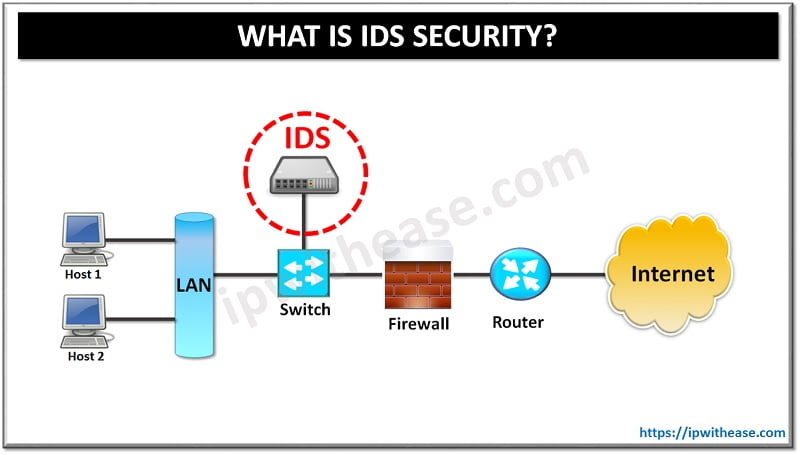
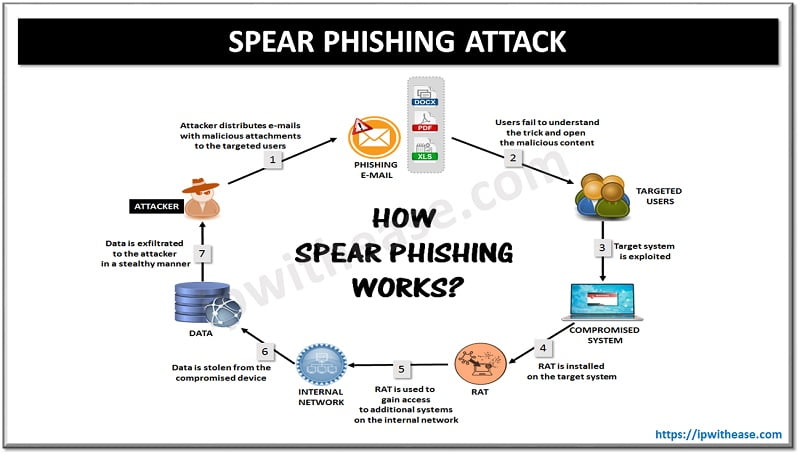
A smart network security administrator is the one that can gear up all the measures to neutralize threats even before they ever take place. In order to manipulate the events as per their scheme of things, the pros in the field of network security always keep certain decoy systems in their arsenal. One such popular decoy system that can function by enticing targets and misdirect the attackers from their real target are termed as honeypots.
Introduction
Honeypot can be made with a range of complexities on the grounds of what is actually required by your organization. Honeypot in network security can be a crucial line of defence and here we are going to focus on what different types of honeypots are, what are their benefits and how they are employed?
Honeypots help us in tracing an early sign of attack, what type of information is vulnerable, what are the details of the attackers and what are the methods used by them? Honeypots are well monitored and actually do not contain sensitive data. It helps in analysing TTPs (tools, tactics and procedures) of the attackers and accumulate legal and forensic evidence without putting the real network security at stake.
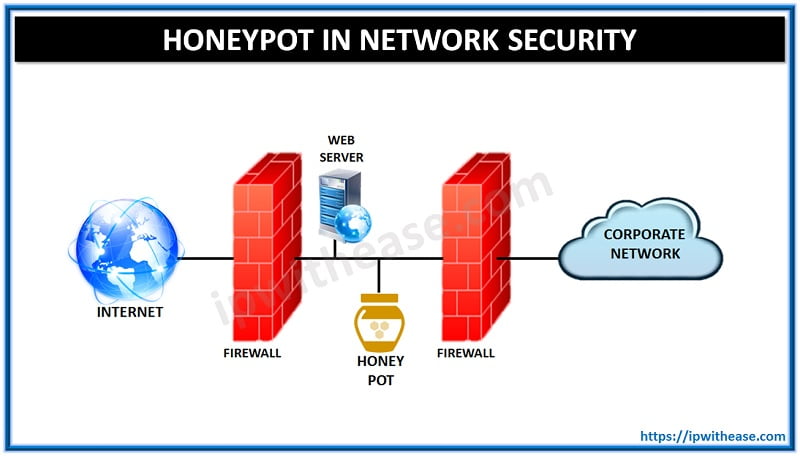
How a Honeypot Works?
In order to successfully execute a honeypot in network security, it is imperative that the entire system set-up seems like legitimate. There has to be certain dummy files in it to make it look important from the surface. The system security designers usually keep it just behind the corporate firewall. A honeypot is programmed to block the outgoing traffic, so that the hackers cannot use it as a checkpoint to redirect toward other internal assets.
In terms of functioning purpose, honeypots are classified into two types- research honeypots and production honeypots.
- Research honeypots are basically assigned to accumulate info on attacks and examine the malicious behaviour for the future pre-emptive measures.
- On the other hand, production honeypots primarily recognize the compromise on internal network security and subsequently tricking the invader.
As the job role indicates, research honeypots are more complex and carry additional forms of data files in comparison to production honeypots.
Honeypot Types
- Pure Honeypot: A full-scale production replication system that can run on different servers. It has comprehensive sensors and carry dummy “confidential” data and user details.
- High-Interaction Honeypot: It is used by the security analyst to observe attacker’s techniques and behaviour pattern. These types of honeypot are quite resource-intensive and demand more maintenance, but can deliver worthwhile findings.
- Mid-Interaction Honeypot: They do not possess own operating system, and primarily used to confuse the attackers in order to buy some time for the security team to react to the breach.
- Low-Interaction Honeypot: This form of honeypot in network security is widely deployed while creating a production environment. It is used for advanced warning spotting mechanism. They are quite simple to deploy and maintain.
Types of Honeypot Technologies
Some of the key honeypot technologies are as follow-
- Malware Honeypots: It is known to replicate and use attack vectors to identify malware. One example is Ghost USB honeypot meant to safeguard the machine from malware spread through USB.
- Spam Honeypots: It is used to simulate open proxies and mail relays. It detect and block the large quantity of spam emails dispatched by the spammers.
- Database Honeypots: It helps in creating decoy databases. These types of honeypots are effective against activities like SQL injections that frequently go untraced by the firewalls.
- Client Honeypots: It is helpful in tracing out malicious servers that are primarily responsible for attacking clients. It functions over virtualization technology and implement a containment strategy in order to curtail the risk imposed on the research team.
- Honeynets: It is a single system comprising of multiple honeypots in the network security. The purpose of the honeynets is to tactically track down the motives and methods of the attacker, simultaneously containing all sorts of outbound and inbound traffic.
The Benefits of Honeypot in Network Security
The following are some of the major benefits of a honeypot-
- Ability to break/ slow attackers down: The attackers while scanning your network always seek misconfiguration and vulnerable devices. An encounter with the honeypot renders you the chance to investigate and restrain the attack on time.
- Unambiguous in Approach: Honeypot does provide you with precise alert and location of the breach. It does help you out with identifying the loopholes as well as the invasion threat without scanning unnecessary locations and wasting the time.
- Easy to Install and demand low-maintenance: Modern honeypots are easy to download and install. They also require low-maintenance time and cost.
Conclusion
The presence of a strategically prepared honeypot in network system can enhance the level of security to a significant level. It is an undeniable fact that you cannot entirely depend on honeypots to formulate your threat detection strategy, but it delivers another layer of trusted security.
So the next time you devise a strategy to integrate honeypots to your network security systems, evaluate the types as mentioned above as per your need and incorporate a powerful weapon to your arsenal of ethical deception technology.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj