Advertisements
 ANSWERS @https://ipwithease.com/shop/
ANSWERS @https://ipwithease.com/shop/
- Firewalls are part of almost every network. Over the past few years firewalls have evolved from a legacy networking device to a next level advance security appliance. Juniper SRX series is an advance form of next generation firewalls. Can you tell which naming convention Juniper uses for its firewall series?
- What is the main difference between different models of Juniper SRX series service gateways and if you are working in company as a presales engineer, what will be your criteria for selecting the right model of SRX for your enterprise or your customer?
- How would you differentiate between legacy firewalls and next generation firewalls in simple terms?
- Which are 2 ways you can access and operate SRX services gateways for configurations and operations purposes?
- SRX series firewalls can be deployed in any network environment. Juniper however categorized the deployment scenarios into two main types. Can you name those and brief about their differences?
- JUNOS is designed for all Juniper devices as a consistent OS. JUNOS by design consists of two planes. Can you mention those planes in which all JUNOS devices works?
- What is the dedicated management interface for managing SRX series?
- You are working as network security engineer in a large enterprise, you must be very well aware of interface conventions and types on your firewalls. Can you give example of such interface, which is a gigabit Ethernet interface in slot 2, module 3 and port number 5?
- SRX series is based on Juniper JUNOS software. One of the key points of JUNOS is that all processes are independently running and are not having any dependency on other process. What is the main advantage of having separate processes in kernel?
- You are working as a network engineer with many Junos platforms in the network. One command, which you may use in any platform including SRX to see the status of online interfaces and their IP details, would be?
- As a network admin, you are assigned a task to get the complete active inventory of the SRX series along with PIC, FPC, PEM etc. You need to run a single command, which may give you the complete details along with serial numbers of SRX chassis, both in standalone and cluster mode. What command would you run?
- You are newly hired as an implementation engineer in a company, which needs to roll out a big project for deploying SRX series in many locations. As a part of staging which are basic steps you will perform to configure initial setup of SRX firewalls?
- You are making many changes in firewall and before committing those changes, need to be 100% sure all is properly configured. Still you are concerned of losing the SRX remote connection. You need to make sure the commit is roll back in case of such a scenario. What is the best approach to deploy such changes on SRX?
- SRX traffic flow is based on first path or fast path once a packet enters into SRX. Can you briefly explain what is the difference between these two packet flow mechanisms?
- When you log into SRX firewall via telnet or ssh, what are the two modes on CLI and how would you briefly explain them?
- You are involved in a maintenance window to make several changes and update many policies on SRX firewall. You are almost done with making configurations, just to verify before committing you need to see the changes that were made by you. Which command will help doing that?
- While troubleshooting on SRX, you suspect that some of the processes are not functioning as expected. Which command is best way to see the processes running on the SRX platform?
- You need to configured interface ge-0/0/0 with an ip address 192.168.1.1/30 having unit 0. Which are the two ways you could do that in SRX?
- You were involved in an activity where you made many changes to existing policies in SRX. You did such changes last week on a specific date, and since then there is a complaint from a particular department about some services not working. You want to see and compare the changes that were done last week on that particular date; what is the best way to do that?
- Which Junos interface commands takes the untagged traffic and mark it with VLAN tag by the means of configuring the SRX port as access port Ethernet-switching port?
- On SRX, if required sometimes you have to connect it to another switch as trunk port, which carries multiple VLANs. Which command will configure an SRX port ge-0/0/0 as trunk?
- While working on JUNOS configuration mode, which command is used for adding new configuration and which keyword is used to remove the existing configuration line?
- You need to configure one interface with VLAN tagging enabled and assigning vlan 500 on it. What exact configurations would accomplish this task?
- Juniper gives a firewall cloud solution for private and public cloud infrastructures. What is the name of such solution for Juniper?
- What is the main purpose of Functional Zone in SRX series? In addition, why is it configured?
- What are the two different traffic flow modes in which SRX can operate? What is the default operation mode of SRX?
- You have deployed pair of SRX firewalls in cluster High Availability scenario, ensuring the redundancy in the network. In order to check the status of the cluster which command you shall use?
- SRX makes use of fast path flow processing. There are steps in which SRX makes these checks and then makes sure the packet is to be fast processed or not. Mention the steps in both case of first path and fast path processing flow?
- Any firewall is based on its rules that allow any traffic to pass, block or discarded. Junos also gives the flexibility of configuring firewall security rules. Which term Junos uses for its firewall rules?
- In SRX series, all the traffic interfaces ideally are part of security zones. Security zones are fundamental part of SRX platforms for deploying policies. Briefly explain about security zone and how is it useful in deploying security policies?
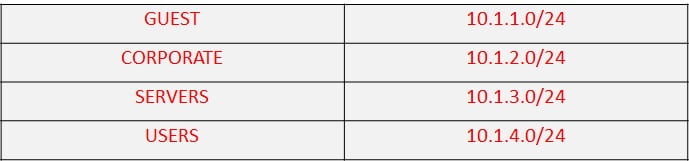
- You are working as a network Security engineer, and given a task to create multiple security zones in the SRX, as per below table-
 Mention the configuration you need to make such security zones?
Mention the configuration you need to make such security zones? - In Juniper SRX, we have to deal with so many networks, IP addresses etc. It will be a nightmare for someone remembering all those addresses and networks especially when it comes to using them in policies. What is the easier way to solve this problem?
- What are the main two broad categories of NAT?
- In your enterprise, you have multiple security zones, your LAN interfaces on SRX are placed in zone name Trust. Moreover, you have no issue on opening some services like ping, ssh and ftp on this zone. Please mention the necessary commands to allow these services in the trust zone?
- Configure the global address book based on below table.

- Which type of address book does not require any security zone attached to it and is available throughout in the SRX platform to be used?
- You have a requirement of configuring a very large address objects, a regular address book is not easy to manage such a large pool of addresses and networks. What is the next option you can use in juniper SRX platform?
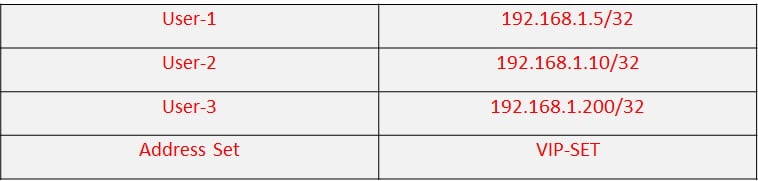
- Create an address book with address set in it calling multiple addresses. As per below table

- You are making address set with many addresses, some of those addresses belong to different security zones, and do you think this will work? Explain briefly?
- Is it possible to name the address set and address with same name?
- An entity, which controls traffic from specified source to specified destination using a specified service permitting or denying it, is called?
- You have been troubleshooting some issues in your network. In order to make sure your ping is not blocked by SRX; you need to make a security policy to allow the ping between LAN users from Guest zone to corporate zone. Define such policy in order to allow the icmp i.e. ping.
- You have allowed icmp to go from zone Guest to zone Corporate, the ping however, when you initiate from corporate network is not working. Explain the issue here and how can it be solved?
- Mention briefly the main components needed for any security policy to be applied?
- In SRX traffic flow, a number of checks are performed before a packet is allowed to pass, screens, firewall filters and security policies and check that every packet has to go through. Where is the security policy checked in this process?
- You have been given task for making a new zone for network admins, named ADMINS. After making security zone, you need to make a security policy in which you will allow all traffic initiated from ADMINS zone towards Internet zone.
- You have to define security policy where your need to reference multiple source zones i.e. from-zone and multiple destination zones i.e. to-zone. A single policy is not able to do so, so what is the best way to avoid multiple policies across every possible context?
- Juniper SRX provides very powerful mechanism to protect against internal and external attacks. What is the name of this mechanism?
- You want protection on untrusted interface facing WAN i.e. Internet side from icmp flooding and TCP attacks. You are committed to use screens on this Internet zone. Define the basic configurations you will do to achieve this?
- You have developing security policies, but need additional feature to add dynamic applications like ‘Facebook’, ‘google’ services to be allowed or blocked by your policy. Which feature in SRX will you use to achieve this?
- Juniper has developed a sophisticated advance level security solution to protect the businesses from cyber-attacks and malwares. This solution is cloud based and uses real time information for updates. Can you name this solution?
- Briefly, explain how sky ATP mechanism works and connects with Juniper cloud to get latest information?
- What is the main reason for network address translation we have today in almost all the networks in the world?
- What are the three main types of NAT, which we use all around the networks for almost all the time?
- During the packet flow processing, NAT rules are inspected to see the destination of the packet. What is the order of different types of NAT while processing the packet?
- You are a normal user in your enterprise. If you view network settings, you will notice that you are assigned a private IPv4 address 192.168.1.23/24 from DHCP server. However if you go on the internet to check the IP address you are getting online with you notice that IP address is a public IP with totally different range. You have an SRX firewall in your network which is translating your private IP pools to public IP address. Can you tell which type of NAT is being used in such scenario?
- You have a public IP address configured on the outside WAN internet facing interface of your SRX firewall. In addition, you have multiple private IP pools of /24 masks to be translated to this interface Public IP. What kind of NAT is being used here? And is there any other term used for this kind of NAT?
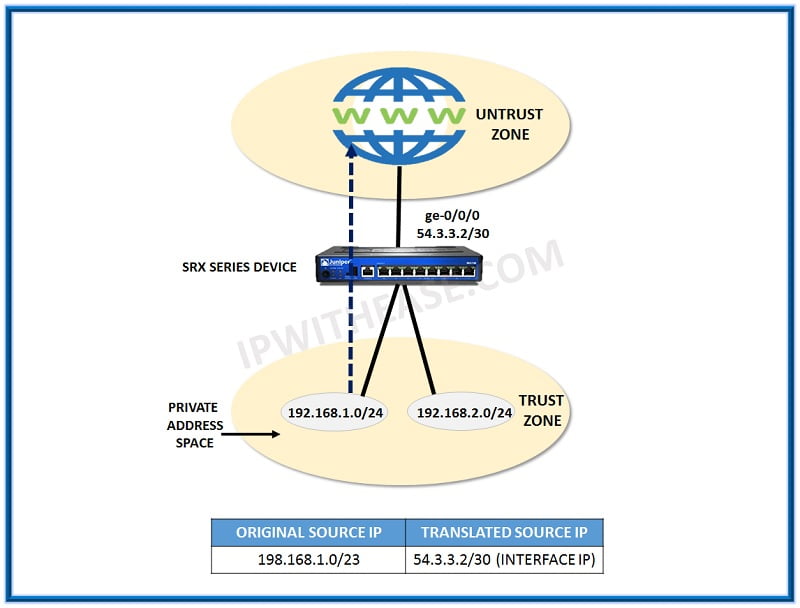
- We have a network where users are allocated the private IP range of 192.168.1.0/24 and 192.168.2.0/24 and they need to be translated as source NAT to public IP 54.3.3.2 which is already configured on SRX outside Internet facing interface. The below diagram shows this scenario. Make the basic set of source NAT based on PAT configurations in this case?

- You are troubleshooting the NAT settings, and realize all configurations are working fine. You need to see if the translations are being done correctly on SRX or not. Which operational command would you use to see the real time translation?
- You are working as a network engineer and your main servers are hosted in private cloud with private IP addresses configured on them. However, you wish to remotely access your servers and for that, you have devised a way to translate their IP to public IP so that if you access the public IP remotely you will be redirected to the private IP address of your server within your network. What type of NAT you will need in this scenario?
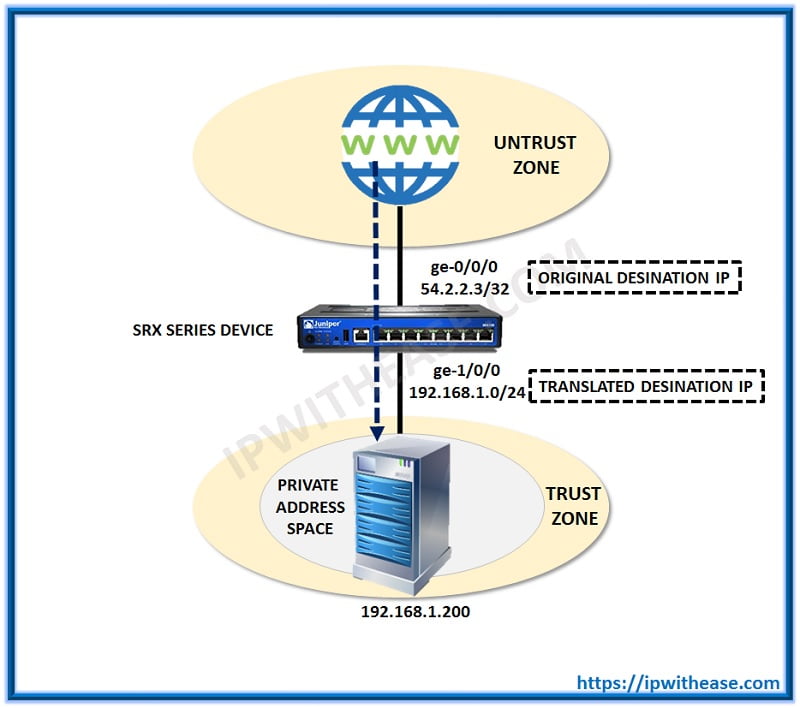
- You have a situation where you need to access the private hosted server using the public IP address give to you. You are supposed to configure Destination NAT on SRX. Define basic rules for such NAT to make sure a user from internet can access this private server easily.
Public IP: 54.2.2.3
Private Server IP: 192.168.1.200/32

- You have configured destination NAT and now you just want to verify if the applied configuration have taken effect properly. Which operations command would you use instead of checking the configuration to verify this?
- Name the supported hypervisors where vSRX can be deployed and installed?
- Which type of NAT is used to allow one to one mapping between source and destination address pools? In which sources addresses are translated in one direction and destination addresses in reverse direction.
- You have two sites in different geographical locations. You need a secure way to access the systems across these sites on daily basis, what is the best way to do it securely and efficiently?
- How many types of IPSEC VPN topologies you can deploy in SRX series firewalls? Briefly explain all these types of topologies.
- What are the two modes in which IPSEC operates?
- The IPSEC VPN goes through multiple phases before it gets completely established and comes to UP state. These phases are commonly known as VPN negotiations. Can you explain how many phases are there and briefly describe what each phase does?
- You have been using ESP protocol for establishing IPsec tunnels. You must know which 3 types are supports on SRX platforms?
- Juniper Unified Threat Management solution has very strong feature of Antispam filtering. Briefly explain about antispam feature and why is it so important in our daily routing?
- During IPSEC configurations setup, you are asked to use which mode between “Main” or “Aggressive”. Briefly explain what are the main differences between these 2 modes?
- You are troubleshooting the IPsec VPN and do not have idea where to start from. However, you know that there are two Phases i.e. Phase 1 and Phase 2, which takes place between two peers trying to establish VPN between each other. Which Phase you will troubleshoot first and why?
- You are working as a network security engineer and recently a new IT policy has been approved in which main aspect is to allow users for internet access in main office timings only. Which Feature on SRX will you use to accomplish this task?
- Juniper Unified Threat Management i.e. UTM is a consolidated mechanism to protect against various attacks and problems occurring in daily routine of IT management. Name basic features of UTM?
- A virtual private Network i.e. VPN has been in use all over the world for almost every network. Briefly describe what a VPN is and what advantage it gives us?
- Which zone is a system defined zone in Juniper SRX?
- After a SRX firewall has successfully processed first packet from a session, how are then the subsequent packets using same flow and session would be processed?
- As a network security engineer, you deal with troubleshooting IPsec VPNs on daily basis; you should have a process in place to go through a checklist for confirming and troubleshooting IPSec VPN. Briefly, explain what steps or checklist you should follow to troubleshoot IPSec?
- What is the main function of Screen Option in Junos Platforms? Briefly, explain?
- As a routine task, you get to add new policies almost every week in your SRX devices across your network. As per the criteria the newly added polices are added exactly where in the existing polices list?
- You are supposed to verify your VPN settings as you just finished off working in setting up the phase 1 and phase 2 configuration on both ends of the SRX. Which troubleshooting command will let you verify the Phase 1 is successfully working and in UP status?
