Table of Contents
Large volume of data and information flows electronically and maintained in house or on cloud infrastructure. Data at rest or in transit is susceptible to sniffing, leakage, theft etc. Encryption technique enables organizations to secure data which we send, receive and store. Businesses uses encryption due to multiple security requirement such as confidentiality, integrity, and availability of data. Objective of encryption is to protect stored information and protect information from unauthorised disclosure.
In this article we will learn more encryption techniques, how encryption works and its advantages.
What is Encryption?
Encryption encodes information in such a manner that it becomes unreadable by anyone aside from its intended receiver. Encryption technology converts and ordinary text which could be an email, message, record into ‘cipher text’. The cipher text is converted back to readable format post reaching its destination. This conversation into readable format is also referred as ‘decryption’. Some common encryption tools/software available in the market are Folder Lock, LastPass, BitLocker, VeraCrypt, File vault2, 7-zip etc.
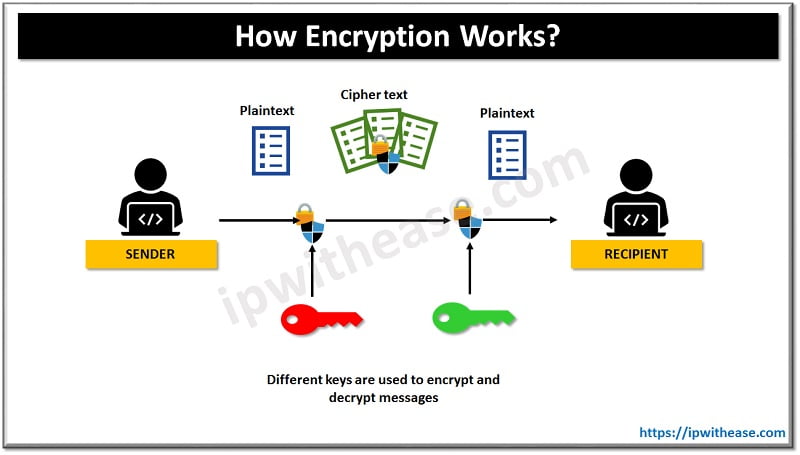
Passwords are a standard part of online life and in many businesses, the necessity for passwords to access various applications creates a headache for system administrators. Tools like zero trust security help by ensuring continuous identity verification, but using encryption is essential.
Encryption techniques
Sequence of numbers used for encrypting and decrypting data is an encryption key. Keys are algorithm based and these are random and special for each key (unique). There are two widely used encryption techniques – Symmetric and asymmetric.
Symmetric Encryption
Symmetric encryption is based on a single password or key. Symmetric keys are 128 or 256 bit long. The secret key is possessed by sender and receiver which are communicating. RC4, AES, DES, 3DES and QUA uses symmetric key encryption.
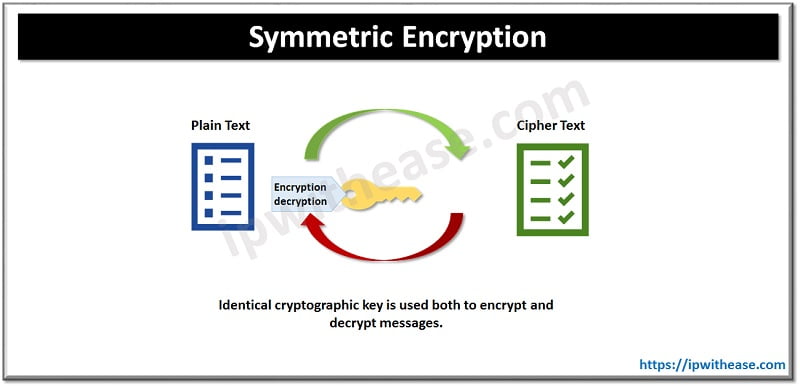
Pros and Cons
Pros
- Ease of use and faster suitable for bulk transfers.
- Determining patterns and guessing decryption key is easier.
Cons
- Anyone with key can decrypted message which is not intended for them.
- Suffers with key management problem as keys need to be protected from unauthorized users.
- Non-repudiation keys are subject to interception.
- It provides limited security.
Asymmetric Encryption
Asymmetric encryption is based on two keys. Public key which is known to everyone who wish to send a message and private key is kept securely with the owner of the public key. Asymmetric algorithms are more complex in nature and slow to execute due to maintaining a pair of two keys. These are usually 1024 or 2048 bit long. RSA, Diffie-Hellman, ECC, El Gamal, DSA uses a symmetric encryption.
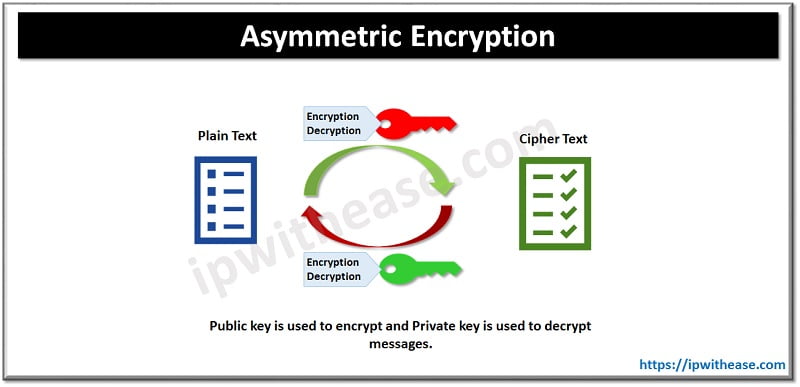
Pros and Cons
Pros
- No need for key exchange hence key distribution problem is eliminated.
- More secure as private keys are not transmitted or handed over or revealed to anyone.
- Digital signatures enable recipient to verify message is come from a legitimate sender.
- Non-repudiation is permissible hence sender can’t deny sending a message.
- Provides five elements of security – confidentiality/privacy, access control, authentication, data integrity, non-repudiation.
Cons
- Computationally intensive and slow hence not suited for bulk message decryption.
- Message can’t be decrypted if private key is lost.
- Public keys are not authenticated so no one really knows public key belongs to specific person.
If hacker gains access to private key all individual messages can be read.
Types of Encryption
There are various types of encryptions available some most common types of encryptions are described below.
- Data Encryption standard (DES) is a low-level encryption it was developed in 1972 by IBM but never approved for national security applications. It is a 64-bit plain cipher. DES is largely redundant now due to advancements in technology. It is a block mode cipher in which message is broken down into blocks and encrypted discretely
- Triple DES is an improvement over DES standard, and it works 3 times the normal DES standard. It first encrypts data, decrypts data and then again encrypts data.
- RSA stands for Ron Rivest, Adi Shamir, and Leonard Adleman— three scientists who first publicly explained the algorithm in 1977. RSA utilizes a common and strong algorithm and commonly used for safe transmission of data.
- Elliptic curve cryptosystem (ECC) is highest strength / bit public key stream, big savings in terms of computation, bandwidth, and storage over other Public key systems.
- Advanced Encryption Standard (AES) is US Government standard since 2002 and widely used and it is based on Rijndael algorithm and operates on single private key
- Blowfish is used as a replacement for DES it uses symmetric block cryptography. It is publicly available without any cost
- Two fish is a quick encryption algorithm and usable in hardware and software and it is Pre-shared key encryption technique and modern form of Blowfish encryption
- Format preserving encryption (FPE) is used to secure format of data it is majorly used by banking , audit firms and retail systems etc.
Internet primarily uses HTTPS protocol which means communication between web browser and web server is encrypted in both sides. HTTPS uses Secure Socket layer (SSL) security technology to create an encrypted link between a server and a client. SSL handshake uses both symmetric and Asymmetric encryption.
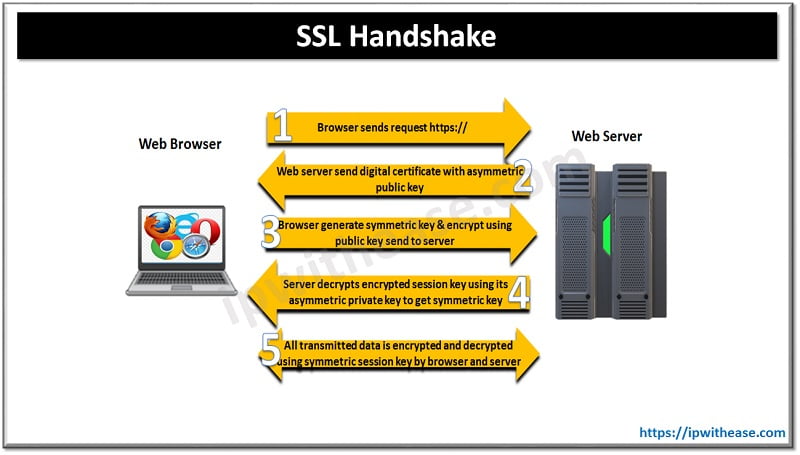
The steps are outlined as under:
- Browser send an HTTPS request
- Web browser sends a digital certificate with asymmetric Public Key
- Web browser generates a symmetric session key and encrypts using is public key and sends to server
- Server decrypts the encrypted session using its asymmetric private key
- All transmitted data is encrypted and decrypted using symmetric session key by Server and web browser unique for that session only.
Major challenges to encryption are brute force attacks or attempting random keys until right one is identified, side channel assaults and cryptanalysis provides alternate means to crack ciphers.
Quick Tip!
Global encryption software market size valued at USD 4.0 billion in 2020 which is expected to grow USD 8.7 billion by 2025.
Continue Reading
Network Vulnerabilities and the OSI Model
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj