Table of Contents
In the current world, which is characterized by escalating cyber hazards, it is essential that every company’s IT infrastructure is secured. A strong IT system will guard against unauthorized access to sensitive data and keep businesses operational by mitigating avoidable risks. The following are some tips that can be followed to enhance IT security measures.
Measures to Strengthen IT Security
Make Regular Patching of All Systems an Obligation
Ensure there is a reliable system for applying security patches to the organization’s software, operating systems, network devices, and firewalls. Adopt an efficient patch management program to minimize vulnerabilities through prompt application of updates. To protect computers from threats by viruses or hackers, users of Microsoft Windows and Mac should regularly update their computers with the latest security patches while also configuring systems for automatic updates where possible or manually checking for updates. Through this proactive approach, security weaknesses can be addressed before they become exploitable vulnerabilities for hackers.
Keep Access Control Robust
System and data security are paramount. This is why it’s essential that you implement strict control over who has access to them in your company. The best you can do to achieve this is to implement a strong multi-factor authentication (MFA) system. This will prevent unauthorized people from accessing these systems.
You should put role-based access control (RBAC) mechanisms in place. This will ensure that only those who need specific information are granted access. It is advisable to review permissions periodically as organizational requirements and staff roles change. Additionally, consider using privileged access management (PAM), which combines high-risk account administration with the principle of least privilege by granting only job-related privileges. This will help strengthen your security architecture at all levels. It will also help address both internal and external threats.
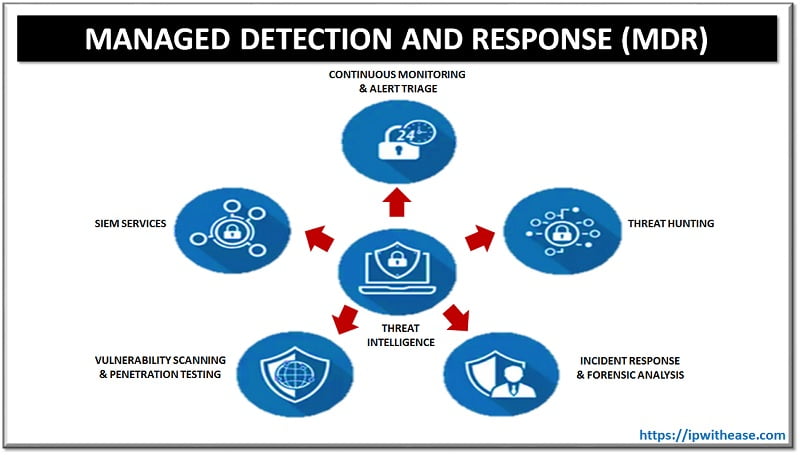
Utilize Managed Detection and Response (MDR) Services
Outsourcing to Managed Detection and Response (MDR) services will improve your cybersecurity posture. MDR providers have brought advanced technology as well as expertise into the game including continuous network monitoring, swift incident detection, and responsive actions. By using these tools, they gain further insights into their current security status while at the same time being secured round-the-clock. It also helps companies meet compliance standards, hence reinforcing their commitment to data security.
When choosing an MDR provider, consider their experience, reputation as well as compatibility with the existing security infrastructure in place. Such service level agreements (SLAs) must clearly define their responsibilities together with performance metrics.
Always Update Software and Systems
The punctual update of software and systems is important to the protection against known weaknesses. Be sure you are aware of security alerts and implement patches promptly to minimize exposure to risks that may come attached. Automate patching where available as a way of reducing human mistakes and ensuring updates take place on time. Have a vulnerability management system in place that can identify and prioritize vulnerabilities for patching. It’s better to test patches first in an environment with controlled access than rolling them out directly to production systems.
Train Your Employees
Company employees play a key role in maintaining a secure IT environment. Therefore, it is necessary to carry out comprehensive security awareness training that will detail common threats, best practices, and the importance of reporting suspicious activities. This calls for the cultivation of a security-conscious culture by all within so that everybody helps in safeguarding assets belonging to organizations. Use interactive modules, phishing simulations, and regular awareness campaigns on critical security topics to further enhance this idea. Training must be ongoing with new threats leading to new updates being added continuously. Recognize employees who detect or report any incidents involving insecurity.
By adopting this comprehensive strategy towards strengthening your organization’s IT security posture, your ability to adjust regarding cyber-threats will get improved besides enhancing its defense mechanism against such attacks.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.