In this blog, we will go through the important Cisco FTD Interview questions to help you crack your next interview.
Cisco Firepower Threat Defense is a software developed by Cisco that combines firewall, IPS, VPN, and advanced threat protection capabilities into a single platform. It is designed to provide comprehensive security for networks, integrating features from Cisco ASA and NGFW capabilities.
ANSWERS @https://ipwithease.com/shop/

List of Cisco FTD Interview Questions
Q.1 What does FTD and FMC stand for?
Q.2 What is the usage and purpose of FMC?
Q.3 Please elaborate the difference between a prefilter rule and an access rule?
Q.4 Can ASA 5500-X Series have the NGIPS SFR?
Q.5 Where can you install and run the SFR in ASA?
Q.6 In order to reimage ASA 5506-X hardware to FTD, what is the correct order?

Q.7 To verify if SSD is installed on ASA hardware, which command should be executed?
Q.8 In which component of Firepower 4100 Series is FTD software installed?
Q.9 Which interface on an ASA device is assigned with an IP address during FTD software initialization?
Q.10 When selecting the type of traffic, if mgmt is selected then what would be the result?
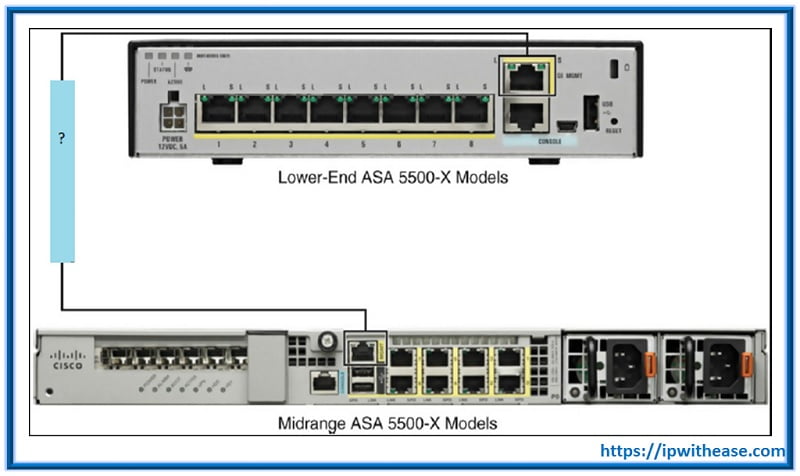
Q.11 Which interface is shown as “?” in lower-end and midrange ASA 5500-X series models?
Q.12 What is the name of the Mgmt interface which CLI shows, when connected to Firepower Code and when connected to ASA code?
Q.13 Which command is used in FTD to view the statistics of events inside the encrypted tunnel between FTD and the FMC?
Q.14 Which command confirms whether FTD is registered with the FMC?
Q.15 Which command is used to configure a manager in an FTD?
Q.16 What are the capabilities of the Firepower in terms of Licenses?
Q.17 Describe the usage and functionality of Base and Threat Licenses?
Q.18 Describe the usage and functionality of Malware and URL Filtering licenses?
Q.19 If we go to the System > Licenses > Smart Licenses page, we see Evaluation Mode button. What is the time period of the evaluation mode?
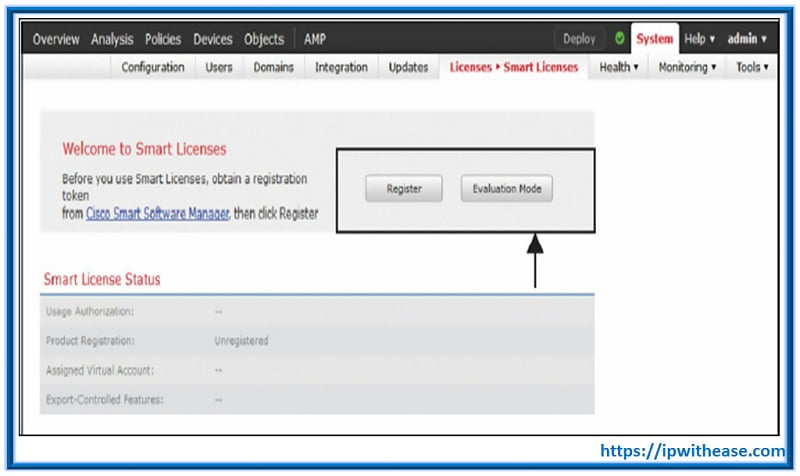
Q.20 What happens when we turn on the Evaluation Mode on the Firepower System?
Q.21 What is the workflow to Purchase, Generate, and Apply a Smart License in Firepower System?
Q.22 What is the behaviour of FTD when it is deployed in a Routed Mode?
Q.23 If you want to install FTD Version 6.1 on Firepower 9300 appliance having FXOS Release 1.1.4, what is the correct order of action?
Q.24 Which file can be deployed directly into an ESXi host if we are installing/running FMC?
Q.25 Which command syntax would be correct, if we want to ping test from FTD to the FMC?
Q.26 Which port does the Firepower System use for management communication by default?
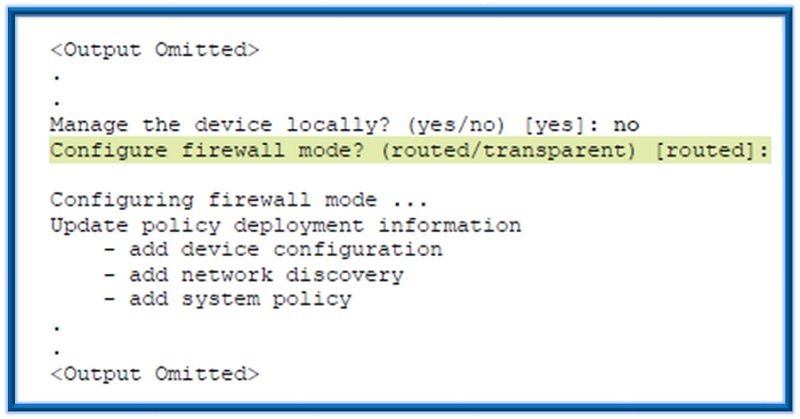
Q.27 If we hit enter in the highlighted prompt, what would be the default firewall mode?
Q.28 In below snippet, when registration with the manager is completed, the IP 10.1.1.16 is of which device?

Q.29 Which command is used to configure FTD from Transparent Mode to Routed Mode?
Q.30 What is the behaviour of FTD when it is deployed in a Transparent Mode?
Q.31 In what mode firewall is configured in below snippet?
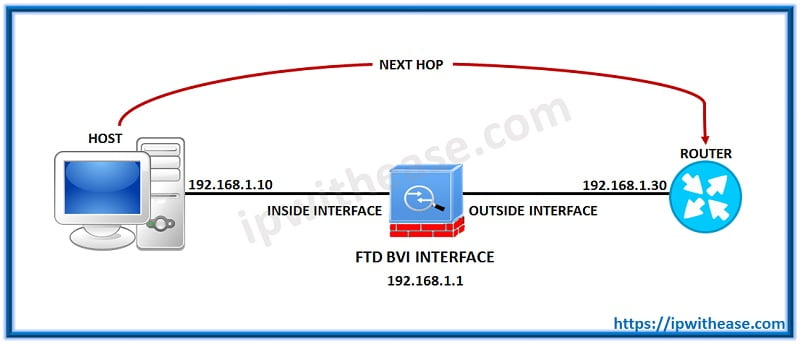
Q.32 In what scenario do Gig interfaces and BVI interface have same IP?
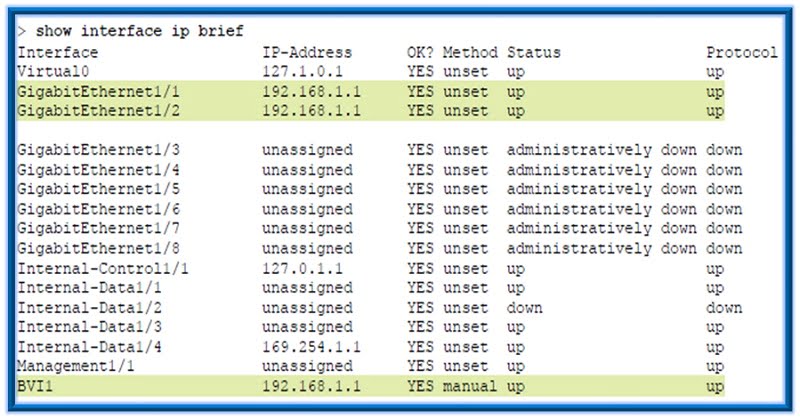
Q.33 Which command provides an overview of the various components of an inline interface set?
Q.34 What is the first-level-defense mechanism implemented on Firepower Engine?
Q.35 Which directory stores the filed related to DNS Policy?
Q.36 Which licenses are necessary to block a URL based on its category and reputation?
Q.37 Which type of analysis requires a connection to the cloud?
Q.38 Which base policy enables the largest number of standard text Snort rules by default?
Q.39 Which NAT section has highest priority during rule evaluation?
Q.40 After you deploy a new NAT policy, if a connection still uses a rule from the prior version of the NAT policy, how could you ensure that FTD will use the new policy?
Q.41 What is Security Intelligence?
Q.42 What is the function of Network Analysis Policy?
Q.43 What is the function of Intrusion Policy?
Q.44 What is Access Control Rule Monitor Action?
Q.45 What is Access Control Rule Trust Action? What is Access Control Rule Blocking Actions?
Q.46 What is Access Control Rule Interactive Blocking Actions?
Q.47 What is the function of Network Discovery Policies? What are 2 types of Network Discovery mechanisms?
Q.48 What is the purpose of Firepower Recommended Rules?
Q.49 How many connectivity models are there for network analysis and intrusion policies in Firepower System?
Q.50 Describe Balanced Security and Connectivity network analysis and intrusion policies?
Q.51 Describe Maximum Detection network analysis and intrusion policies?
Q.52 Describe No Rules Active intrusion policy?
ANSWERS @https://ipwithease.com/shop/
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj