Table of Contents
Cybersecurity threats are no longer just hypothetical risks; they are a daily reality for businesses and individuals alike. From ransomware attacks paralyzing critical infrastructure to data breaches exposing sensitive customer information, the stakes have never been higher. To combat these persistent threats, organizations must pivot from reactive measures to proactive strategies. This is where threat intelligence tools come into play.
Far from being mere add-ons, these cyber threat intelligence tools serve as the backbone of a vigorous cybersecurity framework. They analyze vast amounts of data to identify potential threats, detect vulnerabilities, and provide actionable insights that enable organizations to get ahead of risks and mitigate it before they escalate. By integrating threat intelligence into their strategies, businesses can effectively safeguard their operations, protect sensitive information, and stay one step ahead of cybercriminals.
In this article, we delve into the importance of threat intelligence in cybersecurity, the benefits of threat intelligence tools, and how they empower cybersecurity strategies with threat intelligence. Additionally, we will learn their critical roles in vulnerability management, supply chain risk management, and third-party risk management solutions.

What is Threat Intelligence?
Threat intelligence refers to the collection, analysis, and interpretation of information about potential cyber threats. This information helps organizations understand the tactics, techniques, and procedures (TTPs) used by threat actors. By leveraging this data, companies can reinforce their defenses and respond proactively to emerging risks.
Threat intelligence tools are designed to automate this process, providing organizations with actionable insights in real time. These tools are offered by various threat intelligence companies and come in the form of threat intelligence platforms and solutions tailored to specific business needs.
The Importance of Threat Intelligence in Cybersecurity
With cyber threats becoming more refined and unpredictable, the ability to detect and address risks before they unfold has become crucial.
Here are some key reasons why threat intelligence is essential in modern cybersecurity strategies:
- Proactive Defense: Threat intelligence enables organizations to predict and prepare for potential attacks, minimizing damage and downtime.
- Enhanced Decision-Making: Actionable intelligence supports better decision-making by identifying the most critical threats.
- Real-Time Protection: Real-time threat intelligence solutions ensure organizations are always updated about the latest threats.
- Customized Responses: Tailored threat intelligence helps businesses address specific vulnerabilities and risks unique to their operations.
- Improved Resource Allocation: By focusing on high-priority threats, companies can allocate resources more effectively.
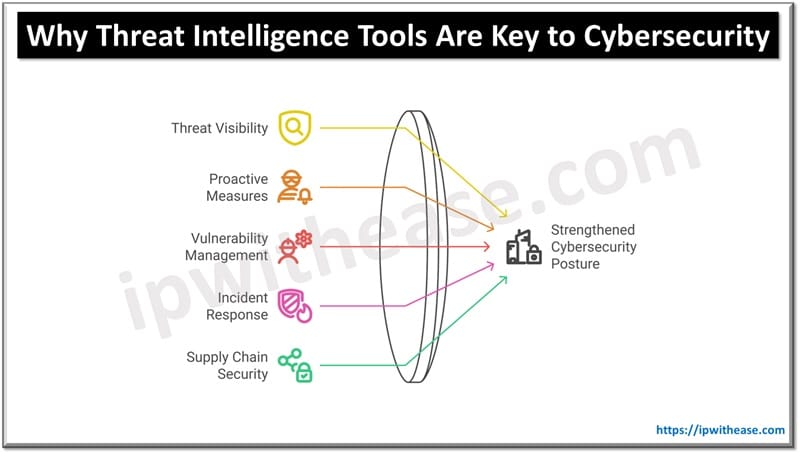
Benefits of Threat Intelligence Tools
The benefits of threat intelligence tools are numerous, making them indispensable in any cybersecurity strategy:
- Comprehensive Threat Visibility: These tools provide detailed insights into global threat landscapes, including emerging trends and active campaigns.
- Proactive Cybersecurity: Threat intelligence tools empower organizations to take preventive actions, reducing the risk of successful attacks.
- Streamlined Vulnerability Management: By identifying and prioritizing vulnerabilities, organizations can focus their efforts on fixing the most critical issues.
- Enhanced Incident Response: Threat intelligence data accelerates detection and response times, mitigating the impact of cyber incidents.
- Third-Party and Supply Chain Risk Management: Organizations can assess risks posed by vendors and partners, ensuring comprehensive security across the supply chain.
How Threat Intelligence Enhances Cybersecurity Strategies
Building strong cybersecurity strategies with threat intelligence is key to staying ahead in today’s threat landscape. Let’s explore how organizations can integrate these tools into their overall security posture:
1. Proactive Cybersecurity Measures
Integrating threat intelligence for proactive cybersecurity allows businesses to anticipate attacks before they happen. By identifying potential risks, organizations can develop countermeasures and reduce the likelihood of a breach.
2. Vulnerability Management
Threat intelligence tools play a crucial role in vulnerability management by:
- Identifying known vulnerabilities in software and systems.
- Prioritizing patches based on the level of risk.
- Reducing the window of exposure to potential exploits.
3. Real-Time Threat Detection
Real-time threat intelligence solutions provide continuous monitoring, alerting organizations to new and emerging threats. This enables quicker detection and response, reducing the damage caused by incidents.
4. Third-Party Risk Management
In a hyper-connected business environment, third-party relationships are unavoidable. However, they also pose significant risks. Threat intelligence tools help organizations:
- Assess the security posture of vendors and partners.
- Identify risks in the supply chain.
- Implement third-party risk management solutions to mitigate these risks effectively.
5. Supply Chain Risk Management
Cyberattacks targeting supply chains have become increasingly common. Using threat intelligence platforms, companies can:
- Map their supply chain to identify vulnerabilities.
- Monitor for threats targeting suppliers.
- Collaborate with partners to strengthen security measures.
Key Features of Threat Intelligence Products
Modern threat intelligence products are equipped with features that cater to diverse organizational needs:
- Automated Threat Feeds: Continuously updated data on global threats.
- Advanced Analytics: AI-driven insights to identify patterns and trends.
- Customizable Dashboards: Tailored views for monitoring specific risks.
- Integration Capabilities: Seamless integration with existing security tools like SIEM and SOAR systems.
- Incident Reporting: Detailed reports to support investigations and compliance efforts.
Choosing the Right Threat Intelligence Solutions
With numerous threat intelligence companies offering a variety of tools, selecting the right solution can be daunting. Here are some factors to consider:
- Relevance: Ensure the tool provides intelligence tailored to your industry and operational needs.
- Scalability: Choose a solution that can grow with your organization.
- Ease of Use: The platform should be user-friendly and require minimal training.
- Integration: Ensure compatibility with your existing cybersecurity infrastructure.
- Vendor Reputation: Opt for trusted threat intelligence companies with a proven track record.
Real-Life Applications of Threat Intelligence
To illustrate the impact of threat intelligence, here are some real-world examples:
- Financial Institutions: Using threat intelligence platforms, banks can identify phishing campaigns targeting their customers, enabling swift mitigation.
- Healthcare Organizations: Threat intelligence helps hospitals detect ransomware attacks, protecting sensitive patient data.
- Manufacturing Firms: By monitoring their supply chain, manufacturers can identify and address risks posed by third-party vendors.
Conclusion
The evolving cyber threat landscape necessitates the adoption of advanced tools and strategies to protect organizational assets. Threat intelligence tools are no longer optional; they are essential for building a resilient security posture. By providing actionable insights, these tools empower organizations to anticipate and counter threats effectively.
Moreover, by integrating threat intelligence into your cybersecurity framework, you can transform your defenses from reactive to proactive, ensuring long-term resilience in the face of ever-evolving threats.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.