Table of Contents
As technologies are advancing, so are cyber-attacks. Gone are the days when poorly worded emails used to be the base of phishing attacks. The attacks are more mature and sophisticated and it is difficult to assess and identify their potential impact and damage they will cause if they get exploited.
It is important to be aware of the latest threats and how they are used to con their targets – humans and systems.
Today we look more in detail about Watering hole attack technique, what are these types of attacks, how it works, how to prevent water hole attacks etc.
Understanding Watering Hole Attack
Watering hole attack as the name suggests is based on a nature phenomena where animals gather around a water patch in the forest to be unknowingly surrounded by their predators in the food chain. Waterhole phishing is an advanced form of phishing which works on the basis of trust.
Cybercriminals study their target to understand and analyze patterns in user web browsing habits, what websites and applications they visit frequently. Once the website or application used by the target is identified, malware is installed on it. The website becomes a point of distribution where both website owner and targeted victims are unaware. For example, a newly joined employee is looking for more information on industry and visits a trade publication, the site is infected with malware via their flash player. This style of attack is very effective and many bigger players such as Microsoft, Apple, Facebook have fallen prey to it.
Cybercriminals used the data normally collected to assess behaviour as an organization and its employees. Usually marketing firms with general intent to provide better products, services and experiences collect this kind of data. Once cybercriminals get hold of this data, it provides a map of what websites are permitted for employees to visit and whitelisted by organizations. Using this approach cyber criminals get hold of data they require for targeted phishing without much research.
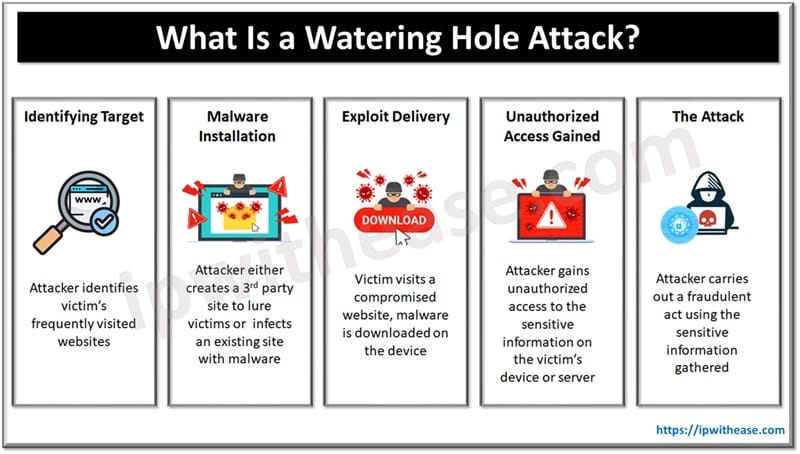
How does the Watering Hole Attack work?
Let’s look at the process of watering hole attacks more in detail.
- Finding target – Usually targeted towards an organization, size is not important here only the data
- Identity Frequently Visited Websites – Cybercriminals use data gathered by marketing companies to understand organization and its employee’s behaviour. These companies provide data related to customer analytics such as Chartbeat, Woopra, Statcounter and so on. Cyber criminals leverage services of these firms to gather the data they want to use in targeted attack
- Installation of Malware – The cybercriminal creates similar websites as legitimate websites, fraudulent websites or find vulnerabilities in existing sites their victims frequent and compromise them with malware.
- Vulnerability Scans – When a user visits a compromised website, code is downloaded in background which performs a vulnerability scan on the target system. The vulnerability it looks can be in operating system, browser, added plugins, flash, Silverlight, java, or any other common software
- Exploit Delivery – If there are open vulnerabilities on target system then exploit is delivered in background
- Greater Attack or Theft – With the privileges associated with targeted user, cyber criminal can have access to confidential data, intellectual property, or capability to place malware into source code.
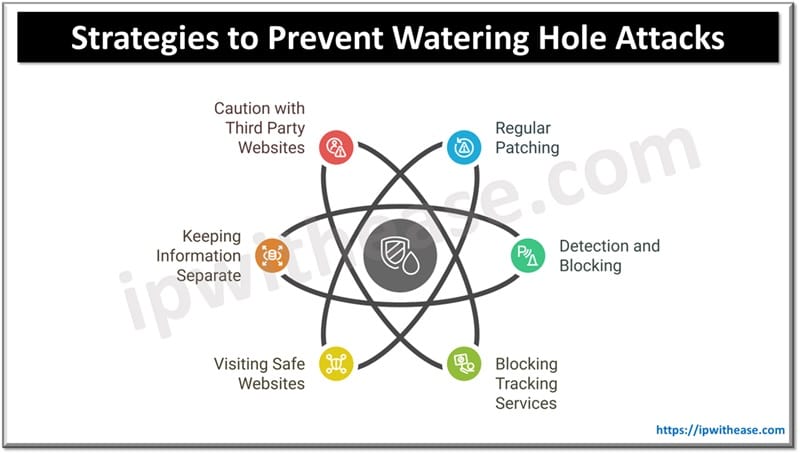
How to Prevent Watering Hole Attacks?
- Regular Patching of Exploitable Vulnerabilities – Watering hole attack can be successful only if a system has some exploitable vulnerabilities. To ensure complete protection ensure that your system has the latest patches installed and keep your software and browser up to date.
- Detection and Block Capabilities – Detection of abnormal activity and its tracking is important. If a system detects abnormal behaviour it needs to respond quickly to malicious activity based on severity.
- Blocking Tracking Services – Blocking tracking services on web browsers help to ward off cybercriminals from systems
- Visit Safe Websites – Only visit secure websites having HTTPS in the URL
- Keep Work and Personal Information Separate – Keep work and personal information separately on different drives or systems
- Be Careful with Third Party Websites – Third party websites which are not operated or controlled by trusted entities and usually a common target of cyber criminals. Only access websites by search and avoid clicking links that come in email etc.
Some Watering Hole Attacks Statistics
Year 2023 – ClearSky have discovered watering hole attack targeting multiple Israeli websites using jQuery
Year 2021 – The “Live Coronavirus Data Map” from the John Hopkins Center for Systems Science and Engineering is used to spread malware
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj