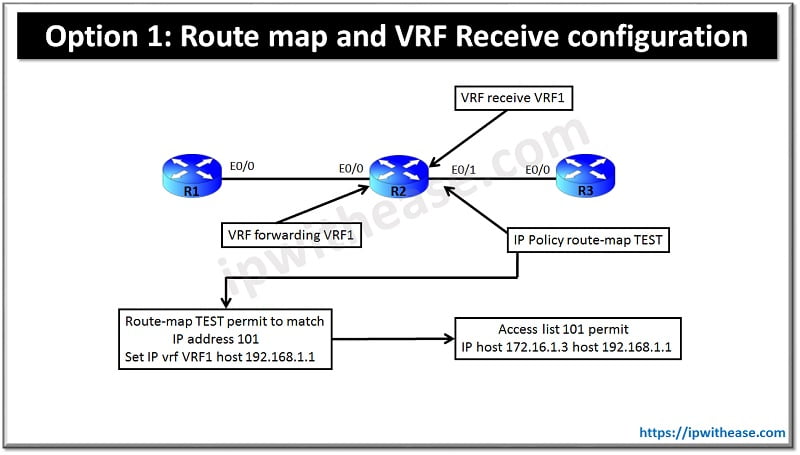
R1 Config
Interface Ethernet0/0
ip address 192.168.1.1 255.255.255.0
ip route 0.0.0.0 0.0.0.0 192.168.1.2R3 Config
Interface Ethernet0/0
ip address 172.16.1.3 255.255.255.0
ip route 0.0.0.0 0.0.0.0 172.16.1.2R2 Config
interface Ethernet0/0
ip vrf forwarding VRF1
ip address 192.168.1.2 255.255.255.0
interface Ethernet0/1
ip vrf receive VRF1
ip address 172.16.1.2 255.255.255.0
ip policy route-map TEST
access-list 101 permit ip host 172.16.1.3 host 192.168.1.1 <you can permit all the traffic here which needs to go to vrf>
route-map TEST permit 10
match ip address 101
set ip vrf VRF1 next-hop 192.168.1.1When we enter the command <ip vrf receive VRF1> it adds the connected subnet of the global interface to the vrf routing table and traffic from global to vrf is policy routed by the route-map applied under the under.
Verification
R2#sh ip route vrf VRF1
Routing Table: VRF1
Codes: L – local, C – connected, S – static, R – RIP, M – mobile, B – BGP
D – EIGRP, EX – EIGRP external, O – OSPF, IA – OSPF inter area
N1 – OSPF NSSA external type 1, N2 – OSPF NSSA external type 2
E1 – OSPF external type 1, E2 – OSPF external type 2
i – IS-IS, su – IS-IS summary, L1 – IS-IS level-1, L2 – IS-IS level-2
ia – IS-IS inter area, * – candidate default, U – per-user static route
o – ODR, P – periodic downloaded static route, H – NHRP, l – LISP
+ – replicated route, % – next hop override
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
<global interface route is seen in vrf VRF1 routing table>
C 172.16.1.0/24 is directly connected, Ethernet0/1
L 172.16.1.2/32 is directly connected, Ethernet0/1
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Ethernet0/0
L 192.168.1.2/32 is directly connected, Ethernet0/0Now if we ping from R3 to R1:
R3#ping 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/5/6 msMethod 2: Static route Configuration
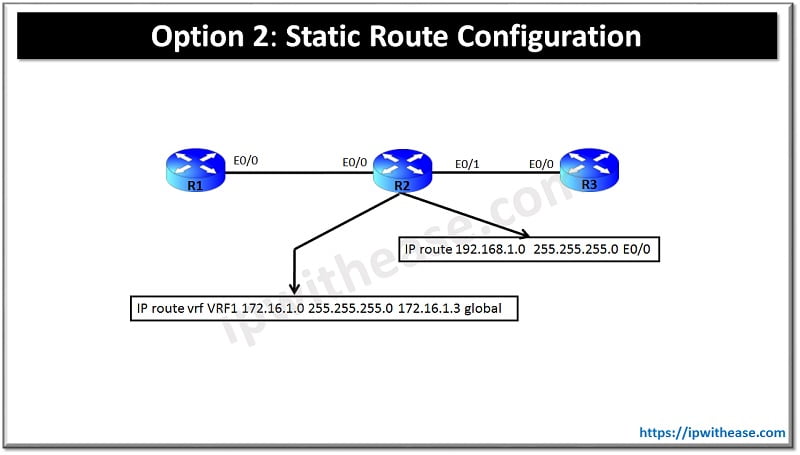
Note: Remove “ip vrf receive” and “route-map” from the R2 eth 0/1 interface.
interface Ethernet0/1
ip address 172.16.1.2 255.255.255.0
# add a route in global routing table for vrf subnet:
ip route 192.168.1.0 255.255.255.0 Ethernet0/0
# add a route in vrf VRF1 routing table for global subnet:
R2(config)#ip route vrf VRF1 172.16.1.0 255.255.255.0 ethernet 0/1
% For VPN or topology routes, must specify a next hop IP address if not a point-to-point interface
# <if we try with exit interface only it throws an error and route is not installed, we can use this if interface is point-to-point (i.e serial) as mentioned in error message >
ip route vrf VRF1 172.16.1.0 255.255.255.0 Ethernet0/1 172.16.1.3 global
# <Add following route with next-hop and global keyword.With global it looks for next-hop in global routing table>Verification
R2#sh ip route | include 192.168.1.0
S 192.168.1.0/24 is directly connected, Ethernet0/0
# <a static route is seen in the global routing table pointing to exit interface>
R2#sh ip route vrf VRF1 172.16.1.0
Routing Table: VRF1
Routing entry for 172.16.1.0/24
Known via “static”, distance 1, metric 0
Routing Descriptor Blocks:
* 172.16.1.3 (default), via Ethernet0/1 <next-hop lookup will occur in global routing table>
Route metric is 0, traffic share count is 1Ping Test
R1#ping 172.16.1.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 5/5/6 msMethod 3: Dynamic Routing Configuration
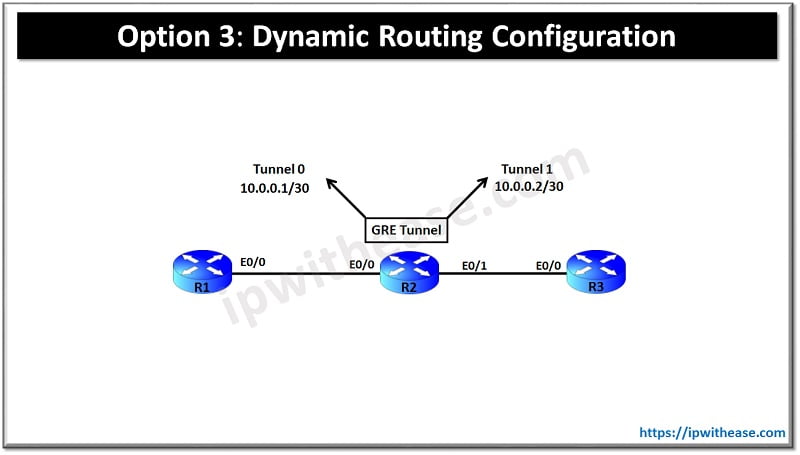
We will remove the static route and add 2 new loopback on router R2.
no ip route vrf VRF1 172.16.1.0 255.255.255.0 Ethernet0/1 172.16.1.3 global
no ip route 192.168.1.0 255.255.255.0 Ethernet0/0
interface Loopback0
ip address 2.2.2.2 255.255.255.255
interface Loopback1
ip address 22.22.22.22 255.255.255.255We will create 2 GRE tunnel on router R2 one in global and one in vrf VRF1.
interface Tunnel0
ip address 10.0.0.1 255.255.255.252
tunnel source Loopback0
tunnel destination 22.22.22.22
interface Tunnel1
ip vrf forwarding VRF1
ip address 10.0.0.2 255.255.255.252
tunnel source Loopback1
tunnel destination 2.2.2.2# We will now run a dynamic routing protocol on these tunnels & advertise the networks, i chose OSPF for this example.
router ospf 100
network 10.0.0.1 0.0.0.0 area 0 <tunnel interface>
network 172.16.1.2 0.0.0.0 area 0 <link between R2 and R3>
router ospf 200 vrf VRF1
network 10.0.0.2 0.0.0.0 area 0 <tunnel interface>
network 192.168.1.2 0.0.0.0 area 0 <link between R2 and R1>Verification
R2#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
192.168.1.2 0 FULL/ – 00:00:34 10.0.0.2 Tunnel0
22.22.22.22 0 FULL/ – 00:00:34 10.0.0.1 Tunnel1
R2#sh ip route ospf
O 192.168.1.0/24 [110/1010] via 10.0.0.2, 01:33:46, Tunnel0
R2#sh ip route vrf VRF1 ospf
172.16.0.0/24 is subnetted, 1 subnets
O 172.16.1.0 [110/1010] via 10.0.0.1, 01:34:37, Tunnel1Ping Test
R1#ping 172.16.1.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 5/6/13 ms
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
<global interface route is seen in vrf VRF1 routing table>
C 172.16.1.0/24 is directly connected, Ethernet0/1
L 172.16.1.2/32 is directly connected, Ethernet0/1
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Ethernet0/0
L 192.168.1.2/32 is directly connected, Ethernet0/0Related – VRF vs VRF Lite
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj