Table of Contents:
What is VRF?
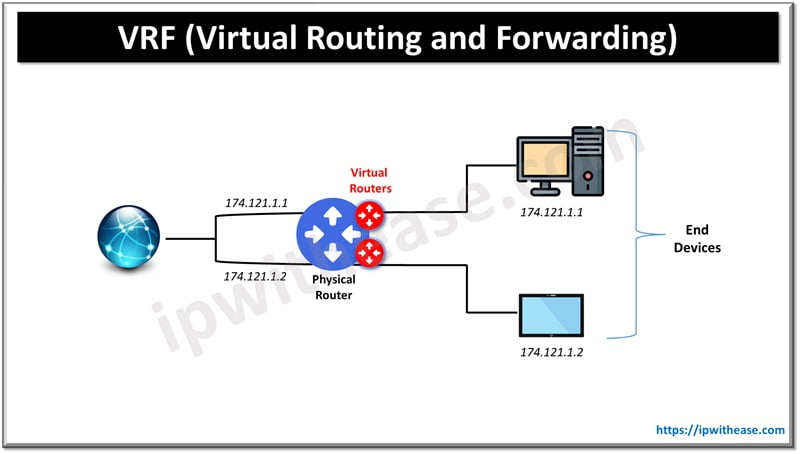
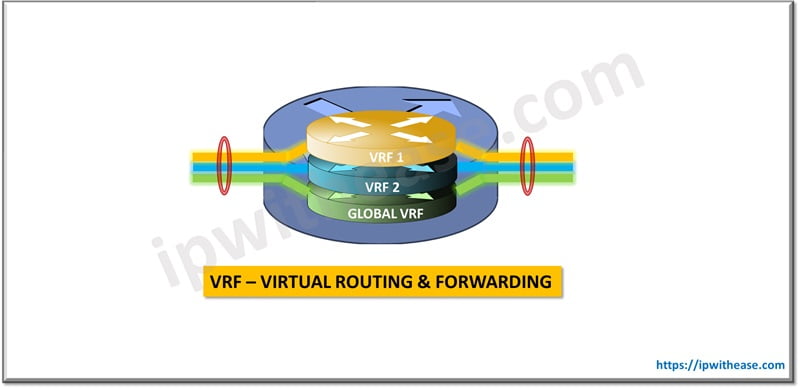
VRF (Virtual routing and Forwarding) is a technology that allows multiple instances of a routing table to co-exist within the same router at the same time. Because the routing instances are independent, overlapping IP addresses can be used without conflicting with each other.
The multiple Routing instances can be made to traverse different path (ie take different outgoing interfaces). VRFs are the same methods of network isolation/virtualization as VLANs.
Related – VLAN vs VRF
VLANs are used at the L2 and VRFs are L3 tools. VRFs are to routing table like VLANs are to LANs.
Using Virtual routing and forwarding we are virtualizing routing table into multiple routing tables, similarly to VLANs used to virtualize LANs.
One could say that VLANs are performing L2 virtualization, VRFs are performing L3 virtualization. VLANs make a single switch look like several switches; Virtual routing and forwarding make a single router look like several routers.
VRF Flavours: VRF and VRF Lite
VRF has earned so much popularity in recent years due to its versatility in Data Centers, Corporate LANs and most importantly in Service provider domain. While we talk about Service providers running MPBGP in MPLS Cloud, VRF is one of the key ingredient responsible for routing multiple customer traffic across the same underlying infrastructure.
VRF
Using VRF in provider MPLS domain increases network security and also allows segregation of customer traffic over WAN even in scenarios of overlapping address space. Considering the superb performance of VRF, its lighter version (VRF Lite) has been widely embraced in Data Center and Campus LAN environments.
VRF Lite
Unlike full-blown VRF, VRF Lite does not require configuration of MPBGP including some parameters like Route target etc. In fact, it is used in data centers to provide end to end segregation of traffic belonging to different zones likes DMZ, Extranet and Inside Zones.
Such an approach has drastically reduced physical infrastructure requirements by using different Logical Routing tables (thanks to VRF Lite). It segregates traffic of various traffic zones without the need for dedicated physical devices to perform these tasks.
VRF in Networking: How is VRF configured?
Below scenario will help us understand how virtual routing and forwarding or VRF works in networking and logically separate traffic for multiple customers by having multiple routing tables for each customer VRF.
Related – VRF Route Leaking
In the diagram, PE is the Provider Router connected on FastEthernet 0/0 to C1 and C2 Routers where C1 is customer 1 Router (Allocation under Vlan RED) and C2 is customer 2 Router (Allocation under Vlan GREEN).
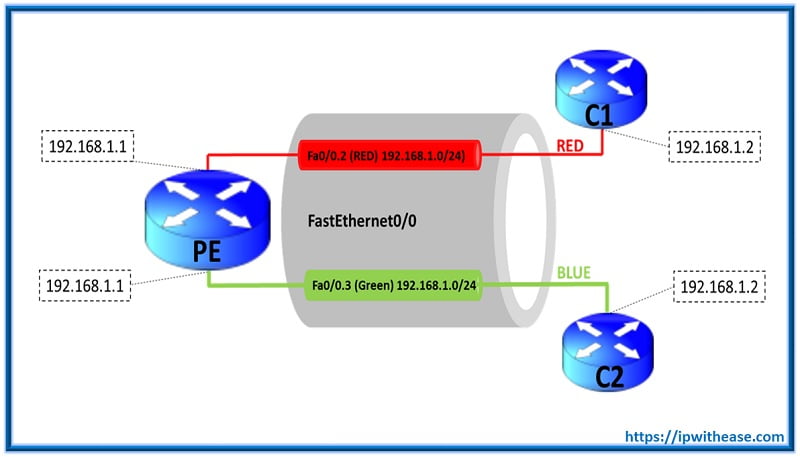
1st in order to configure 2 instances of Routing table (1 for the customer under RED instance and 1 for the customer under GREEN instance) we will allocate different VRF to both the customers and assign different RD values as below:
PE(config)#ip vrf RED
PE(config-vrf)#rd 2:2
PE(config-vrf)#ip vrf GREEN
PE(config-vrf)#rd 3:3Next, configure subinterface for both the customers. In this case fa0/0.2 for RED vrf customer and fa0/0.3 for GREEN vrf customer. Please note, the IP address at PE end for both the Virtual routing and forwarding will remain the same ie 192.168.1.1.
PE(config)#int fa0/0.2
PE(config-subif)#encapsulation dot1q 2
PE(config-subif)#ip vrf forwarding RED
PE(config-subif)#ip address 192.168.1.1 255.255.255.0
PE(config-subif)#int fa0/0.3
PE(config-subif)#encapsulation dot1q 3
PE(config-subif)#ip vrf forwarding GREEN
PE(config-subif)#ip address 192.168.1.1 255.255.255.0Now since the configuration is complete, let’s perform the connectivity test.
1st ping from Customer 1 Router towards PE IP address 192.168.1.1 (RED VRF)
2nd ping from customer 2 Router towards PE IP address 192.168.1.1 (GREEN VRF)
C1#ping 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 10/35/70 ms
C2#ping 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 10/35/70 msPing test from PE towards customer Routers
PE#ping vrf RED 192.168.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 10/35/70 ms
PE#ping vrf GREEN 192.168.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 10/35/70 msI hope I’ve explained myself well. The intent is to share the concept of VRF lite and its related terms in simple and easy to understand terms.
FAQs on “VRF Basics”
Q.1 What is the difference between VRF and VLAN?
VLAN is a group of ports that form a logical LAN segment. VLAN ports form an independent traffic domain in which the traffic generated by the nodes remains within the LAN. VRF feature allows multiple instances of IP routing table to exist in a layer 3 device and all routing instances working simultaneously. This allows network paths to be segmented without using multiple device. No license is required for VLAN creation.
VRF starts from IP base license and IP service in catalyst switches. While one VLAN can be part of only 1 VRF on same device, one VRF can have multiple VLAN assigned to it on same physical device. VLAN works on layer 2 of OSI model. On the contrary, VRF works on layer 3 of OSI model. VLAN can make single switch look like multiple switch and a VRF can make single router look like multiple routers. While VLAN is communicated between devices, VRF is local to router/switch.
Q.2 What is Multi VRF?
Multi-VRF is a feature that enables a service provider to support two or more VPNs, where IP addresses can overlapped among the VPNs. Multi-VRF uses input interfaces to classify routes for different VPNs and build a virtual packet-forwarding tables by assigning Layer 3 interfaces to each VRF.
Interfaces in a VRF can be either physical such as Ethernet/Gig ports or logical such as VLAN SVIs (Switched Virtual Interfaces), but a Layer 3 interface cannot assign to more than one VRF at any one time. The Multi-VRF feature allows to support more than one routing domains on a CE router with each routing domain having its own interface and its own set of routing and forwarding table.
Q.3 Where is VRF used?
VRF provides a way for you to configure multiple routing instances on router or Layer 3 Switch. The intent is to keep customer traffic and routing separate while using the common hardware. In scenarios where VRF is not used, customer routes are divided by using sub-interfaces or different physical interfaces and then ACL based filtering to separate the traffic.
This would certainly be one method of doing so however if for some reason you wanted to overlap customer addressing you’d have a serious problem. This is where VRF is very useful, which is capable of routing overlapping IP address on a router/L3 device at the same time.
Q.4 What is BGP VRF?
The Border Gateway Protocol (BGP) VRF feature provides additional control of the advertisement of routes and extends this control to within a virtual routing and forwarding (VRF) instance. This feature extends support for BGP VRF-aware conditional advertisement to the following address families
1. IPv4 unicast
2. IPv4 unicast VRF
3. IPv6 unicast and
4. IPv6 unicast VRF
Per-VRF assignment of BGP Router ID is the ability to have VRF-to-VRF peering in Border Gateway Protocol (BGP) on the same router. The router ID can be manually configured for each VRF or can be assigned automatically either globally under address family configuration mode or for each VRF.
Q.5 Is VRF secure?
Yes, VRF is pretty secure. A VRF instance consists of an IP routing table, a derived forwarding table, a set of interfaces that use the forwarding table and a set of rules and routing protocols that determine what permit/deny into the forwarding table. VRF technology allows the customer to virtualize a network device from a Layer 3 standpoint creating different “virtual routers” in the same physical chassis.
A VRF is actually not a virtual router because it does not have dedicated memory or I/O resources. VRF-lite and MPLS support are different that can be used to provide separate path isolation mechanisms (VRF-lite + GRE, MPLS VPN).
Q.6 What is difference between VRF and VRF Lite?
In VRF, traffic is isolated from source to destination network through the MPLS cloud which uses MPBGP in the service provider’s Cloud environment. RD and RT (Route Distinguishers and Route Targets) are designed for overlapping route segregation. VRF-lite is normally a VRF without MPLS and MPBGP. VRF Lite a subset of VRF.
VRF lite can be virtualizing network elements and various security zones inside data center or office LAN environment. This can be used if enterprise has networks of same IP addresses or some segments are required to traverse through network Firewall. VRF-lite configuration doesn’t require the route-target and can be provisioned by static or dynamic routing under its vrf instance.
Q.7 What is RD value in VRF?
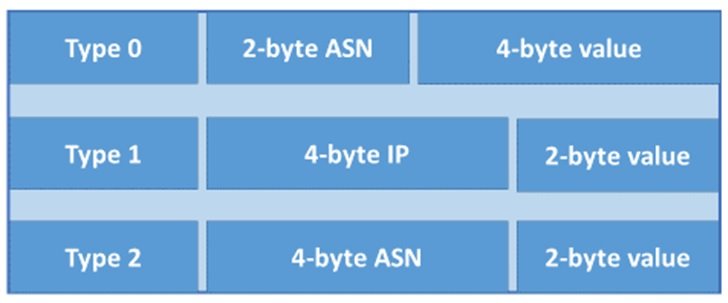
VRFs allow IP address space to be reused among isolated routing domains. Let’s assume three sites all of which are using same IP as their local network. Each customer has its own VRF so that the overlapped subnet are kept isolated from one another routing domains. This is where route distinguishers come in. A route distinguisher (RD) distinguishes routes from one another.
A unique number is prepended to each route within a VRF to identify it as belonging to that customer. An RD is inserted with a route via MP-BGP when exchanging VPN routes with other PE routers. An RD is a 64-bits in length contains three field types (two bytes) administrator and value. There are three defined formats which can be used by a provider.
Q.8 How do I create a VRF lite?
Below is the 2 step process of creating a VRF Lite and assigning the same to an interface –
1. Creating the VRF instance
Hostname(config)#ip vrf name
2. Assigning VRF to an interface
Hostname(config)#interface name
Hostname(config-if)#ip vrf forwarding name
Hostname(config-if)#ip address X.X.X.X X.X.X.X
Hostname(config-if)#exit
You Can watch This Video For Better Understanding
To Understand more about What is VRF & understand more concepts of VRF in Networking watch our Video: