Table of Contents
The agile development methodology has revolutionized software development. Its core principles – rapid iterations, continuous feedback, and close collaboration – fuel faster time-to-market and a higher degree of responsiveness to customer needs. However, when agile development teams extend beyond internal borders to incorporate outsourced talent, the need for secure and reliable data access becomes paramount. Fortunately, secure networking solutions offer a robust and adaptable foundation for seamless collaboration in an agile environment.
The Challenge: Agility Meets Security
The beauty of agile development lies in its dynamic nature. Frequent code updates, continuous integration practices, and rapid deployment cycles necessitate a constant flow of data between developers. This holds true even when working with outsourced teams located geographically distant from the core development unit.
However, this emphasis on agility can clash with essential security considerations. Sharing sensitive information, intellectual property, and source code with external partners introduces inherent risks. Data breaches, unauthorized access attempts, and potential intellectual property theft can significantly hamper project timelines and cause financial damage.
Secure Networking Solutions: The Bridge Between Teams
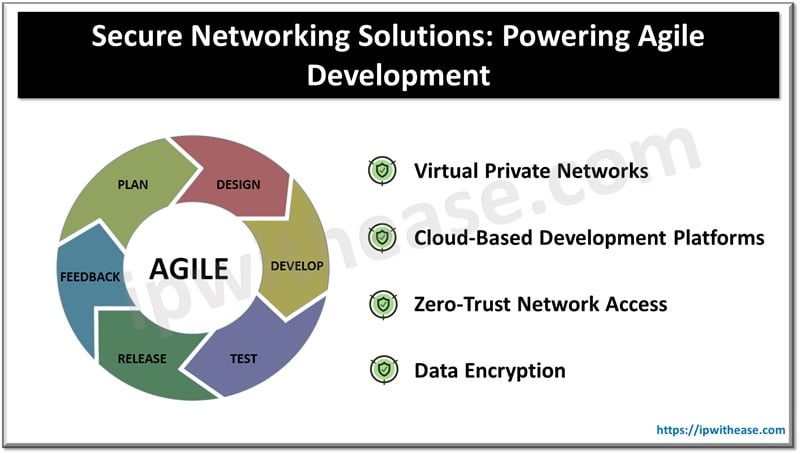
Secure networking solutions bridge this gap between agility and security. By employing a combination of technologies and protocols, they create a secure environment for collaboration within an agile development framework, even with outsourced teams. Here’s how:
Virtual Private Networks (VPNs)
VPNs establish secure tunnels over public internet connections. Data traversing the VPN tunnel is encrypted, making it unreadable even if intercepted. This allows outsourced developers to securely access project resources hosted within the organization’s network, ensuring data confidentiality.
Cloud-Based Development Platforms
Cloud-based development platforms provide a centralized repository for code, version control systems, and project management tools. These platforms offer built-in security features like access control mechanisms and user authentication, ensuring only authorized personnel, including outsourced developers, can access specific project resources. Cloud providers often replicate data across geographically dispersed data centers, enhancing redundancy and disaster recovery capabilities.
Zero-Trust Network Access (ZTNA)
ZTNA takes security a step further by eliminating the concept of implicit trust within a network. Instead, every user or device attempting to access a resource, regardless of location (internal or outsourced team), must undergo rigorous authentication and authorization checks. This approach minimizes the attack surface and reduces the risk of unauthorized access, even if a bad actor manages to breach the perimeter defenses.
Data Encryption
Data encryption scrambles information using complex algorithms, rendering it meaningless without the appropriate decryption key. This ensures that even if sensitive data is intercepted, it remains unusable. Secure networking solutions often integrate data encryption at rest (stored data), in transit (during transmission), and in use (while being processed) to provide comprehensive protection.
Benefits Beyond Security
Secure networking solutions offer benefits beyond just enhanced security.
- Improved Collaboration: Secure networking platforms create a centralized workspace where internal and outsourced teams can access the latest code versions, project documentation, and communication channels. This fosters smoother collaboration and streamlines the development process.
- Scalability and Flexibility: Secure solutions can be easily scaled up or down based on project requirements. This allows organizations to seamlessly integrate outsourced teams of varying sizes into the development workflow.
- Cost-Effectiveness: Secure cloud-based solutions eliminate the need for extensive investment in on-premise infrastructure for outsourced team access. This reduces hardware and software costs, resulting in a more cost-effective approach to development.
Considerations and Best Practices
While secure networking solutions offer a powerful toolset, it’s crucial to consider some key aspects:
- Security Policy and Training: A well-defined security policy outlining access controls, data handling procedures, and incident response protocols is essential. Regular security awareness training for both internal and outsourced development teams helps maintain a vigilant posture against potential threats.
- Data Classification and Access Levels: Classify project data based on sensitivity and implement granular access controls. This ensures outsourced developers like dedicated python development companies only have access to the information necessary for their specific tasks, minimizing the potential damage from unauthorized access.
- Regular Security Audits: Conducting regular security audits of the network infrastructure and cloud platforms helps identify vulnerabilities and ensure the effectiveness of implemented security measures.
The Future of Secure Networking for Agile Development
The future of secure networking for agile development is brimming with exciting possibilities. We can expect closer integration with DevOps tools, allowing for automated security checks within the development pipeline. This will catch vulnerabilities early and prevent them from becoming bigger issues later.
Additionally, with its dynamic approach, Software-Defined Networking (SDN) holds promise for agile teams. SDN grants more control over network infrastructure, enabling the provisioning of secure resources tailored to specific project needs. Biometric authentication methods like fingerprint scans and facial recognition are gaining traction as well. These offer a more secure and user-friendly way to verify users, further bolstering security within the agile environment.
Finally, the focus on Identity and Access Management (IAM) will intensify as user numbers and devices accessing development resources continue to grow. Robust IAM solutions will be essential for managing user identities, access privileges, and lifecycles, guaranteeing that only authorized personnel can access sensitive project data.
By embracing these advancements, secure networking solutions can continue to evolve hand-in-hand with agile methodologies. This empowers organizations to leverage a global talent pool while maintaining the agility, security, and efficiency that are hallmarks of successful agile development.
Securely Scaling Agile Development
By leveraging secure networking solutions, agile development teams can unlock the full potential of collaboration with outsourced partners, regardless of location. These solutions provide a robust and secure foundation for data exchange, fostering seamless collaboration in a dynamic development environment. Remember, security is an ongoing process, not a one-time fix. By implementing secure networking solutions alongside sound security practices and ongoing vigilance, agile development teams can embrace the benefits of outsourcing while ensuring project data and intellectual property remain protected.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.