Table of Contents
Introduction
Whaling Phishing is a highly dangerous phishing attack initiated by hackers that targets mostly senior executives and looks as an ordinary legitimate email. Whaling Phishing is described as a digitally enabled fraud through social engineering, designed to encourage user victims to perform a secondary action, such as initiating a wire transfer of funds.
Although Whaling Phishing does not require extensive technical knowledge, it has the advantage of delivering huge returns. This is one of the biggest risks that online business is facing at the moment. Financial organizations and payment services are the most targeted victims. Interestingly, cloud storage and file hosting sites, online services and e-commerce sites are receiving a huge share of attacks as well.
The main strategy of Whaling Phishing emails is highly sophisticated compared to the generic phishing emails, because they often target chief (C-Level) executives and usually contain personalized information about the targeted organization or individual. These kind of emails may also convey a sense of urgency and are usually crafted with a solid understanding of business language and tone.
Whaling Phishing Techniques
As investigated by scientists and engineers and the following three techniques are mainly used:
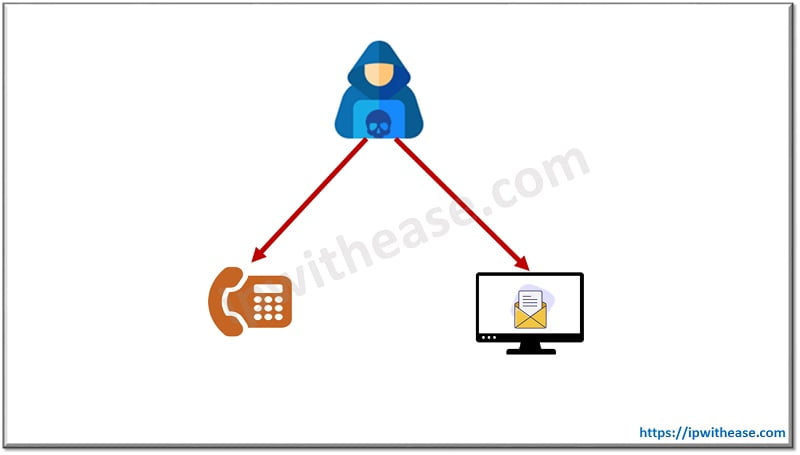
- Whaling Fishing Email with A Phone Call: There have been several incidents reported, where by a whaling phishing email was first received and then followed by a phone call that confirms the initial email request. This is mainly a social engineering technique which could be best described as cyber enabled fraud attack. In this case, the phone call serves the dual purpose of corroborating the email request and making the victim weak from a possible cyber-attack.
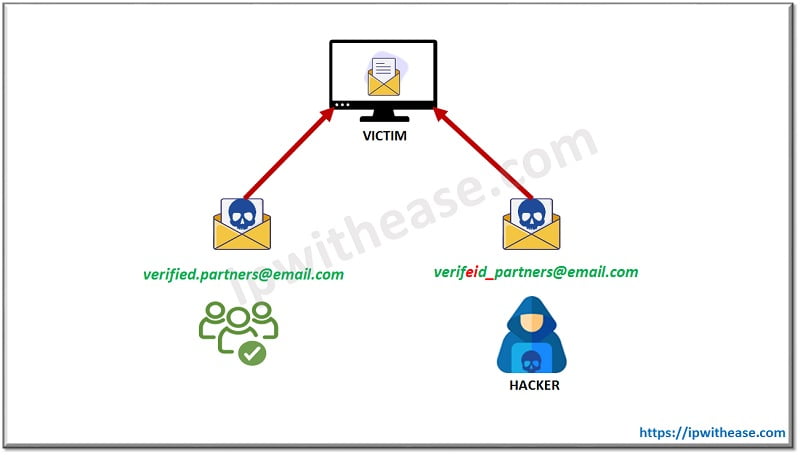
- Whaling Fishing Email from Malicious Actors: The increase of supply chain attacks (where a supplier or partner organization’s network is compromised in order to gain access to the target area) has been well documented. However, recent whaling attacks have used easily accessible information on suppliers or partners to create whaling emails which look legitimate. If an organization advertises partners such as charities, law firms, policy institute or academic, they should be aware that they may receive emails from malicious actors disguised as the trusted partners.
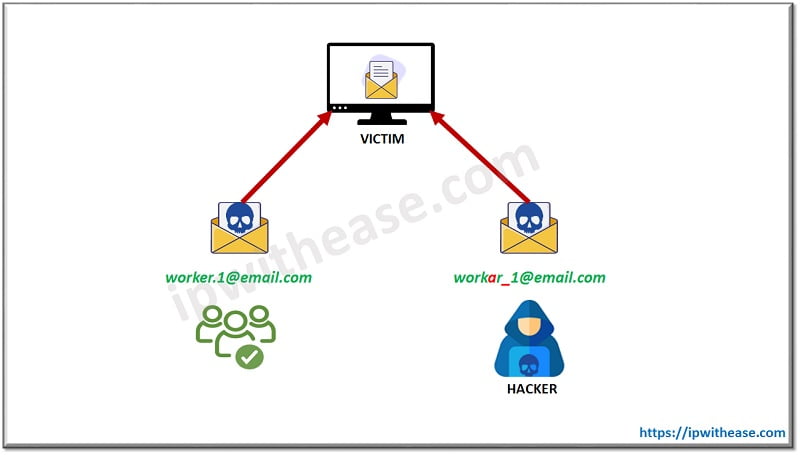
- Whaling Fishing Email from Colleagues: In this case an employee’s email address is either compromised (or a spoofed email address is used) to convince other employees, that they are going to receive a legitimate request from a colleague. This is especially effective when the email address of a senior executive is spoofed to request an urgent payment for a junior member of (for example) a finance organization.
- Whaling Fishing through Social Media: Nowadays, Social media networks are being used increasingly for developing business contacts, recruiting employees and hosting conversations. However social media accounts, both professional and personal, provide a method for malicious actors to investigate and make contacts with senior executives. They provide a legitimate source of information for social engineering.
Consequences of Whaling Phishing
The two main disadvantages of being a victim of a Whale Phishing attack are the following:
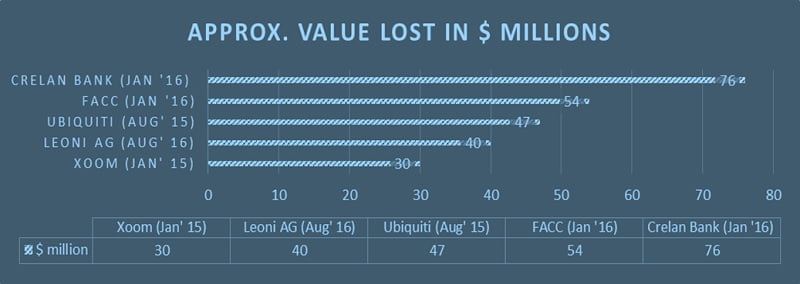
- Financial Loss: The Intelligence report by PhishLabs, reveals that 22% of whaling phishing attacks analyzed in 2015 were motivated by financial frauds. As shown in the table below, there is an illustration of the top five of the largest financial losses to organizations, were from fishing emails. According to these examples, a senior executive received a fraudulent email request to transfer funds.
- Reputational Loss: Financial or data loss because of a whaling phishing attack can be extremely embarrassing to both an organization and an individual as well. FACC, an Austrian aerospace manufacturer, lost €50 million from a targeted whaling phishing email attack in 2016. Then he decided to fire many employees including the CEO, for their involvement in the incident.
Conclusion
The innovative and increasing use of the Internet, technology devices and smart cities have also presented huge opportunities to cybercriminal attacks. It is becoming imperative to balance, the use of the insecure Internet in our daily lives with new age devices. Therefore if we need to securely communicate with others and realize the advantages of these technologies without being exploited by whaling phishing attacks
Continue Reading:
Top 5 Data Breaches in Cyber Security
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj