Table of Contents
Email communications are one of the major sources of cyber threats. Hackers impersonate legitimate mail servers and act as authorized sources to send emails on behalf of a domain. This leads to email spoofing attacks.
The From address is forged to appear as if it is coming from a legit domain in an email spoofing attack. The use of DNS SPF records prevents this kind of attack as it is a way to authorize email communication which helps senders and email recipients from phishing, spoofing and spam attacks.
The domain SPF record is verified by DNS SPF to ensure if the server is authorized for sending emails.
In this article we will learn more in detail about the DNS SPF record, its working, mechanisms, qualifiers and an example SPF record.
What is DNS Sender Policy Framework (SPF) Record
As email spam continues to grow as a major problem for many of the organizations. Organizations do deploy spam filtering or blocking measures but they also consider strategies to prevent spammers from using your domain names for sending spoofed emails. The spoofed emails damage the credibility of the company’s domain and adversely impact the organization brand image.
DNS sender policy framework (SPF) is utilized by large email providers such as Google Gmail, Yahoo mail, AOL etc. to check sender policy framework (SPF) records to verify sender domain legitimacy.
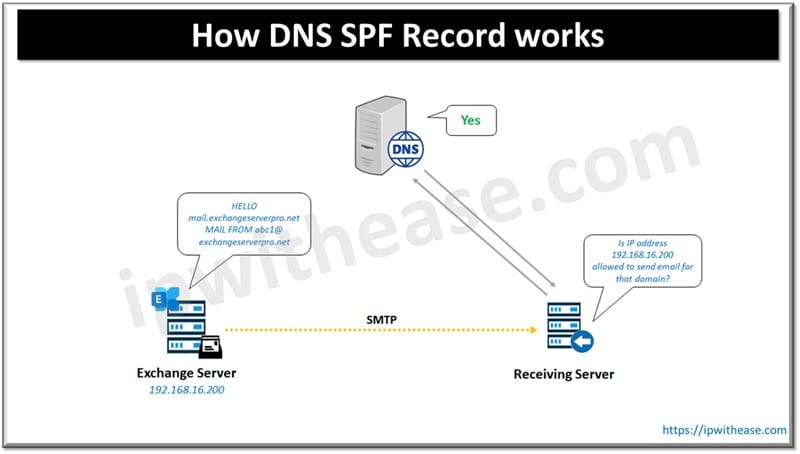
Working
Domain owner is authorized by DNS SPF record to define mail servers which are authorized for sending emails for specific domains. In SMTP conversation, sending server issues ‘MAIL FROM’ command and receiving server checks SPF domain record in domain name ‘MAIL FROM’ email address to ensure source IP address of SMTP connection matches.
SPF records a text record with specific syntax. The syntax of SPF record is made into two parts – modifiers and mechanisms. Modifiers are not used commonly and optional except in special. Mechanisms are mostly used by SPF records. The mechanism defines a set of hosts which are authorized to send email from domain.
Mechanisms are used in conjunction with qualifiers which tell the server what to do in case an event match is found.
Mechanisms
- All – means matched any host and placed at the end of SPF record for any senders which did not match other mechanisms listed before all.
- IP4 – means match a single IPv4 address
- IP6 – means match a single IPv6 address
- A – means match host or domain name
- Mx – means match with mx records for domain
- Ptr – means match sender ip address to host name using reverse DNS query not recommended usually due to DNS load issues
- Exists – means if domain name exists in DNS record
- Include – means sender ip address is matched with SPF record of another domain. Used during outbound email routing via cloud service
Qualifiers
- ‘+’ pass result and default setting with no qualifier means message must be accepted
- ‘-‘ for hard fail and indicates reject email from authorized hosts
- ‘~’ for softfail – mail is accepted as likely spam and result is not definitive
- ‘?’ for neutral which means it neither failed nor passed the test and you can either accept it or reject it
Example of an SPF Record
An SPF record looks like
v=spf1 a include:_spf.microsoft.com -all
Where,
v=spf1 – is SPF version
a – In A record detected host is authorized to send emails
include: - authorize emails which sender sends on behalf of domain (such as microosoft.com)
-all – addresses not listed in SPF record are unauthorized to send any emails and should be rejectedContinue Reading
How to Configure Cisco Router as DNS Server
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj