What is a Proxy Server?
A proxy server functions as a middleman for requests from customers trying to access data from other servers.
A customer links to the proxy server to ask for a service that is available on another server, and the proxy server examines the request to reduce and control its complexity.
Forward Proxy
Forward Proxy takes origin connections from the intranet clients and connect them to servers outside on the internet. In other words, A forward proxy takes requests from an internal LAN network and forwards them towards the Internet. Sometimes, forward proxy may even serve the requesting client with cached information rather than passing the request towards the internet.
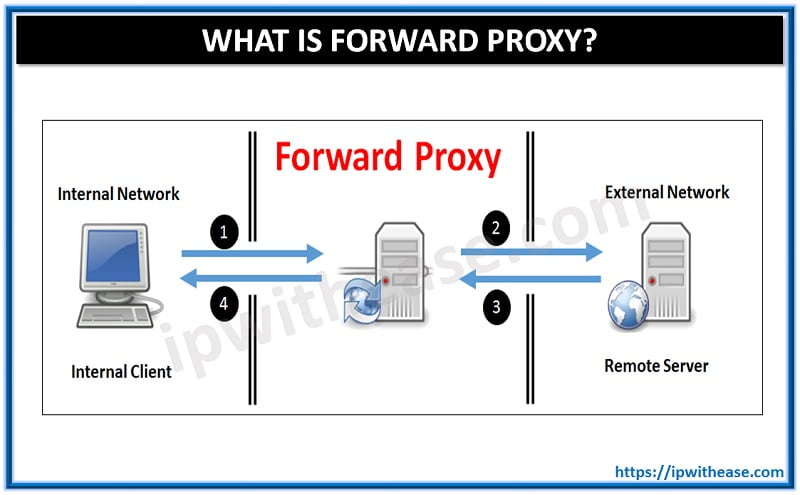
How does Forward Proxy work?
- The proxy server works as an intermediary between the user and the internet, fulfilling the user’s requests and relaying the corresponding response back to them. All the information is transmitted through the proxy server when it is set up in this manner. The user’s device is connected to the internet using the proxy server, which implies that each request made by the user’s device is routed through the server.
- Once the requests are received by the Forward proxy server, the proxy server carries out a few regulations that have been set by the organization’s administrators. Companies might implement a range of policies including prohibiting access to particular sites, verifying the IP address of users, preventing the use of personal email accounts, limiting access to certain materials, and safeguarding confidential data.
- After the forward proxy has gone through all the regulations, it will either grant or deny the user’s request based on the company’s policy. If the request is approved, the proxy will send it on to its intended location.
- The endpoint can either be on-premise service of the company or cloud service. When the request reaches the endpoint, the service will produce a response and send it to the proxy server.
- At this point, the proxy server can perform additional authentication, such as eliminating malicious reactions. It can also pass the answer through additional filters set by the administrators, and if all checks are successful, the response is sent back to the user’s device.
Forward Proxy: Tasks Performed
In the general scenario, forward proxy performs following tasks
- Check for validity of request from LAN (based on configured parameters).If rejected, the client is supplied with error message.
- If above request if accepted, forward proxy looks in cache for requested information. If information is available in cache, it is served to the client.
- If no cached information is available, the proxy sends request to destination Content server and further relays the required data to the end client. The information is stored in cache for future reference.
Benefits of a Forward Proxy
- User Privacy: A forward proxy works as an intermediary between a user’s device and the public internet. It creates requests on behalf of the user, providing a layer of protection for the user’s privacy.
- Traffic Visibility: All traffic on the web passes through the forward proxy, which gives insight into how the establishment makes use of cloud technology, programs, and additional external services.
- Policy Enforcement: When using a forward proxy, all web traffic generated by the company passes through the proxy. This enables the proxy to examine the requests and replies and enforce corporate policy and usage regulations.
- Shadow IT Detection: Equipment that has not been given the go-ahead by the IT department, otherwise known as “shadow IT,” generally transmit information to outside cloud-based services. A forward proxy can recognize this kind of communication and use it to detect any unapproved gadgets connected to the corporate network.
Forward Proxies Use Cases
- Content Filtering
- eMail security
- NAT’ing
- Compliance Reporting
Continue Reading:
PROXY vs NAT – Understand the Difference
VPN vs Proxy: Detailed Comparison
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj