Table of Contents
In the present digital age in which we live, data is the most valuable asset for any organization. Protecting that data from leaks, theft, or misuse, which used to be a choice before, is now a must. That is the role played by Data Loss Prevention. What is data loss prevention, how does data loss prevention software work, and what steps are required for a successful and effective implementation?
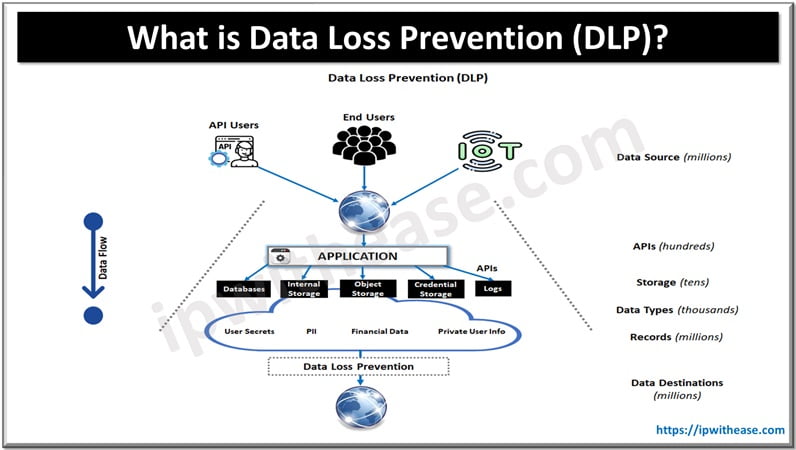
What is Data Loss Prevention?
Stored within servers, in motion across networks, or in use at endpoints and applications.
At its root DLP implements rules that govern how data is used, shared, and protected. Organizations use data loss prevention software for the automatic identification of sensitive data, classification of that data, tracking its movement, and prevention of its unauthorized transfer. Also, these tools may drop risky actions, encrypt files, or sound an alert when a policy violation occurs.
Why Organizations Need DLP
In today’s business environment DLP is a key issue, which also brings into play:
- Protecting intellectual property, personal information, and financial details.
- Meeting data protection standards as they pertain to GDPR, HIPAA, and PCI DSS.
- Reducing the risk of insider incidents, which may result from carelessness, mistakes, or malice.
- Maintaining trust and reputation through avoidance of large-scale breaches.
Step 1: Define Business Needs and Stakeholders
The first in line for DLP implementation is to align the initiative with business objectives. Organizations must put forward what they are to achieve via DLP, which may be for compliance, intellectual property protection, or general data privacy. Also included is the identification of stakeholders from across departments—from IT and security to compliance and business leaders—which in turn secures support for the initiative.
Step 2: Discover and Classify Data
Before creating rules, determine what is being protected. At this stage teams identify sensitive data across the organization, which includes servers, endpoints, and cloud platforms. Once discovered, it is put into categories like public, internal, confidential, or regulated. Classification of the data in turn ensures that the most critical info is given the highest level of protection.
Step 3: Establish Policies and Governance
Effective DLP includes having well-defined policies. Teams determine which groups own what data, how that data is to be treated, and what is off-limits. Policies should present what is and is not ok behavior, e.g., whether it is fine for staff to send out sensitive files. Also, governance issues of which groups respond to alert notifications and which ones change the policies over time are made clear.
Step 4: Select the Right Data Loss Prevention Software
Not all DLP products are the same. Organizations do well to choose the software that supports their infrastructure, which may be on premises, in the cloud, or a mix of both. Look for what the product does in terms of content inspection, encryption, user activity monitoring, and also contextual analysis. It is often best to start out with a proof of concept, to put the tool in “monitor only” mode, which in turn will give an idea of normal data flow before very strict controls are put in place.
Step 5: Roll Out Policies Gradually
At first organizations may monitor and alert, then implement more drastic actions like blocking or quarantining of data transfer. This is done in order to minimize disruption to regular workflow at the same time as improving policies.
Step 6: Train and Engage Employees
Technology in itself does not prevent data loss. Companies must see to it that employees are aware of what is sensitive data, why policies are important, and how to be a part of them. Training should include proper info handling, report procedures, and what to expect from noncompliance. Ongoing communication is the key for staff to stay in the loop as policies change.
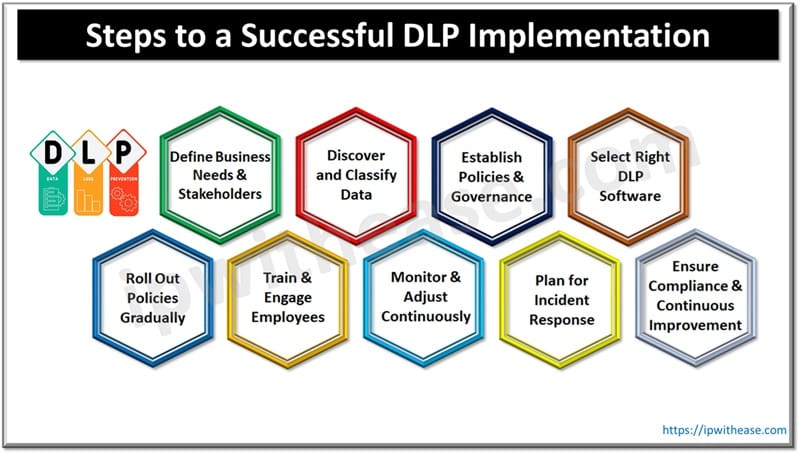
Step 7: Monitor and Adjust Continuously
Once the system is put in place, continuous monitoring is key. Organizations look at alerts, logs, and reports at regular intervals to identify any violations. Also, they evaluate if policies are too strict, which may cause false positives, or not strict enough, which may miss threats. Fine-tuning is what keeps DLP effective and also makes it responsive to business and regulatory changes.
Step 8: Plan for Incident Response
In the wake of a breach, companies will look at the cause and also work to remediate vulnerabilities. They should also learn from these incidents and apply that knowledge to strengthen the DLP program for the future.
Step 9: Ensure Compliance and Continuous Improvement
DLP is a continuous program not a one time project. Businesses do regular reviews, audits and updates to align it with new laws, changing business requirements, and threats which emerge from the cyber world. They also put in place metrics like the number of data exfiltration attempts blocked or the reduction in policy violations which help measure success.
Common Challenges in DLP Implementation
- False positives and user frustration are minimized by putting policies into monitor mode and including employees in reviews.
- In some cases data may be left out which in turn may be a result of ignoring shadow IT or cloud apps; regular audits help to identify and fill in these gaps.
- Balanced productivity and security has in it policies that are flexible and to the context.
- As threats and regulations evolve, policies must be reviewed frequently to improve their effectiveness.
The Importance of DLP Software Features
Picking the right data loss prevention software is key to a successful implementation. Try out products which:
- Comprehensive data discovery and classification
- Monitoring of live, static, and in use data.
- Contextual analysis of user activity
- Flexible actions that include alerting, blocking, or encryption.
- Integration with existing security infrastructure
- Scalability to handle future growth
Conclusion
A successful DLP program is a mix of strategy, technology and culture. Organizations identify business needs, discover and classify data, put in place strong policies, choose the right tools, train staff, and constantly monitor and improve.
When performed as it is meant to be, DLP protects sensitive info, achieves regulatory compliance, reduces insider risks, and in the process improves organizational trust. By doing so and by also using the best software solutions companies may put in place the base for great data security over the long term.
Continue Reading
DLP Techniques & Best Practices
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.