- You have been establishing the VPNs across your office networks for quite some time as needed by your corporate IT policy. You should know the main protocols used by IPsec and AH i.e. Authentication Header is one of them. Explain briefly about AH?
- Which protocol is responsible to provide the IP security over the WAN links on public internet cloud in VPN connections?
- When it is mandatory to use IPSEC tunnel mode in setting up VPNs?
- What is the correct order in which Juniper Platforms assess and evaluate the packets in terms of policies, i.e. Security policy, Global policy or any default policy?
- Name valid zone types in SRX device, which are used all time?
- You are supposed to establish IPsec between your head office and multiple branches, to secure the communications between your office sites across the country. You have used all the parameters on each site as per design and verified they are consistent on both ends of the VPN. Now you need to verify the status of VPN tunnels if they are established successfully or not, which commands will give you full view of this?
- You have a traffic transiting from SRX firewall, but the traffic has no matching zone based policy or global security policy to allow such traffic. So in such case what will be the default behavior of SRX to treat such traffic?
- You have adopted the Juniper Unified threat management solution. As UTM is nothing but consolidation of various network security features, can you define briefly about the content filtering and web filtering features of UTM?
- You have been assigned a task to give access remotely to one of you internal server on a certain TCP port number so that the server is accessible worldwide. You only have one public IP configured on your SRX outside Internet facing interface and you are now supposed to re direct the traffic inbound from internet for this particular IP and customer TCP port towards the server. What kind of technology on SRX will be used to achieve this?
- As senior network engineer, you are troubleshooting two-way communication between your organization’s multiple departments. There has been a complaint from users of one department that they are unable to access some services from IT department particularly servers. In troubleshooting, you tested the communication between IT towards that department, and found no issue. However, when you did the same testing from the systems of impacted department, you realized it is not working. What could be the issue of this one-way traffic being working and not vice versa?
- You are working as network security expert and would like a very strong IT policy to harden your devices. Under such policy, you are supposed to select the remote access protocol, which shall be used by all network operations team. Which protocol would you go for and why?
- In IPSec you need to decide between AH and ESP protocols, but before doing that you must have clear understanding between these two protocols being used in IPSec. Define the basic difference between these two?
- You have connected two sites of your office with IPSec VPN. Your final goal is to make sure the local networks on both ends are able to communicate with each other. However when you ping from either side to remote end LAN it is not successful. What are the possible root causes for this issue?
- You want to have best security design in your network, which is redundant so that in case one firewall fails the other can take over seamlessly and traffic flow remains unimpacted. What feature would you use in such scenario?
- Juniper offers a great solution to manage its devices like switches, firewalls etc. and that too from cloud. Using such solution, you have control and flexibility to deploy, configure and manage the switches and firewalls. Can you name this solution?
- Explain basic difference between stateful and stateless firewalls?
- Which type of NAT is used when you want to hide the IP address while entering from one network to another network? Alternatively, maybe you need to do this because you cannot provide full end-to-end routing and so NAT has to be used to reach to a certain network.
- Explain some basic concept about the NAT Traversal and where is it needed?
- Which Juniper Security Network Management Tool custom make for threat management and policy management is available and is highly recommended to be integrated for Network Security Operations?
ANSWERS @https://ipwithease.com/shop/
Check our new website https://networkinterview.com For Free Video Courses, TechBlog, Mindmaps, Cheatsheets and much more.
ABOUT THE AUTHOR

I am here to share my knowledge and experience in the field of networking with the goal being – “The more you share, the more you learn.”
I am a biotechnologist by qualification and a Network Enthusiast by interest. I developed interest in networking being in the company of a passionate Network Professional, my husband.
I am a strong believer of the fact that “learning is a constant process of discovering yourself.”
– Rashmi Bhardwaj (Author/Editor)

 ANSWERS @
ANSWERS @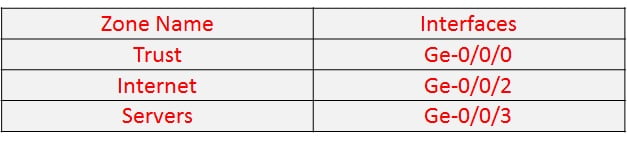 Mention the configuration you need to make such security zones?
Mention the configuration you need to make such security zones?