VLAN ACLs are often also referred to as VLAN access-maps. When we want to filter traffic from one VLAN to other and from one VLAN to other world we can use ACLs and several other methods.
But what if we want to filter traffic within the same VLAN. That is where the VLAN ACLs come handy and help us achieve this purpose.
Let us take the topology example as below –
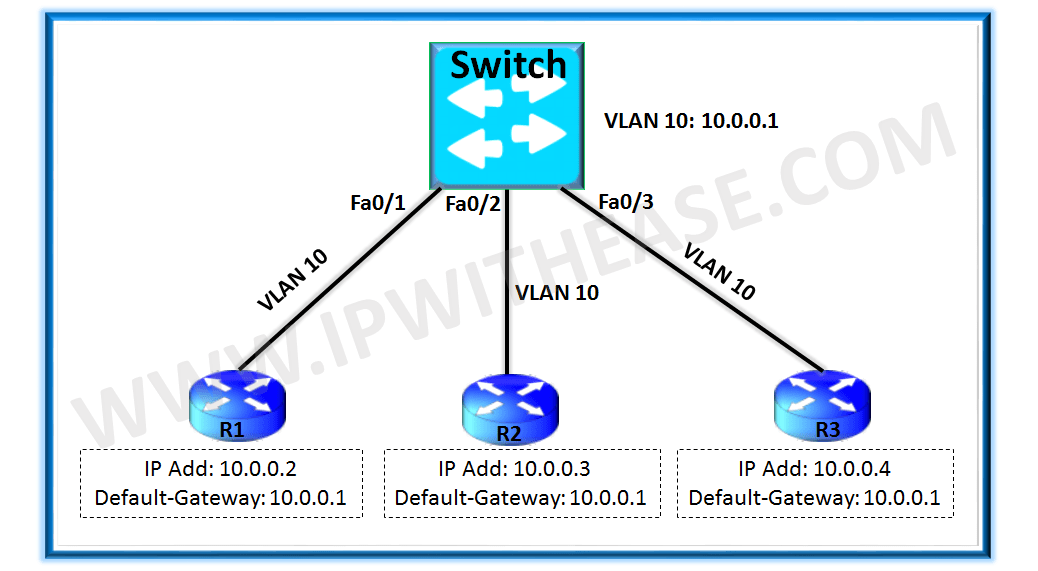
In the above topology all the Routers simulate the end-hosts and are on same VLAN 10. Switch is acting as a simple L2 switch with all the ports connecting to routers in same VLAN 10.
Switch Configuration
ip address 10.0.0.1 255.255.255.0
!
interface FastEthernet0/1
switchport access vlan 10
!
interface FastEthernet0/2
switchport access vlan 10
!
interface FastEthernet0/3
switchport access vlan 10
Initially we can ping from one router to another as all are in the same VLAN.
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 6/6/7 ms
R1#ping 10.0.0.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.3, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/2/5 ms
Now let us say we want to filter traffic within the same VLAN so that R1 and R3 aren’t able to reach R2. And to achieve this we will have to configure VACL as below on switch:
vlan access-map traffic-block 10
match ip address 101
action drop
vlan access-map traffic-block 20
action forward
Sequence number 10 will look for traffic that matches access-list 101. All traffic that is permitted in access-list 101 will match here. The action is to drop this traffic.Sequence number 20 doesn’t have a match statement so everything will match, the action is to forward traffic.As a result all traffic from any host to destination IP address 10.0.0.2 will be dropped, everything else will be forwarded.
Last step is to apply this ACL to VLAN in which you want to filter the traffic.
As a result the traffic from R1 & R3 to R2 will be blocked and dropped.
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.2, timeout is 2 seconds:
…..
Success rate is 0 percent (0/5)
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.2, timeout is 2 seconds:
…..
Success rate is 0 percent (0/5)
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj