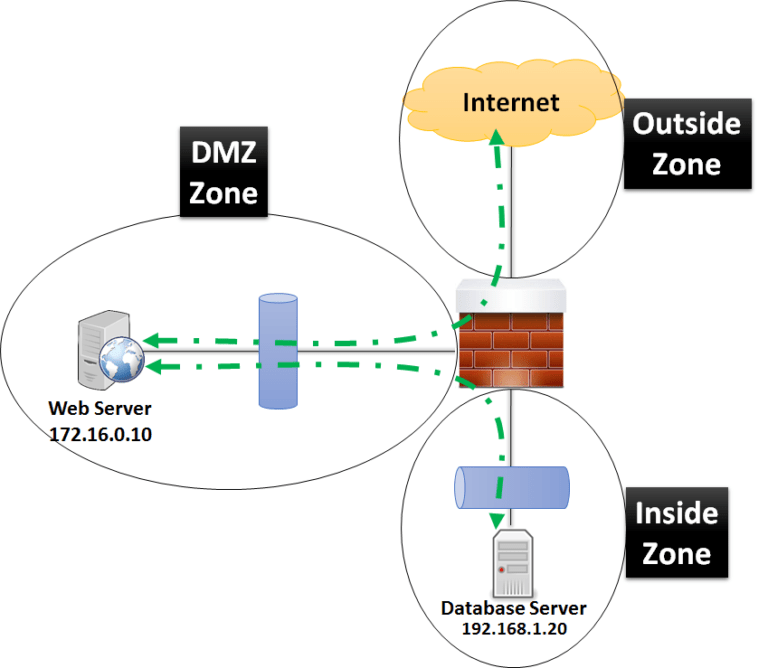
DMZ Cisco ASA
In the Cisco ASA firewall, there may be asked to have a customized configuration for communication across different assets across Security Zones. It’s imperative to share the default Security level Across Zones configured on Cisco ASA Firewall as below –
Outside Zone (Unsecured) = 0
Inside Zone (Secured) = 100
DMZ Zone (Semi Secured) = 50
Please note that more Secured traffic can send traffic to less secured zone however less secured zone to more secured traffic cant be possible and requires policy to be implemented on the firewall.
Related- ASA Firewall Security Guideline
Below is a scenario where we need to configure DMZ Zone server communication to Internet Zone and some selected IPs in Inside Secure Zone.
The key requirement of DMZ access is enlisted below –
- Web Server (in DMZ with IP 172.16.0.10) should have access to unsecured Internet over HTTP and HTTPS protocols only. Rest of the traffic should be blocked.
- DMZ Web Server should be able to reach SQL Server in inside network rest of traffic should be blocked.
STEP 1 –
Allow specific traffic from the DMZ to the inside.
STEP 2 –
Allow specific traffic from the DMZ to the outside.
access-list DMZ_WEB line 4 extended permit tcp host 172.16.0.10 any4 eq https
STEP 3 –
Block Everything else.
Related- Cisco ASA Firewall Interview Questions
Related- Single Site With Internet Only
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj