Table of Contents
In today’s world, the ability to detect and respond to threats in real-time is paramount. Cybercriminals, adept at exploiting vulnerabilities, can quickly compromise networks, devices, and accounts. The challenge lies in identifying these threats amidst the data generated by the applications and accounts within a typical tech stack. So, Security Information and Event Management (SIEM) technology emerges as a critical tool, acting as a vigilant guardian by continuously monitoring and analyzing security events.
When cybercriminals infiltrate a network, the aftermath becomes a race against time. The sheer volume of data generated by various applications and accounts poses a challenge. SIEM technology serves as the magnet, swiftly detecting abnormal patterns or behaviors that could indicate a security threat. In this article, we will explore the role SIEM alerts play in the early detection of security threats and how organizations can optimize their SIEM solutions for effective threat management.
What is a SIEM Alert?
SIEM alerts serve as the frontline notifications that keep security professionals informed about potential security incidents. Thus, it is essential to understand what is a SIEM alert and how it works if an organization must effectively curb attacks and vulnerabilities. Constructed through the meticulous processes of detection, correlation, and aggregation, these alerts are the early warning system against cyber threats. Let’s look into the step-by-step process through which SIEM alerts come to life.
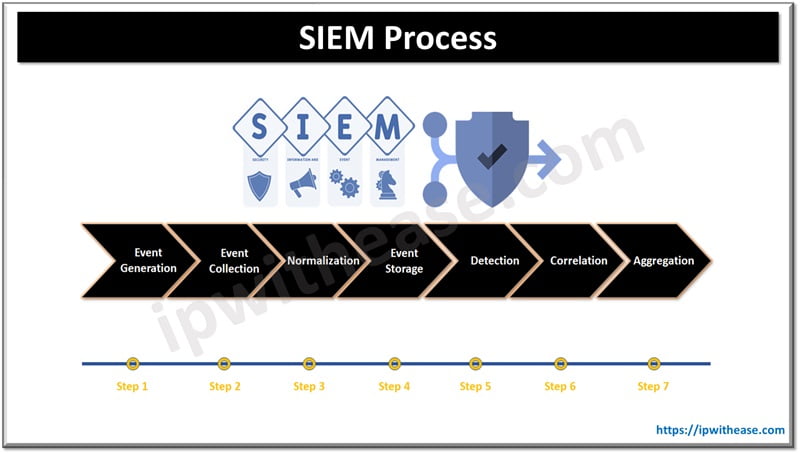
Event Generation
Every file within an organization’s on-premises or cloud environment generates a constant flow of logs. SIEM technology integrates with these log sources, gaining real-time insights into the processes supporting firewalls, intrusion detection systems, antivirus solutions, servers, and other security devices.
Event Collection
Not all logs are equal, and to discern their significance, SIEM must collect a broad spectrum of events from diverse sources, centralizing them for analysis.
Normalization
Events from different sources often use different formats and standards. SIEM’s normalization function standardizes these events into a common format, ensuring seamless analysis.
Event Storage
Normalized events find a secure home in a centralized database, facilitating historical analysis, compliance reporting, and forensic investigations.
Detection
The crux of SIEM’s functionality lies in its ability to detect potential security incidents. Using predefined rules, signatures, and behavioral analysis, SIEM identifies anomalies or patterns indicative of security threats.
Correlation
Correlation is a vital step that involves analyzing multiple related events to determine if they collectively represent a security incident. This helps in identifying complex attack patterns that might go unnoticed when examining individual events.
Aggregation
Combining related events into a consolidated view, aggregation reduces alert fatigue by presenting security professionals with a more concise set of alerts. This meticulous process culminates in the generation of a SIEM alert, providing vital details about the incident, such as the type of threat, affected systems, and the severity of the incident.
Different Types of Alerts In SIEM
SIEM alerts aim to provide a focused and prioritized view of potential threats, eliminating the need to sift through vast amounts of data. Here are some common types of SIEM alerts and their significance:
- Anomalous User Behavior: Alerts triggered by unusual user activity, such as multiple unsuccessful login attempts, unauthorized access to resources, or irregular data transfers.
- Monitoring System or Application Errors: Prompt alerts on critical errors or failures in systems or applications, revealing potential vulnerabilities or misconfigurations.
- Data Breaches: Alerts are generated in response to unauthorized access or the exfiltration of sensitive data, enabling prompt reactions to minimize impact.
- Compliance Violations: Customizable alerts that notify about regulatory violations or breaches of internal policies, ensuring adherence to established standards.
When anomalies are discovered, alerts are forwarded to a centralized Network Operation Center, SRE, or specific DevOps teams for a swift response. Apparently, SIEM solutions such as Stellar Cyber are very much committed to abiding by compliance and regulatory standards.
Types of Alert Triggers
SIEM alerts employ various triggers, each serving a unique purpose in identifying specific events or behaviors indicative of security threats.
- Rule-based Triggers: Frequently used in SIEM alerts, rule-based triggers rely on predefined conditions to identify specific events. Security teams establish rules based on diverse aspects, such as known attack patterns, indicators of compromise, or suspicious activities.
- Threshold-based Triggers: These triggers involve setting specific thresholds or limits for events or metrics. When these threshold values are breached, the system generates an alert. This proves valuable in detecting abnormal behavior or deviations in patterns.
- Anomaly Detection: A vital component aims to identify deviations from anticipated behavior. Anomaly detection analyzes historical data to establish baseline profiles for routine activities, flagging noteworthy deviations as potential anomalies.
These triggers work cohesively, creating an adaptive layer of ticketing that aligns with pre-existing platforms. Some solutions like Stellar Cyber take it a step further, employing Artificial Intelligence (AI) and Machine Learning (ML) to identify correlation patterns across diverse alerts.
Best Practices for Managing SIEM Alerts
The efficacy of SIEM tools lies in their ability to detect threats without overwhelming security teams with a barrage of alerts. Implementing best practices ensures that SIEM alerts contribute to threat detection rather than causing alert fatigue.
- Set Your Own Rules: Rules define the understanding between normal and malicious behavior within a SIEM system. While a single alert can have multiple rules, creating an excess of customized alerts clouds security insight.
- Check Your Alerts Before Issuing New Ones: Before implementing fresh alert rules, a thorough review of existing alerts is essential. Identifying built-in alerts serving the same purpose prevents redundancy, and collecting information about the sequence of events provides context.
- Be Precise When Choosing What to Flag: Alert flooding often results from vagueness or ambiguity in alert descriptions. Precise descriptions and accurate categorizations reduce the likelihood of mundane issues appearing in high-priority workflows.
- Keep Regulations In Mind: Creating custom alert rules should align with various local, regional, and federal laws governing cybersecurity. Adherence to regulations is vital for maintaining a robust security posture.
- Rely on Both Simple and Composite Rules: While basic rules identify specific event types, composite rules enable the identification of patterns. Rigorous testing of custom alerts is imperative to refine correlation rules, ensuring optimal performance.
- Set and Tune Thresholds: Threshold-based triggers require regular tuning, especially when factors like an expansion in user base can lead to unnecessary alerts. Continuous refinement of thresholds ensures the relevance of alerts to the environment.
- Define Your Anomalies: Behavior models that profile users, apps, or accounts based on standard behavior are vital. Defining risk tolerance for each model is critical in managing and controlling the volume of alerts generated.
Conclusion
SIEM alerts are the unsung heroes of a robust security infrastructure. They serve as the eyes and ears of an organization’s security operations, providing real-time insights into potential threats and vulnerabilities. So, understanding the intricacies of SIEM alerts, from their inception through event correlation to the implementation of best practices, is paramount for organizations aiming to fortify their cybersecurity defenses.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.